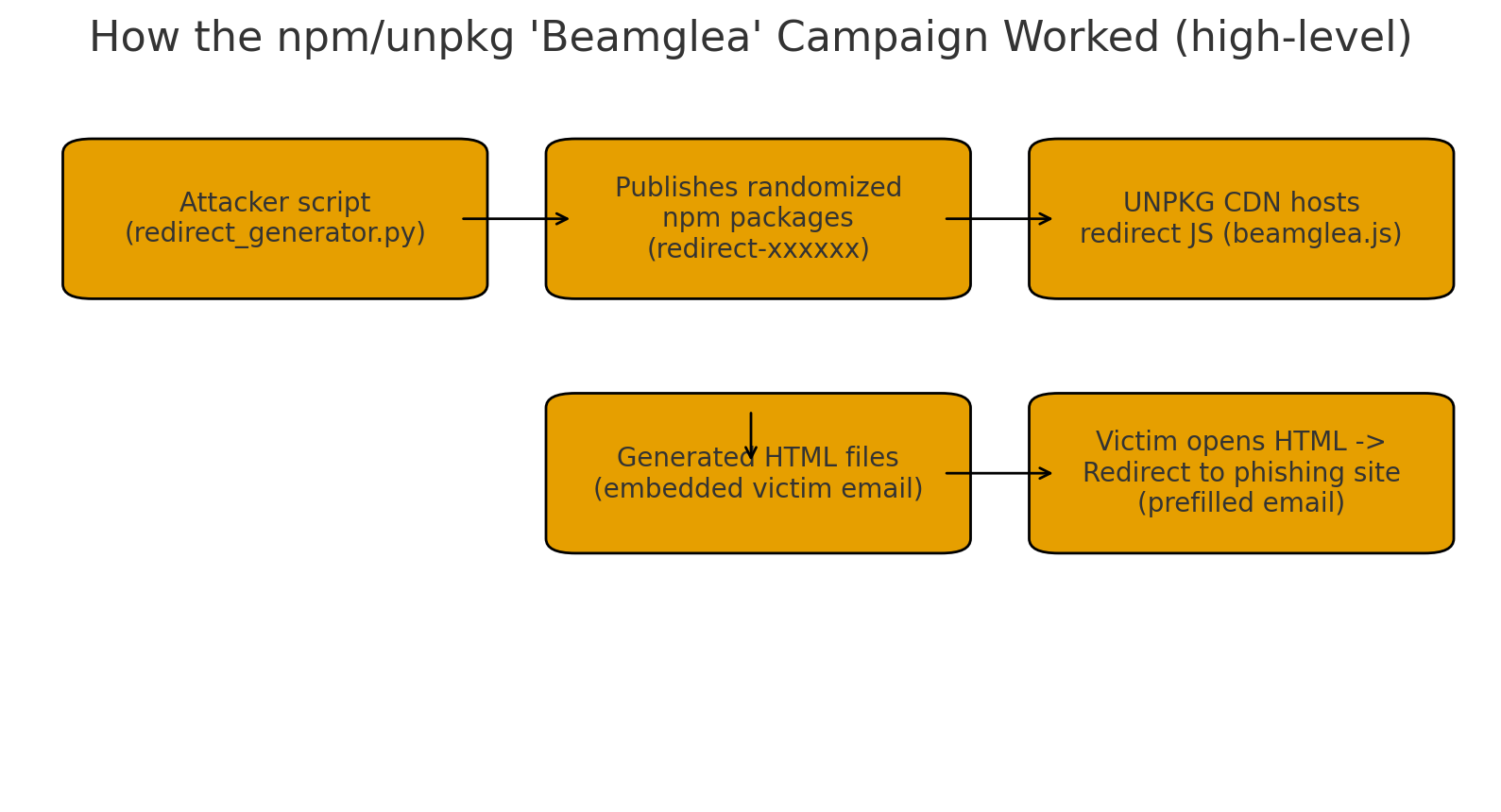
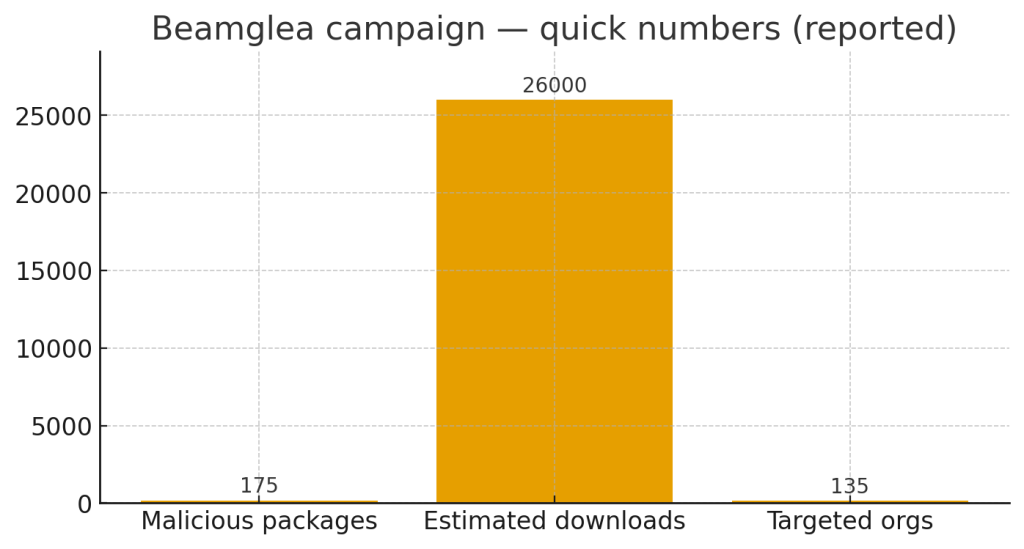
Security teams recently uncovered a coordinated campaign that used hundreds of small npm packages and the unpkg CDN as a free hosting layer for credential-phishing redirects. The operation published dozens of randomized “redirect-xxxxxx” packages and generated tailored HTML files that, when opened by a victim, immediately forwarded them to credential-collection pages with their email pre-filled. According to Socket’s investigation and earlier work by Safety, the set totals roughly 175 malicious npm packages with around 26,000 recorded downloads and infrastructure targeting 135+ organizations.
What happened (plain language timeline)
Researchers first noticed suspicious redirect behavior on September 24, 2025. Safety’s initial discovery flagged the pattern; Socket’s follow-up analysis documented a larger ecosystem of packages and automated tooling that generated them. The core pieces were:
- An attacker-side script (identified as
redirect_generator.py) that programmatically creates npm packages with randomized names such asredirect-xxxxx. Socket - Each package publishes an HTML/JS pointer that is automatically served via the unpkg CDN. That JavaScript (reported as
beamglea.jsin analyses) contains the victim-specific redirect URL and the victim’s email. When the hosted HTML is opened, it loads that JS and forwards the user to a credential-phishing page with the email field pre-populated. - Because the packages themselves contain minimal code and do not execute on install, the campaign leveraged npm/unpkg primarily as free, trusted hosting rather than as a supply-chain execution vector. That design makes detection by package-install checks harder while still producing a highly effective phishing channel.
Scale and impact — what the numbers mean
Socket’s expanded scan found 175 packages involved in the campaign; aggregated download counts reported by scanning tools are around 26,000 — though researchers note that many downloads are likely automated scans and CDN fetches rather than developer installs. The investigation also linked the infrastructure to a targeted campaign (named Beamglea in reporting) aimed at more than 135 companies across industrial, technology and energy sectors. These figures indicate a large, low-cost phishing platform that can be replicated and reused.
Why this technique is clever — and dangerous
- Trusted-hosting abuse: By using npm (a trusted registry) together with unpkg (a legitimate CDN), attackers host redirecting scripts on domains that often escape immediate suspicion. Users and some automated scanners are less likely to block or flag content coming from well-known CDNs.
- Low forensic footprint for installs: Because the malicious packages don’t run code on
npm install, typical runtime protections are less effective; the real payload is loaded only when someone opens an externally distributed HTML file. - Victim-specific social engineering: Generated HTML files contain the victim’s email; when redirected to the phishing page the email field is prefilled, dramatically increasing the credibility of the fake login form and the chance of credential submission. The Hacker News
How attackers probably distributed the HTML (educated assessment)
Researchers have not published a definitive distribution vector for the HTML files, but the likely mechanisms include targeted email phishing, shared links in messaging platforms, or social-engineered file attachments that entice recipients to open benign-looking documents (purchase orders, specs, invoices) that contain the embedded redirect. Socket reported discovery of hundreds of such HTML artifacts masquerading as business documents.
Detection indicators and quick hunting queries
If you’re defending an organization, focus on these signals:
- Unusual UNPKG requests: look for inbound requests that reference
unpkg.com/redirect-or similar randomredirect-xxxxpaths. - HTML files with embedded unpkg references: search mail/attachment stores and shared drives for HTML files containing
unpkg.com/references. - Prefilled-email redirects: detect HTTP requests containing email addresses in the URL fragments or query parameters that resolve to login pages.
- Package publish spikes: monitor the npm accounts that are publishing many short-lived, randomly named packages. Socket flagged nine accounts responsible for the 175 packages.
Example SIEM / grep hunt (adapt to your logs):
grep -Ei "unpkg\.com/redirect-|redirect-[a-z0-9]{4,}" /var/log/httpd/*access.log
grep -Ri "unpkg.com/redirect" /mnt/shared/drives /home
Remediation & defensive steps (practical)
- Block and monitor unpkg usage: apply temporary blocking or monitoring rules for unexpected
unpkg.com/*redirect*paths, and use web proxies to rewrite or warn on external CDN requests that contain redirection logic. - Harden email gateways: enforce attachment scanning and HTML sanitization, disallow automatic opening of HTML attachments, and flag emails with embedded external script references.
- Raise user awareness: notify targeted groups (finance, procurement, engineering) that staged documents may be bait; show examples of fake invoices and the tell-tale
unpkgreferences. - Rotate credentials & enable MFA: assume credentials exposed via phishing will be abused; require MFA and implement conditional access where possible.
- Work with registries: report malicious packages to npm and with the CDN provider (unpkg) so they can take down hosting and block the publisher accounts. Socket and other vendors provided lists of the malicious packages to registries for takedown.
Broader context — a recurring pattern in 2025 supply-chain attacks
This campaign is the latest example of adversaries weaponizing open-source ecosystems: earlier incidents in 2025 included trojanized popular npm packages and automated republishing tools that injected malware into dependencies. The pattern shows attackers increasingly prefer low-cost, high-trust hosting abuse (CDNs, package registries) and automation to scale targeted phishing and credential-theft campaigns.
What security teams should measure (KPIs)
- Number of
unpkg.com/*redirect*hits per week (target: 0) - Count of HTML attachments with external script references opened by users
- Percentage of targeted groups with enforced MFA (target: 100%)
- Time from detection to takedown for malicious packages (goal: <24 hours)
Final takeaways
The Beamglea campaign shows how simple tools and free hosting can be combined to build resilient, targeted phishing infrastructure. It underlines the need for defenders to shift from purely code- or install-time protections to monitoring hosted content, CDN usage, and the distribution channels attackers exploit. If you run an enterprise environment, treat externally hosted script loads from package CDNs as potentially hostile, and bake that assumption into proxy rules, email hygiene and incident playbooks.