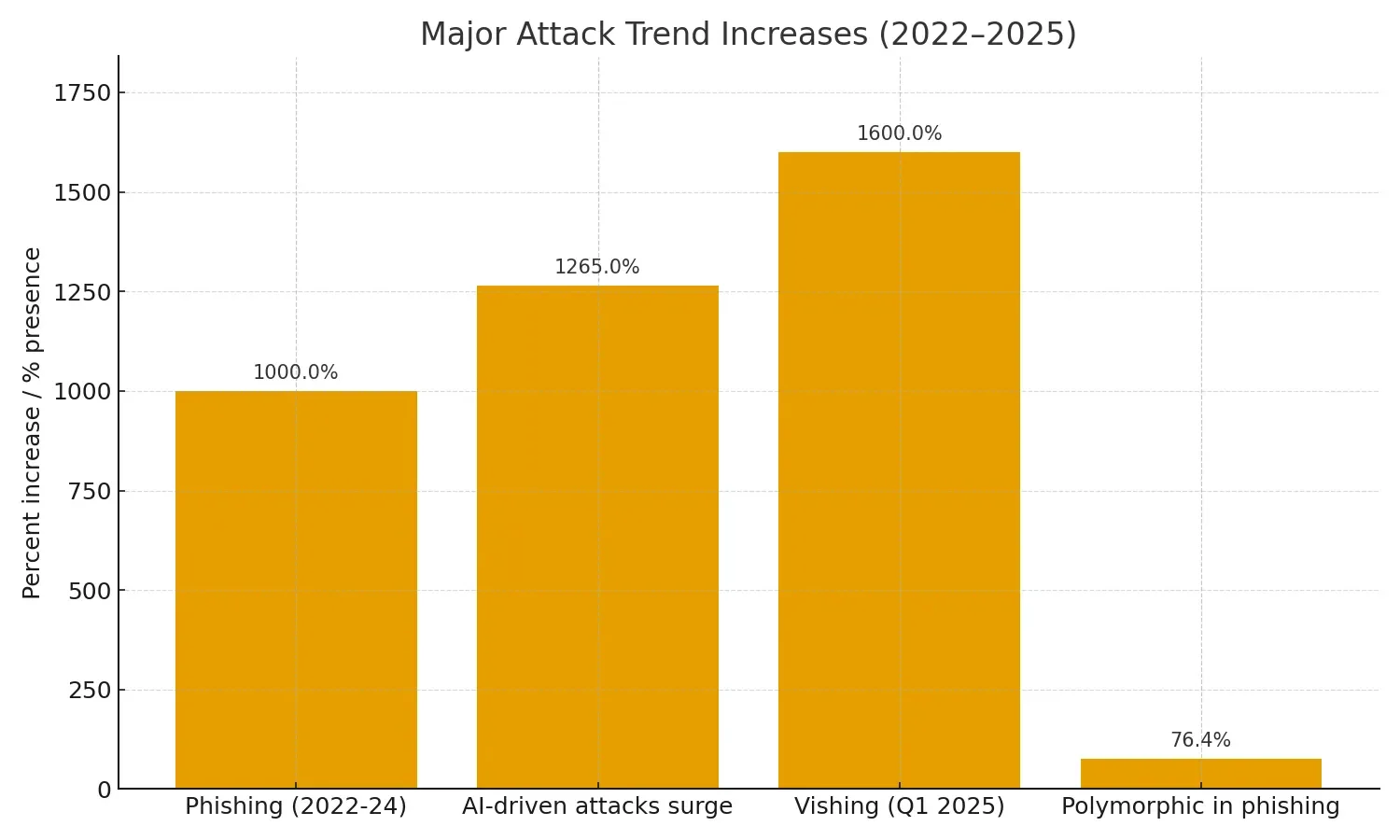
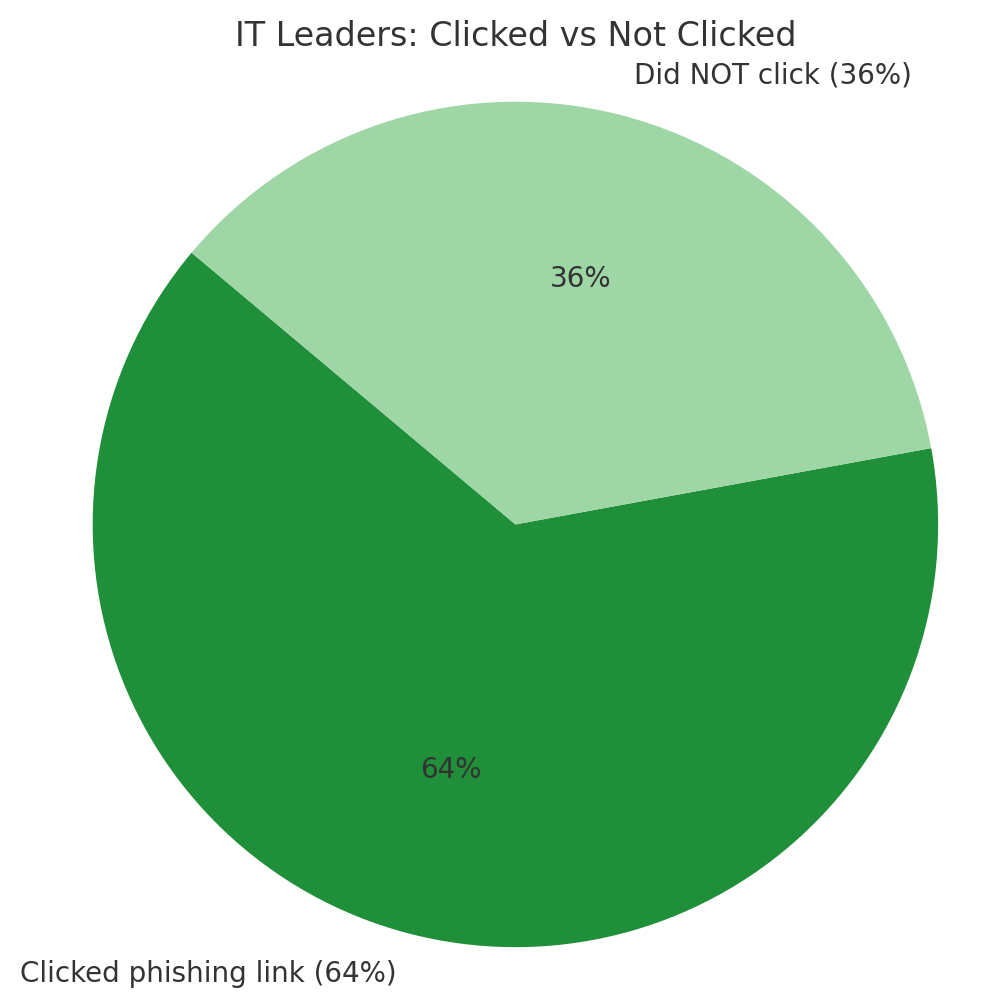
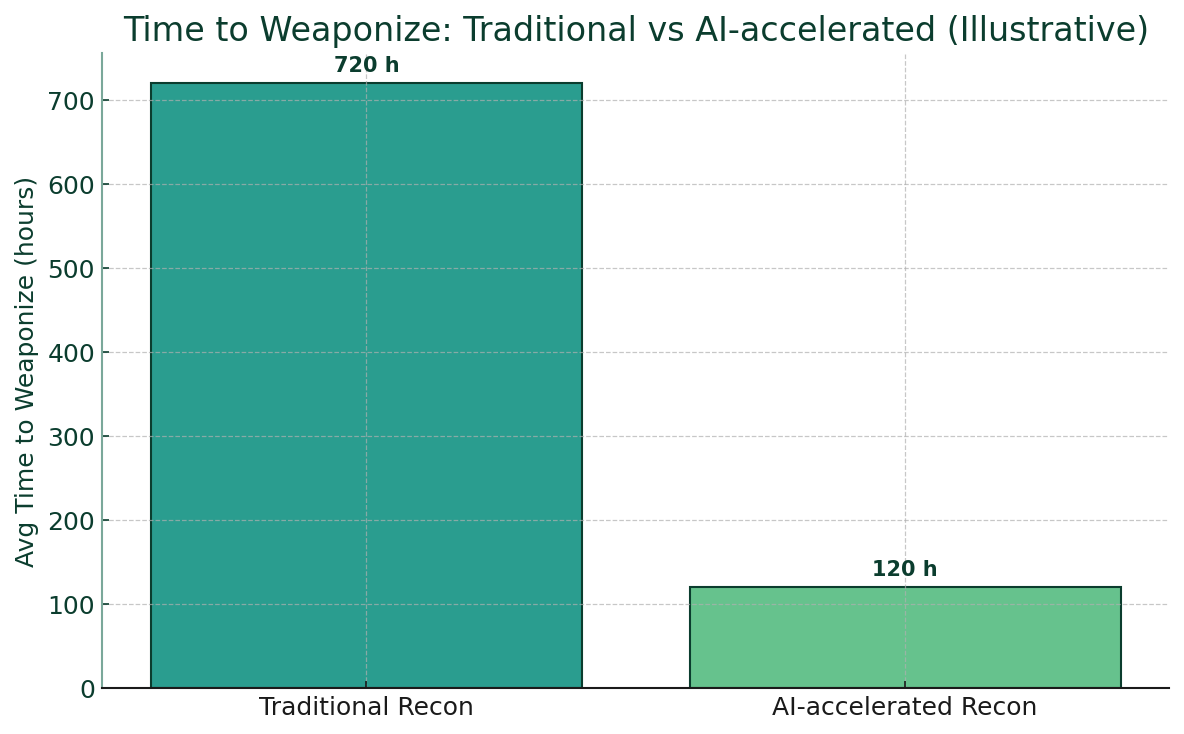
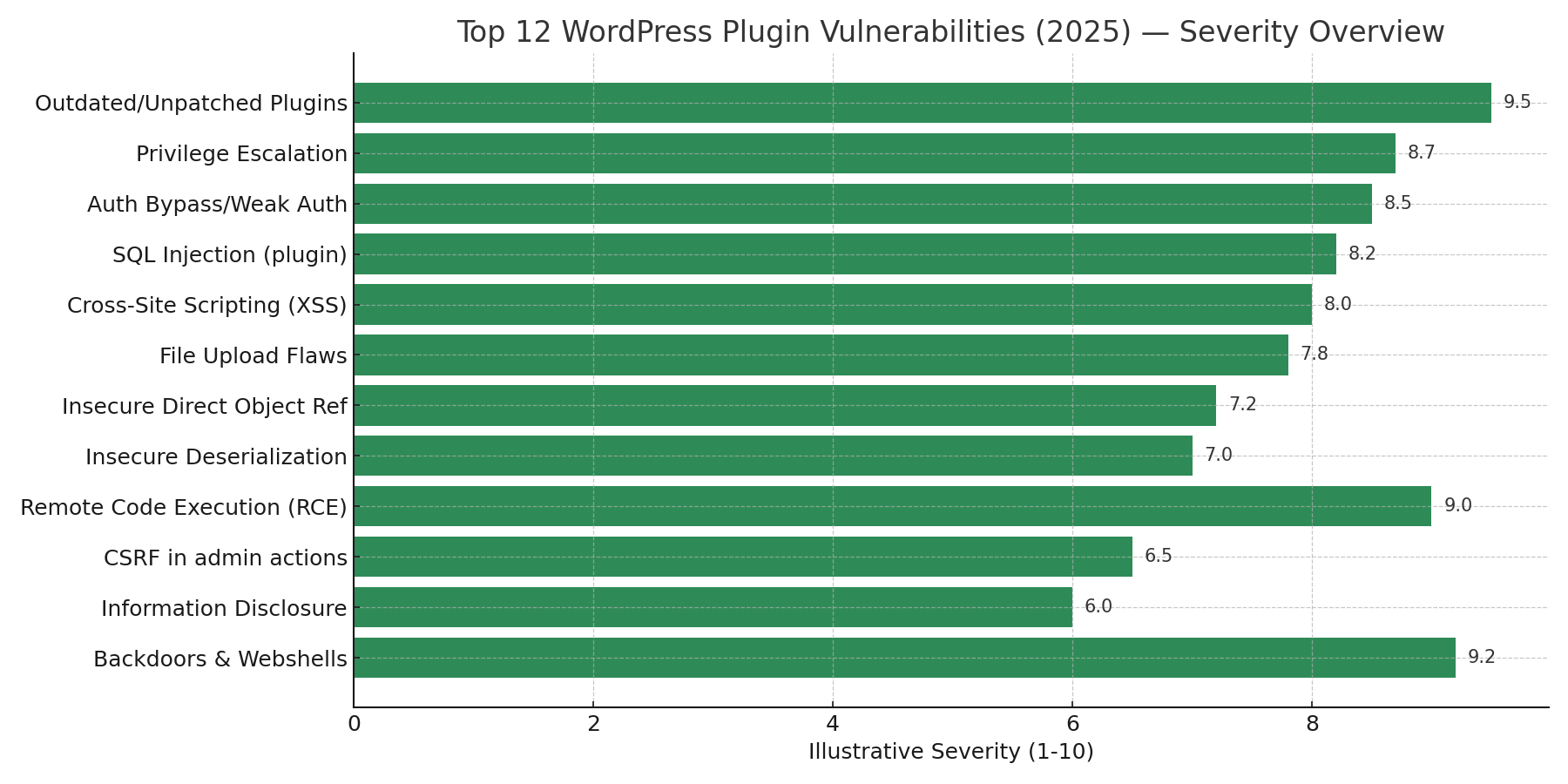
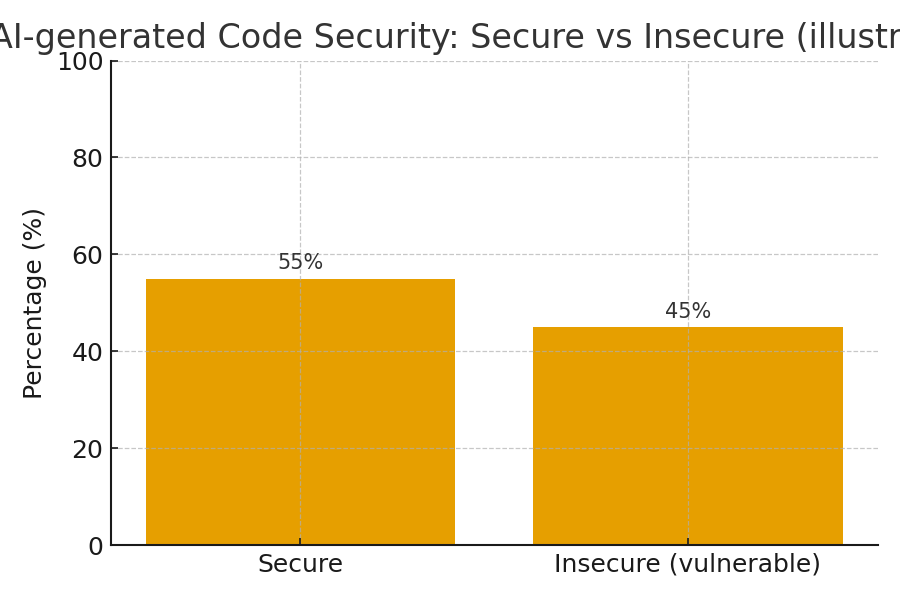
A new attack technique is quietly becoming one of the most prevalent cybersecurity threats of 2025. Known as ClickFix, FileFix, or fake CAPTCHA attacks, this social engineering method has seen explosive growth, with some studies reporting increases of up to 517% in just six months. Major organizations including Kettering Health, DaVita, and the City of St. Paul have all fallen victim to these increasingly sophisticated attacks.
Read More