WordPress powers a huge share of the web, and plugins make it flexible — but plugins are also the most common source of site compromises. In 2025 attackers continue to target vulnerable plugins, using automation, supply-chain abuse, and legacy code mistakes to gain access. This guide inventories the Top 12 plugin vulnerabilities, explains how attackers exploit them, provides practical detection scripts and checks you can run today, and gives robust mitigation patterns: from vendor patches to virtual patching with a WAF.
Quick TL;DR
- Top plugin risks in 2025: unpatched plugins, RCE/backdoors, privilege escalation, and obfuscated malware.
- Detection: use safe defensive scans (WP-CLI, WPScan, file scans, hash checks); avoid running exploit payloads.
- Fixes: update plugins, remove unused plugins, apply vendor patches; if patch not available use virtual patching (WAF/ModSecurity) and restrict plugin surface via mu-plugins or filters.
- If compromised: isolate site, take trusted backups offline, perform a full cleanup, rotate credentials, and request a review (Google Safe Browsing / hosts as needed).
- CTA: schedule a plugin security audit (we offer free quick scan + paid deep cleanup).
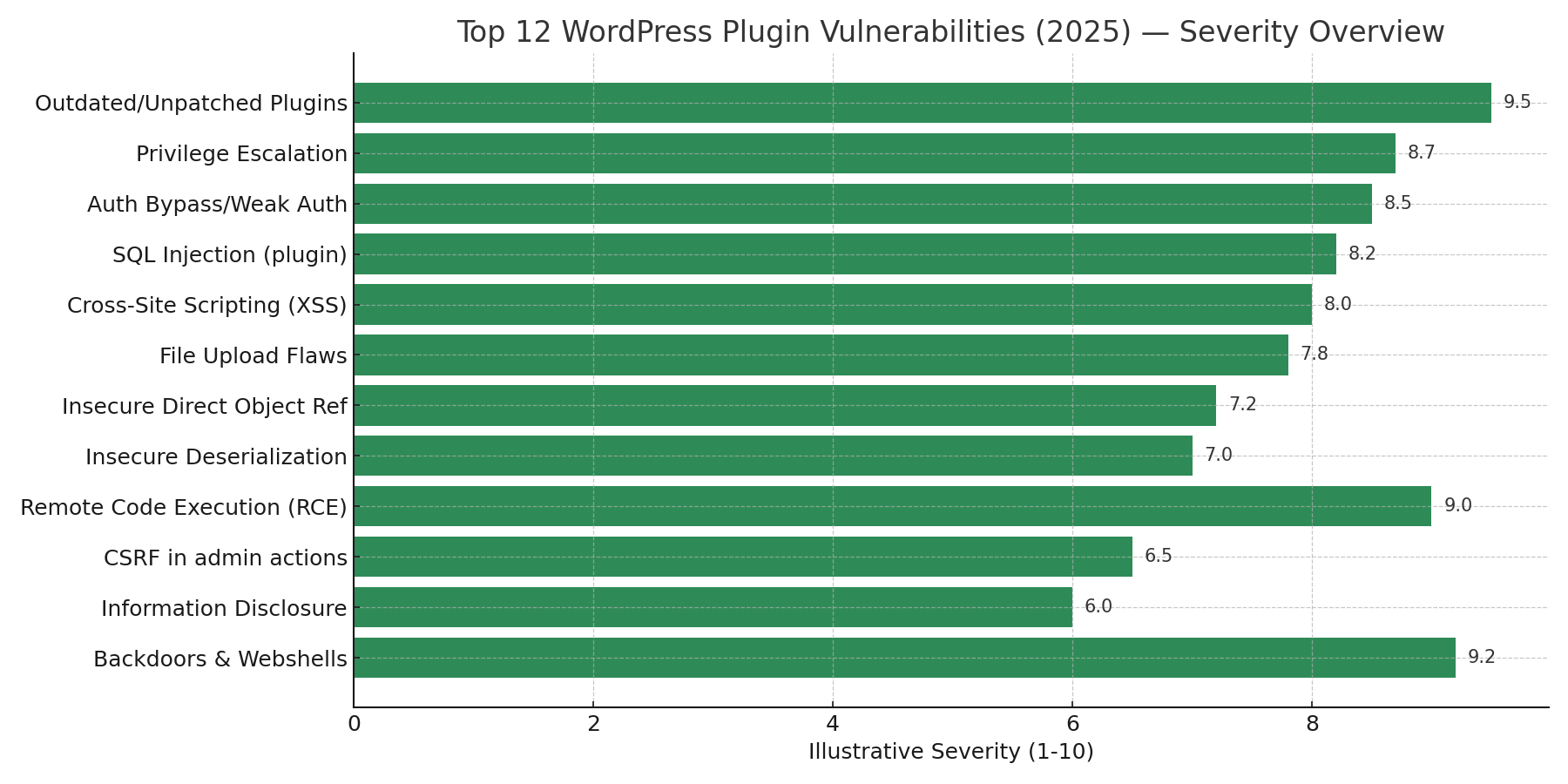
The Top 12 WordPress Plugin Vulnerabilities (2025)
Below is the canonical list based on observed incidents, public advisories, and typical attacker behavior. Severity scores are illustrative.
- Outdated / Unpatched Plugins — (Very High)
- Backdoors & Webshells — (Very High)
- Remote Code Execution (RCE) via plugin file inclusion — (Very High)
- Privilege Escalation (unauthorized capability grants) — (High)
- Authentication bypass / Weak auth flows — (High)
- SQL Injection in plugin endpoints — (High)
- Cross-Site Scripting (XSS) in admin/front-end — (High)
- File Upload Flaws (unsafe storage/execution) — (High)
- Insecure Direct Object References (IDOR) — (Medium-High)
- Insecure Deserialization — (Medium-High)
- CSRF in admin actions — (Medium)
- Information Disclosure (debug info, verbose errors) — (Medium)
| Vulnerability | Why it matters | Typical exploitation | Priority |
|---|---|---|---|
| Outdated / Unpatched Plugins | Known CVEs are public and widely scanned | Exploit via published PoCs or automated scanners | Critical |
| Backdoors & Webshells | Persistent control for attackers | Upload webshell via file upload, plugin bug, or compromised plugin update | Critical |
| RCE (File include, unsafe eval) | Full site takeover | Remote command execution through plugin endpoint | Critical |
| Privilege Escalation | Attacker becomes admin | Abuse of capability checks or misconfigured roles | High |
| SQLi (plugin) | Data theft, account takeover | SQL injection in plugin API endpoints | High |
How Attackers Exploit Plugins (High-level)
Attackers often follow an automated chain:
- Discovery — automated scanners identify sites with a given plugin + known CVE.
- Exploit — either using published PoC exploit or targeting misconfiguration (weak credentials, permissive file permissions).
- Persistence — upload backdoor/webshell or modify plugin files to maintain access.
- Escalation — create admin user or alter capabilities.
- Monetization — deploy spam/SEO injections, ransomware, cryptomining, or resell access.
Given this, a defense-in-depth approach is necessary: update, monitor, virtual patch, and mitigate blast radius.
Detection: Safe Scripts & Checks (Defensive)
Below are defensive commands and scripts you can run on your server or via an SSH session to detect suspicious plugin behavior. These are not exploit instructions — they are detection checks.
Important: Run these as an admin on your site server (SSH) or use your hosting control panel. Replace
example.comor/var/www/htmlwith your actual path. Always take a backup before performing extensive scans.
Inventory & Versions (WP-CLI)
# List installed plugins and versions (WP-CLI)
wp plugin list --format=csv > /tmp/wp-plugins.csv
# Output shows plugin, status, update available, version
Vulnerability Scan (WPScan) — defensive scan
# Use WPScan to enumerate known vulnerable plugins (requires API token)
wpscan --url https://example.com --enumerate vp,vt --api-token YOUR_TOKEN
Suspicious file patterns (search for obfuscation/backdoors)
# Look for potentially obfuscated PHP patterns in plugins (defensive)
grep -R --line-number -E "eval\\(|base64_decode\\(|gzinflate\\(|str_rot13\\(" wp-content/plugins || true
Recently changed plugin files (possible compromise)
# Find plugin files modified in last 30 days
find wp-content/plugins -type f -mtime -30 -print
Check for rogue admin users
# List admin users
wp user list --role=administrator --format=csv
File integrity check (hash compare)
Create an index of known-good plugin file checksums from a trusted clean install and compare using sha256sum for changes.
| Tool | Purpose | Use case |
|---|---|---|
| WP-CLI | Inventory, updates, user checks | Quick plugin list, user audits, automated scripts |
| WPScan | Vulnerability enumeration | Find known vulnerable plugin versions |
| grep / find | File-level scanning for indicators | Search for obfuscated code, new files, modified files |
| Static file hashes | Integrity verification | Detect tampering by comparing against clean checksums |
Real Examples & Case Notes (Redacted / High-level)
- Case A — Supply-chain compromise: An attacker uploaded a malicious plugin update to a compromised developer account. Hundreds of sites installing automatic updates were compromised and delivered spam/SEO injections. Lesson: vet developer accounts, sign updates, and prefer signed plugins where possible.
- Case B — Legacy plugin RCE: A discontinued plugin had an unauthenticated file-inclusion endpoint used for RCE. Hosts that had old versions installed were fully compromised. Lesson: remove unused plugins and monitor plugin EOL notices.
- Case C — Obfuscated backdoor found in plugin folder: Post-incident forensic analysis found
class-cache.phpwitheval(base64_decode(...)). Attackers used this to persist. Lesson: file scanning & integrity checks quickly detect such obfuscation.
How to Fix Plugin Vulnerabilities (Step-by-step)
- Update first — Always check vendor updates and test them in staging. Updating often removes known vulnerabilities.
- Remove unused plugins — If you don’t need a plugin, delete it (not just deactivate).
- Apply vendor patches — If a patch exists, install and verify.
- If patch is not available: virtual patch (WAF) — Add WAF rules to block exploit vectors until patch arrives.
- Harden permissions — Limit file write permissions; disable plugin file editing.
- Lock down admin access — 2FA, restrict admin IPs, change login endpoints.
- Monitor & rollback — If you detect compromise, restore from a known-good backup and rotate all credentials.
Example: Virtual Patching with ModSecurity (Defensive)
Below is a defensive ModSecurity rule example that blocks common attempts to exploit file-inclusion / remote-eval signatures. This pattern is intended for your WAF to block suspicious payloads, not to instruct exploitation. Test rules on staging and adapt to your environment.
# ModSecurity example (defensive)
SecRule REQUEST_URI|ARGS|REQUEST_HEADERS "(?:base64_decode|eval\\(|gzinflate\\(|preg_replace\\(.*\\/e)" \
"id:100001,phase:2,deny,status:403,log,auditlog,msg:'Potential PHP obfuscation payload blocked',severity:2"
You can also create rules targeting specific vulnerable plugin endpoints by matching the URI path and blocking write or execution parameters.
Hardening: File & Server Recommendations
- Disable plugin/theme file edits in wp-config.php:
define('DISALLOW_FILE_EDIT', true);
- Ensure proper file permissions:
- Directories:
755 - Files:
644 wp-config.php:600
- Directories:
- Prevent PHP execution in
wp-content/uploads:
# Example .htaccess in wp-content/uploads
<FilesMatch "\.php$">
Deny from all
</FilesMatch>
- Use a CDN + WAF (Cloudflare, Sucuri, etc.) for automatic virtual patching and DDoS protection.
| Action | Priority | Why |
|---|---|---|
| Update all plugins (staging first) | Critical | Fixes published CVEs |
| Remove unused plugins | High | Reduces attack surface |
| Run malware scan & file diff | Critical | Detects backdoors and changed files |
| Implement WAF rule for vulnerable endpoint | High | Virtual patch while vendor fixes |
| Rotate admin passwords + enable 2FA | High | Close compromised credentials |
Advanced Mitigation Strategies
- Virtual patching: use WAF rules to block request patterns or usernames payloads targeting the plugin until a vendor patch is available.
- Least privilege: plugin-specific database users (if possible) and limited capability grants.
- MU-plugins as safety net: put code in
mu-pluginsto override dangerous plugin hooks or disable risky features temporarily. - Staging validation: test updates in staging with a full regression suite before pushing to production.
- Continuous file-integrity monitoring: solutions like Tripwire, AIDE, or commercial FIM track unexpected changes and alert quickly.
Sample Incident Playbook (Short)
- Isolate — put site in maintenance mode, disable network access if serious.
- Backup — take a forensic image of the current state before changing anything.
- Scan — run the detection steps above (WP-CLI, grep, wpscan).
- Validate — compare with clean plugin versions (hashes).
- Remove — remove malicious files, suspicious plugins, or compromised code.
- Patch — update or virtual patch.
- Harden — rotate secrets, enable 2FA, fix permissions.
- Monitor — heightened monitoring for at least 30 days.
- Notify — if user data possibly exposed, follow regulatory notification procedures.
When to Call Professionals (Website Security Service)
You should consider a professional plugin security service when:
- You detect an unknown backdoor or persistent webshell.
- The site is part of an e-commerce system (PCI/financial).
- You lack time/resources for deep forensics and safe clean restore.
- You want guarantees: some providers offer malware removal with warranty & Google blacklist removal.
- You need full vulnerability assessment and ongoing managed patching.
What a typical Plugin Security Audit includes: plugin inventory, vulnerability scan, file integrity audit, database checks for injected content, WAF tuning, and remediation report with remediation steps and estimated time/cost.