A critical authentication-bypass vulnerability in the Service Finder “Bookings” plugin/theme (affecting versions up to 6.0) allows unauthenticated attackers to take over accounts — including administrator accounts — on vulnerable WordPress sites. Multiple security researchers and vendors have confirmed active exploitation in the wild. If your site uses the Service Finder theme or bundled Bookings plugin, update to the fixed release immediately (or remove the plugin) and follow the emergency checklist below.
What happened (plain language)
Researchers disclosed a broken-authentication vulnerability in the Service Finder Bookings component that fails to validate certain cookie or AJAX parameters before performing a user switch/claim action. Because of that logic error an unauthenticated attacker can trick the site into authenticating as another user (including admins) and gain full control of the site. The issue has been tracked under public CVE identifiers and has been given a critical severity score (CVSS ~9.8). Security vendors and news sites report active exploitation, with attackers using this flaw for account takeover, malware installation, creation of rogue admin accounts, and other post-compromise activity.
How widespread is the risk? (context & statistics)
- WordPress powers a very large chunk of the web — roughly ~43% of all websites use WordPress — so plugin and theme vulnerabilities at scale are high-risk for the web ecosystem. That scale helps explain why high-severity WordPress vulnerabilities are attractive to attackers.
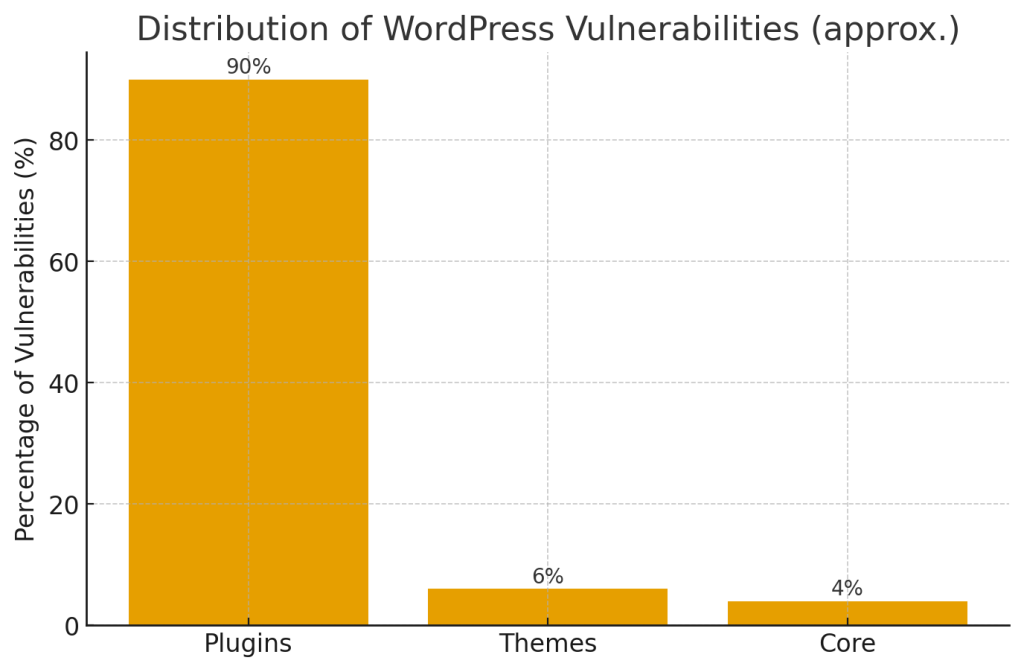
- The WordPress security ecosystem shows that the vast majority of reported vulnerabilities are in plugins — estimates used by researchers put plugin vulnerabilities at around ~90% of reported WordPress issues (with themes and core making up the remainder). That means plugin-related critical bugs like this one are statistically the most likely route to a site compromise.
Put simply: one critical plugin flaw affecting even a modestly popular theme or plugin can put thousands of websites at immediate risk.

Technical details (short, non-exploitable summary)
- Affected product: Service Finder — Bookings plugin (bundled with the Service Finder theme).
- Affected versions: All versions up to 6.0 (users should assume anything ≤6.0 is vulnerable).
- Fixed in: 6.1 (or a security patch published by the theme/vendor — update notes available in vendor advisories).
- Root cause: improper validation of user identity (cookie / AJAX action) when performing the
claim_business/switch_backflow, which permits privilege escalation and remote account takeover without proper credentials. - Severity / CVE: public CVE(s) and NVD entries list this as a critical authentication/privilege escalation issue (CVSS ≈ 9.8). Attackers can obtain admin privileges and then deploy webshells/backdoors, malicious redirects, or SEO spam.
Note: I intentionally keep the technical description high level — the goal is to explain impact and remedial steps without publishing exploit code or step-by-step attacker recipes.
Evidence of active exploitation
Multiple independent sources report in-the-wild exploitation: vendor advisories, security blogs and news outlets (e.g., The Hacker News, BleepingComputer) have observed attacks and warned site operators to patch or remove the plugin immediately. Active exploitation typically begins within hours or days of public disclosure for high-severity issues — treat this as an emergency.
Immediate, actionable emergency checklist (do these right now)
Use the downloadable checklist graphic (link below) and run through these steps immediately:
- Patch or remove the plugin — update Service Finder Bookings to v6.1 (or the vendor’s fixed release). If you cannot update immediately, deactivate and delete the Bookings plugin and any bundled theme plugin.
- Force admin & privileged user password reset and enable MFA for all administrator accounts. Rotate any API keys or tokens that may have been exposed.
- Audit user accounts — look for unknown administrator-level users and remove or lock them.
- Check for persistence — scan the filesystem and webroot for webshells, rogue PHP files, suspicious cron jobs, and unexpected scheduled tasks.
- Rotate credentials — change passwords for SFTP/SSH, database users, API credentials and any service accounts used by the site.
- Restore from a known-good backup if you detect signs of tampering and cannot confidently remove all persistence.
- Preserve forensic evidence — take immutable snapshots of files, databases and logs before making major changes (useful for investigation and insurance).
- Scan and monitor — run multiple malware scanners, and enable continuous monitoring (file integrity monitoring, WAF rules) to catch re-infection.
- Submit re-review / delisting requests if your site shows browser or search engine warnings (e.g., Google Safe Browsing).
- Contact your host or security provider for emergency assistance if you see active exploitation or elevated outbound connections.
Hunting & detection tips (how to know if you’ve been hit)
If you can access logs and the server, look for these indicators of compromise:
- Unusual admin logins from unfamiliar IPs, especially using the WordPress user id of an admin.
- Creation of unexpected administrator users or sudden privilege changes in
wp_users/wp_usermeta. - Suspicious outgoing connections from the web server (command-and-control domains).
- Files added under upload directories (wp-content/uploads), theme directories, or tmp folders that contain PHP code (particularly files with random names or timestamp changes).
- Malicious redirects or injected JavaScript observed on public pages.
- Web traffic spikes or unexpected cron jobs.
If you see any of these, assume persistence: snapshot forensics, isolate the host (put in maintenance), and perform an expert cleanup. See remediation timeline image below for expected timescales.
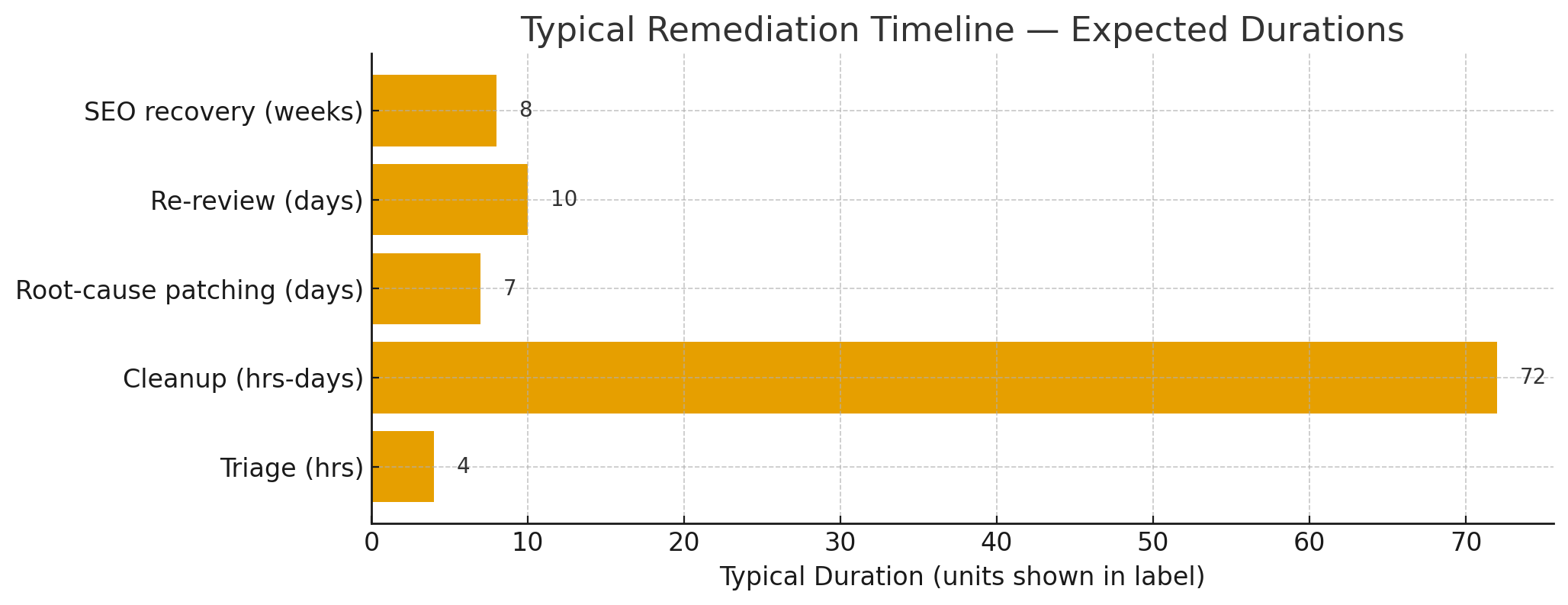
Practical remediation & recovery workflow (recommended sequence)
- Triage (0–4 hours): non-destructive scan, confirm presence/extent of compromise, and put site in maintenance mode if attack is active.
- Contain & snapshot (same day): block malicious IPs, create forensic snapshots of files and databases.
- Cleanup (hours → 3 days): remove malicious files, delete rogue users, sanitize databases (remove injected SEO spam), remove unauthorized cron jobs.
- Patch & rotate (1–7 days): apply vendor patches (update plugin to v6.1), rotate credentials, patch other vulnerable plugins.
- Verify & test (days): re-scan and crawl site as Googlebot and normal browsers, confirm no malicious resources remain.
- Google/re-index / SEO recovery (days → weeks): submit re-review requests, resubmit sitemaps and monitor indexing and search performance.
A representative remediation timeline image is available for download below. (Real timelines depend on site size and the complexity of compromise.)
Prevention: how to reduce your attack surface going forward
- Keep everything up to date (core, plugins, themes) and adopt a patching cadence (weekly/bi-weekly for high-risk environments).
- Minimize installed plugins and themes — remove unused or abandoned components.
- Harden authentication: enforce strong password policies, enable MFA for all privileged users and limit login attempts.
- Use a managed WAF/virtual patching to block exploit attempts while you test and deploy fixes.
- Enable file integrity monitoring (FIM) and centralized logging so changes are detected quickly.
- Implement least-privilege for database and filesystem accounts.
- Secure deployment pipelines: store secrets in a vault and restrict who can push changes to production.
- Backups & immutable snapshots so you can restore trusted states after a compromise.
- Consider professional monitoring & incident response for business-critical sites.
Because plugin vulnerabilities are the leading cause of site compromise, a combination of reduced plugin footprint, fast patching, and runtime protection greatly reduces risk.