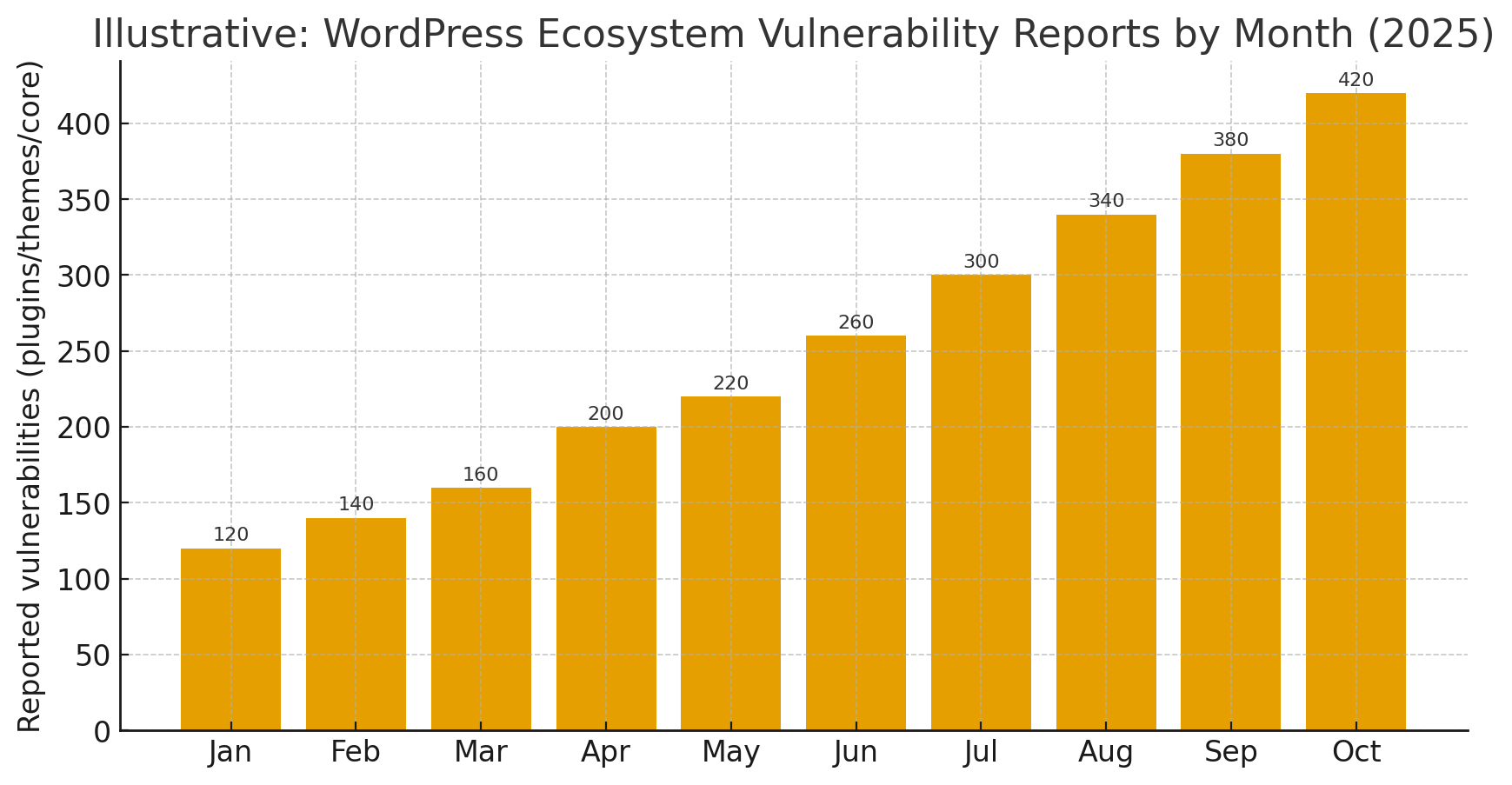
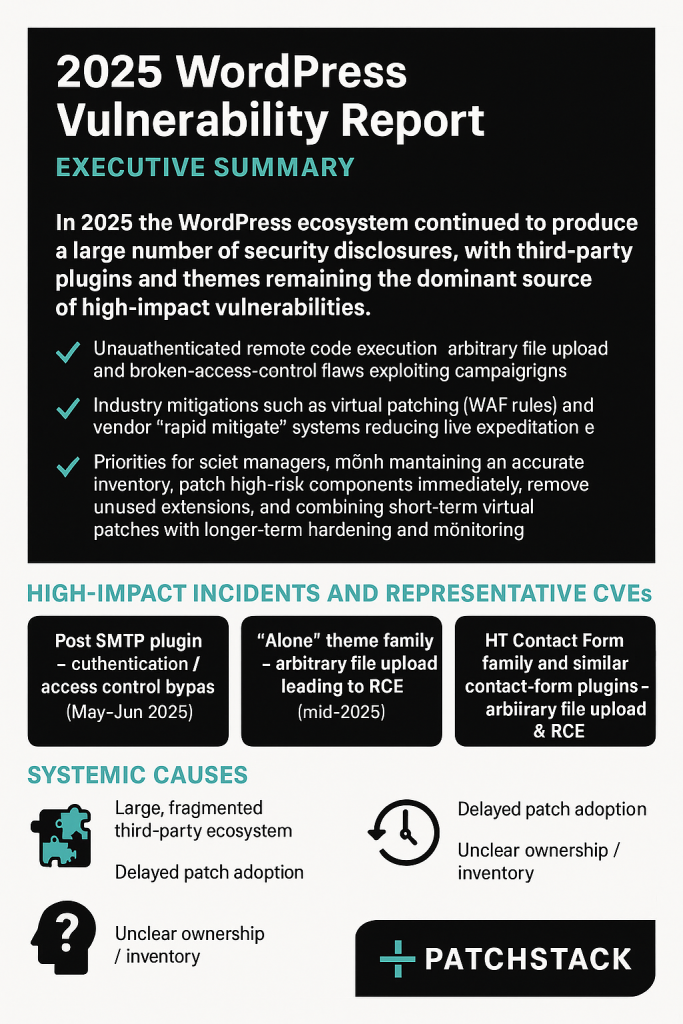
In 2025 the WordPress ecosystem continued to produce a large number of security disclosures, with third-party plugins and themes remaining the dominant source of high-impact vulnerabilities. Attackers quickly weaponized several unauthenticated remote code execution, arbitrary file upload and broken-access-control flaws, and exploit campaigns often began within days of disclosure. Industry mitigations such as virtual patching (WAF rules) and vendor “rapid mitigate” systems played a major role in reducing live exploitation while site owners applied official patches. If you manage WordPress sites, the priority remains the same: maintain an accurate inventory; patch high-risk components immediately; remove unused extensions; and combine short-term virtual patches with longer-term hardening and monitoring.
High-impact incidents and representative CVEs (what happened and how to fix it)
Below are several representative, well-documented incidents from 2025. Each entry briefly describes the flaw, real-world impact, and immediate & follow-up remediation steps.
1) Post SMTP plugin — authentication / access control bypass (CVE family, May–Jun 2025)
Summary: A critical broken access control vulnerability in the widely used Post SMTP plugin allowed low-privileged or unauthenticated actors to access email logs and perform actions that could lead to administrative takeover on affected sites. The flaw received high severity scores and was patched in a later release; nevertheless, a large number of installations remained unpatched weeks after disclosure. Immediate exploitation potential made this a mass-exploitation concern.
Immediate remediation
-
Upgrade Post SMTP to the vendor-released patched version as a top priority.
-
If you cannot patch immediately, deactivate the plugin or restrict access to its endpoints (e.g., block the plugin’s REST routes at the webserver or WAF).
-
Rotate any credentials that may have been exposed and audit admin sessions and users.
Follow-up
-
Limit storage of sensitive message contents in site logs; ensure logs are only accessible to admin staff behind authenticated controls or internal networks.
-
Add the plugin to your high-risk watchlist and monitor vulnerability feeds for follow-ups.
(Source: vendor and security vendor advisories reporting CVE and exploit data.)
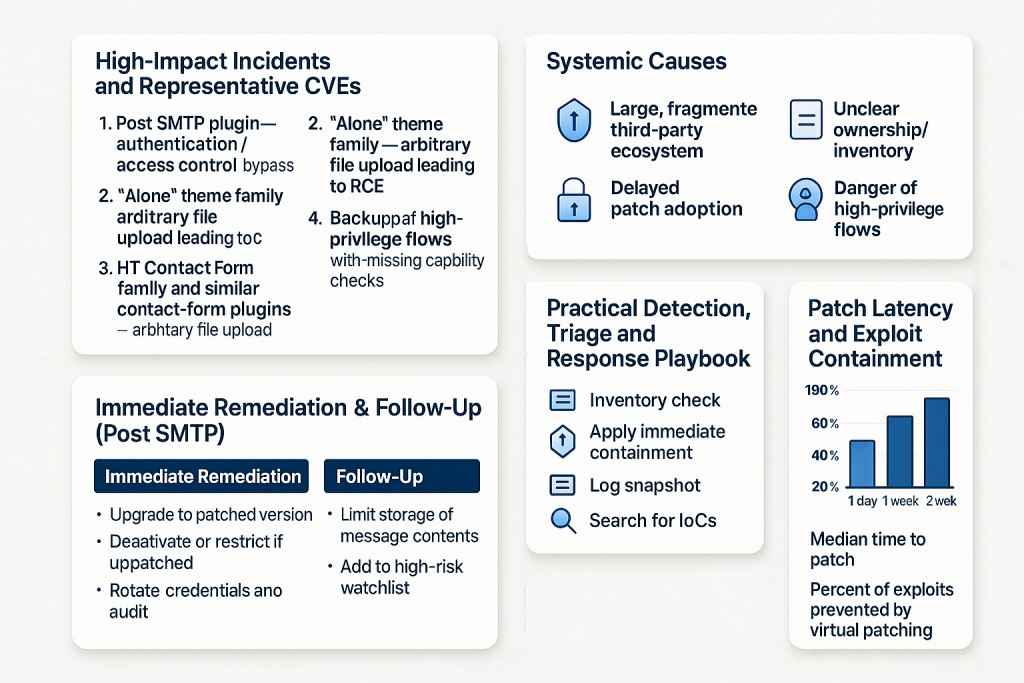
2) “Alone” theme family — arbitrary file upload leading to RCE (theme backdoor campaigns, mid-2025)
Summary: Several commercial WordPress themes (exemplified by an actively exploited “Alone” charity theme) contained an arbitrary file upload or remote install feature that threat actors abused to upload ZIPs with PHP backdoors, install malicious admin users, and achieve persistent remote code execution on victim sites. Exploitation began in the wild almost immediately after disclosure in multiple observed campaigns.
Immediate remediation
-
Update the theme to the vendor’s fixed version. If a patch is unavailable, disable the theme (switch to a safe default) and scan for newly added PHP files and admin accounts.
-
Remove any uploaded ZIPs, web shells, or files in
wp-content/uploadswith executable code.
Follow-up
-
Restore from a verified clean backup if persistence is found. Rotate secrets and reissue keys for integrated services.
-
Consider replacing commercial themes that have poor security histories with better-maintained alternatives.
(Source: vulnerability research and incident reports showing active exploitation patterns.)
3) HT Contact Form family and similar contact-form plugins — arbitrary file upload & RCE
Summary: Multiple contact form plugins were found to allow arbitrary file upload, insecure file handling, or insufficient sanitization that permitted remote code execution on affected installs. Some of these plugin vulnerabilities impacted thousands of sites and were actively targeted in exploit campaigns.
Immediate remediation
-
Patch or remove the vulnerable contact form plugin. If your site uses file uploads via forms, temporarily disable upload functionality until you confirm the plugin is secure.
-
Scan for unexpected PHP files in uploads and for modified core/theme files.
Follow-up
-
Force revalidation of uploads: implement server-side checks that forbid
.php,.phtml, and other executable extensions in upload directories and deny execution privileges for upload folders.
(Source: security vendor reports documenting specific contact form exploits.)
4) Backup and maintenance plugins with missing capability checks (example: Bears Backup RCE)
Summary: Backup and maintenance plugins that expose AJAX or management endpoints without proper capability checks have been discovered to allow unauthenticated attackers to invoke administrative functions, leading to remote code execution. These are particularly dangerous because backup/restore flows often touch files and database operations. The NIST NVD contains entries illustrating such gaps.
Immediate remediation
-
Update the plugin to the patched release or remove it if vendor support is absent.
-
Harden plugin endpoints by restricting access via IP allowlists or moving management interfaces behind VPN/SSH tunnels.
Follow-up
-
Audit backup integrity and verify no restored backups contain injected code. Ensure backups are stored encrypted and access is tightly controlled.
(Source: NVD CVE entries and vendor advisories.)
5) Core permission quirks & small-scope CVEs chained with plugin bugs
Summary: Some low-severity core bugs or misconfigurations surfaced in 2025 that, when combined with insecure plugins, formed exploit chains (for example, a minor permission oversight enabling escalation after a plugin RCE). These illustrate how layered defenses must be applied across core, themes and plugins.
Mitigation
-
Keep WordPress core up to date, disable in-dashboard file editing (
DISALLOW_FILE_EDIT), and apply strict file system permissions. -
Conduct periodic configuration audits to detect risky core settings.
(Source: CVE tracking and vendor advisories covering core and chained abuse.)
Systemic causes (why the same problems keep happening)
Across the incidents above and many others in 2025, several systemic themes recur:
-
Large, fragmented third-party ecosystem. Hundreds of thousands of plugins and themes exist, varying widely in maintenance and security maturity; this increases attack surface and the probability that some extension is insecure. Patchstack and other trackers reported thousands of new plugin & theme vulnerabilities across 2025.
-
Delayed patch adoption. Even when vendors release fixes quickly, a substantial share of active installs delay updates — prolonging exposure and enabling mass exploitation attempts. Observers reported high percentages of sites running vulnerable versions weeks after patches were available.
-
Unclear ownership / inventory. Many sites don’t maintain an accurate inventory of installed extensions or who is responsible for them, which complicates triage and patch management.
-
Danger of high-privilege flows. Plugins that expose admin-level features via AJAX or REST endpoints without robust capability checks are a recurring root cause of RCEs and privilege escalations.
Practical detection, triage and response playbook (24–72 hours)
When a high-impact WordPress vulnerability is disclosed or you suspect exploitation, follow this operational sequence:
Triage & detection (first 0–24 hours)
-
Inventory check: enumerate installed plugins/themes and their versions; flag any items on public advisories.
-
Apply immediate containment: if a patched version exists, schedule emergency updates for affected sites. If patching is not immediately possible, apply WAF rules or block the offending endpoints at the edge. Many vendors deploy “virtual patches” that block exploit traffic until you can update.
-
Log snapshot: collect web server logs, PHP error logs, access logs, and plugin-specific logs for forensic analysis.
-
Search for IoCs: scan for new admin users, unexpected PHP files in uploads, unusual scheduled tasks, and outbound connections from web processes.
Remediation (24–72 hours)
-
Patch or remove the vulnerable extension; test updates in staging if feasible but prioritize critical fixes on high-risk public-facing sites.
-
If compromise is suspected: isolate the site, rotate credentials and API keys, and restore from a verified clean backup after removing persistence.
-
Hardening: disable file editing in dashboard, enforce 2FA for admin accounts, restrict admin panels by IP, and set secure file permissions.
-
Monitoring: maintain elevated logging for at least 30 days and watch for re-injection attempts.
Hardening checklist (operational controls to reduce likelihood & impact)
Apply these baseline controls across all WordPress assets:
-
Inventory & patch policy: automated inventory of plugins/themes, weekly patch windows, and emergency patch process for CVEs with active exploits.
-
Least privilege: ensure plugin/service database users have minimal privileges; run site processes under constrained accounts.
-
WAF/virtual patching: subscribe to reputable WAF/intel providers and enable virtual patch rules for critical advisories until official patches are applied.
-
Disable risky features: set
DISALLOW_FILE_EDIT, disable XML-RPC if not needed, and limit REST endpoints exposed to unauthenticated users. -
Backups & immutable snapshots: keep offline, versioned backups, and practice restoration drills.
-
File integrity monitoring: scan for unexpected PHP files, modified hashes, and new scheduled tasks.
-
Authentication & access: enforce MFA for all admin users, use strong password policies, and limit login attempts.
-
Staging testing: patch first in staging, verify site functionality, then push to production.
-
Telemetry & SIEM: centralize logs and create alerts for new admin creation, file writes in upload dirs, large numbers of 404/500 errors, and suspicious outbound traffic.
Recommended tooling & feeds
-
Vulnerability trackers / feeds: subscribe to multiple sources (security vendors, plugin advisory feeds, Patchstack/Wordfence/SolidWP) to get fast, corroborated reports. Patchstack’s mid-year reporting and vendor mitigation services are an example of active threat intelligence for the WP ecosystem.
-
WAF & CDN: use providers capable of rapid rule deployment (virtual patches) for urgent CVEs.
-
File integrity & malware scanners: run periodic scans (both signature and heuristic) and integrate results into your incident workflow.
-
Automated inventory & update tools: tools that report installed versions and notify owners are critical to reducing lag between patches and deployment.
Measuring success — KPIs you should track
-
Patch latency: median time from disclosure to patch application across your site fleet.
-
Exploit containment rate: percent of high-risk CVEs where virtual patching prevented exploitation before patch rollout.
-
Time to detect compromise (MTTD) and time to remediate (MTTR) for exploited sites.
-
Inventory coverage: percentage of sites with complete plugin/theme/version telemetry.
-
Number of residual vulnerable installs after N days of a critical advisory.
Final recommendations & closing
2025 reinforced that WordPress security is primarily a supply-chain and maintenance problem: the core platform is typically secured via official releases, but the third-party ecosystem drives most successful attacks. Treat plugin/theme management as a first-class security function: keep a trimmed inventory, automate updates where safe, subscribe to multiple vulnerability feeds, and use virtual patching as an immediate compensating control when official fixes lag.