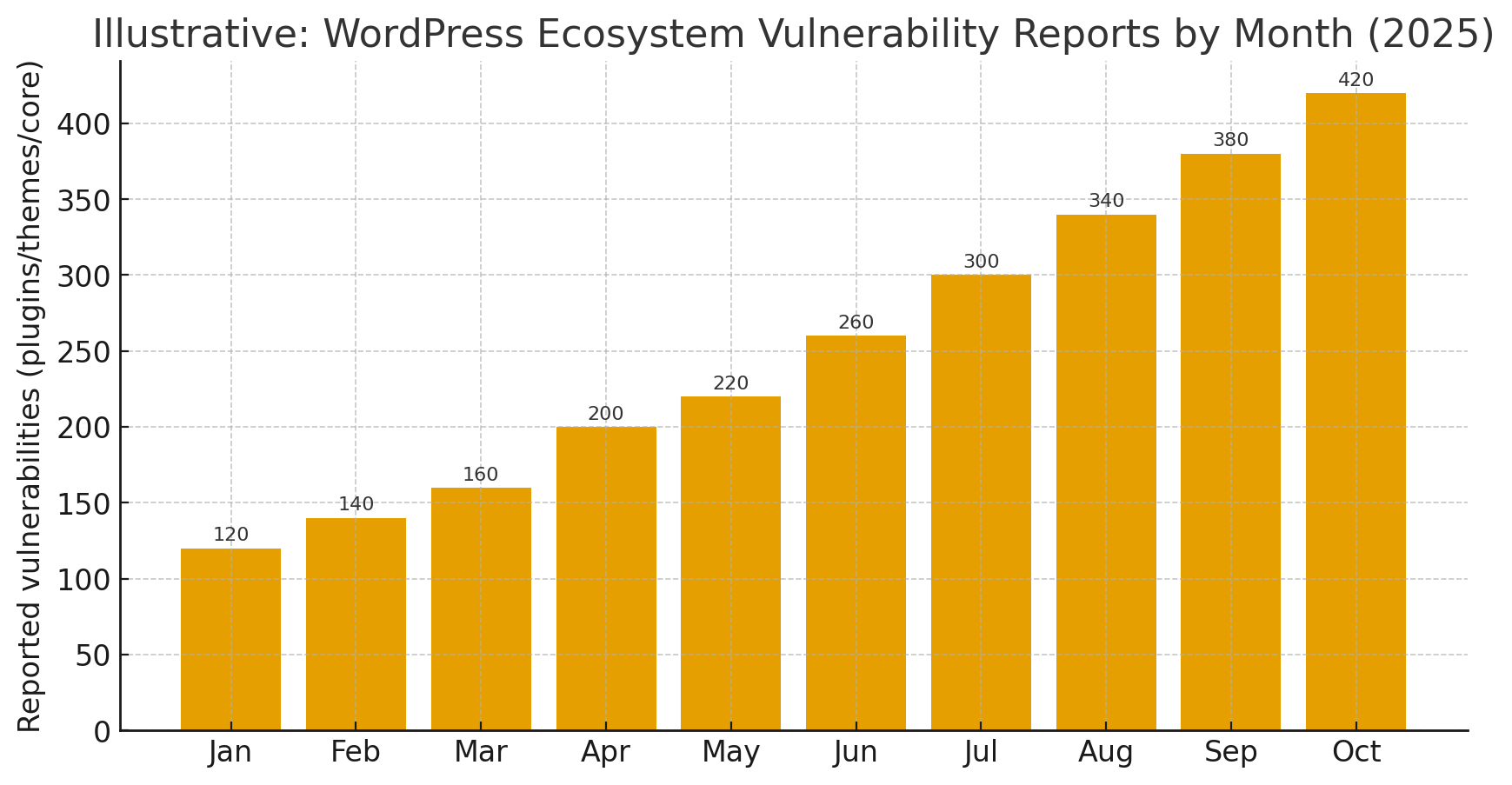
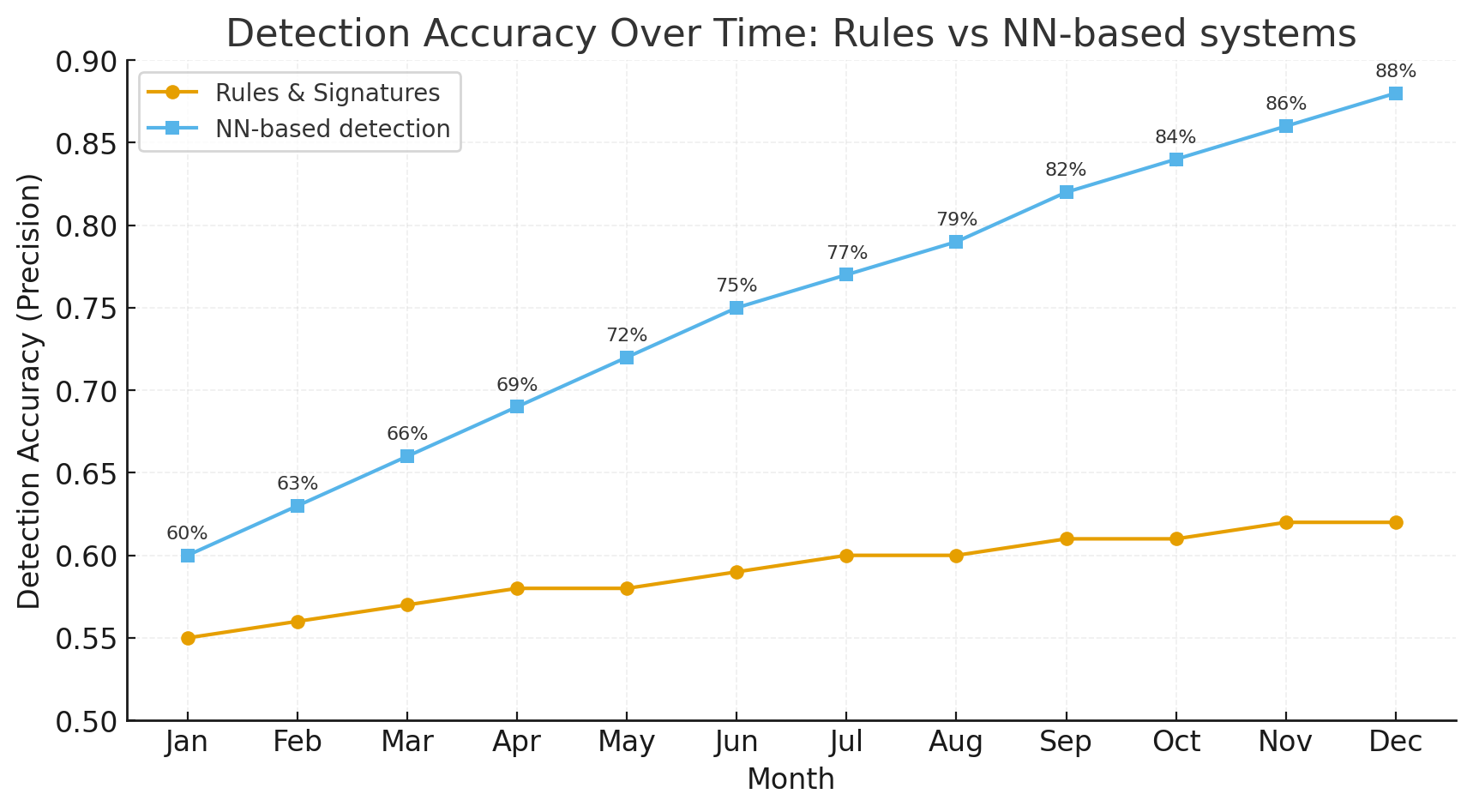
In 2025 several high-impact vulnerabilities affecting Adobe Commerce and Magento Open Source were publicly disclosed and patched. The most critical is the so-called SessionReaper (CVE-2025-54236) — an improper input validation flaw in the Web API that can lead to session takeover and, in specific conditions, unauthenticated remote code execution. Adobe released an out-of-band hotfix and urged immediate application. Other important 2025 CVEs include a set of access-control and authorization bugs (several CVE entries), and multiple XSS/authorization issues fixed across release updates. Apply vendor patches immediately and follow the detection checklist below.