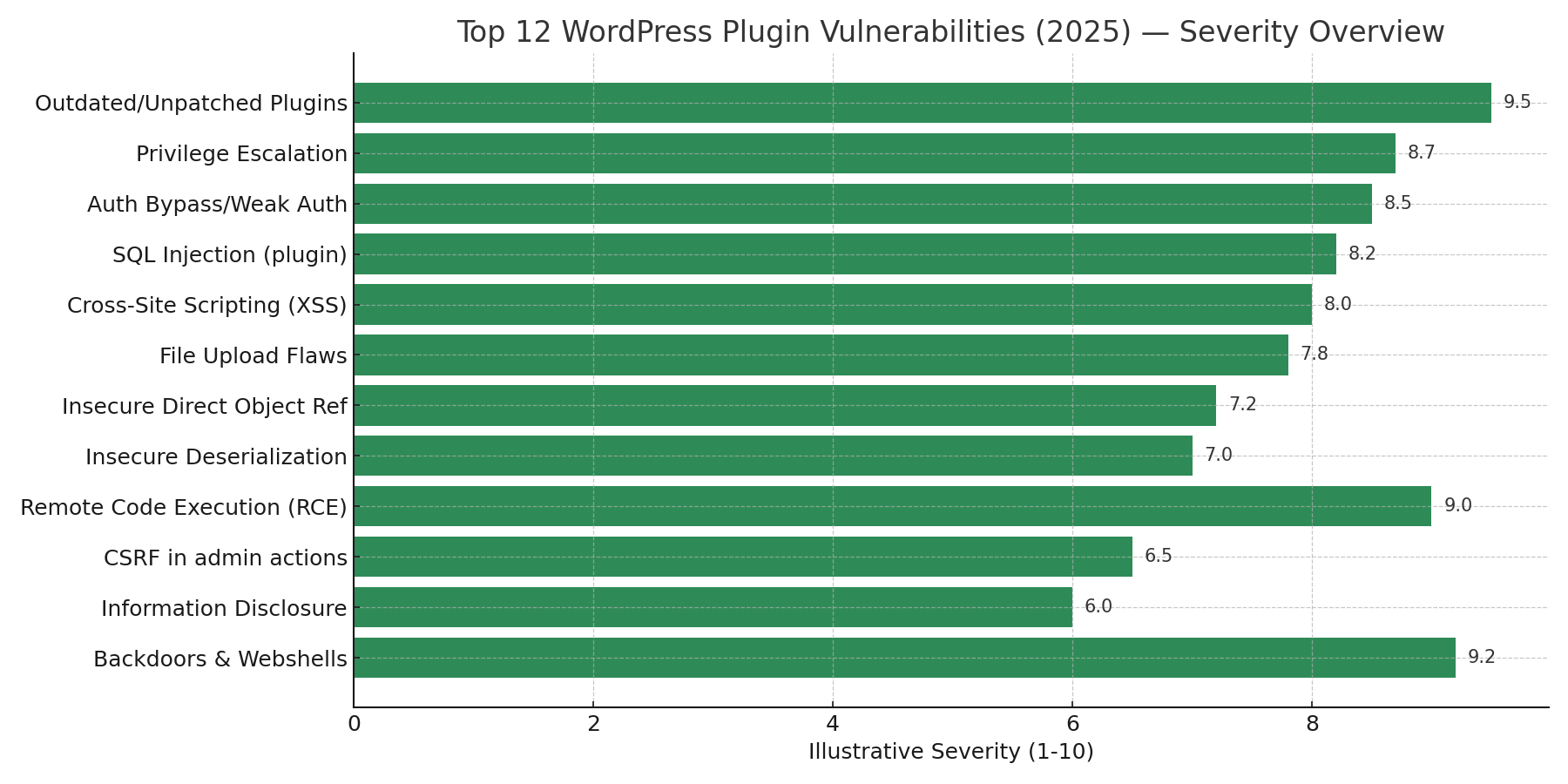
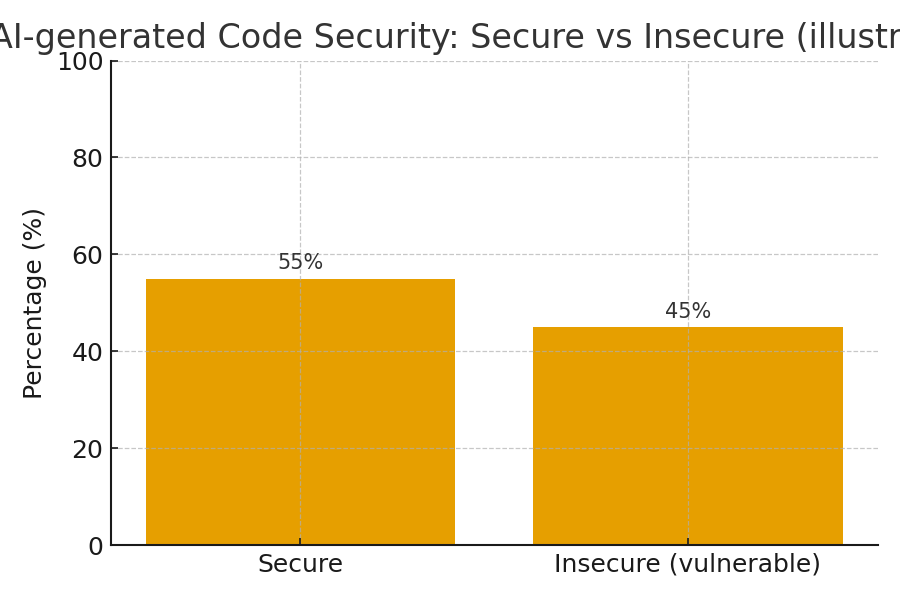
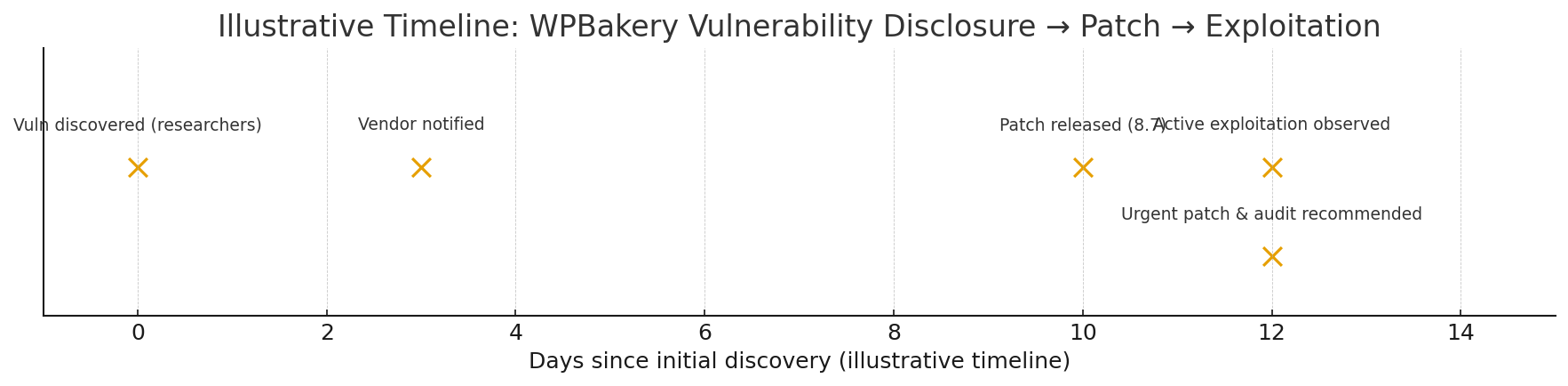
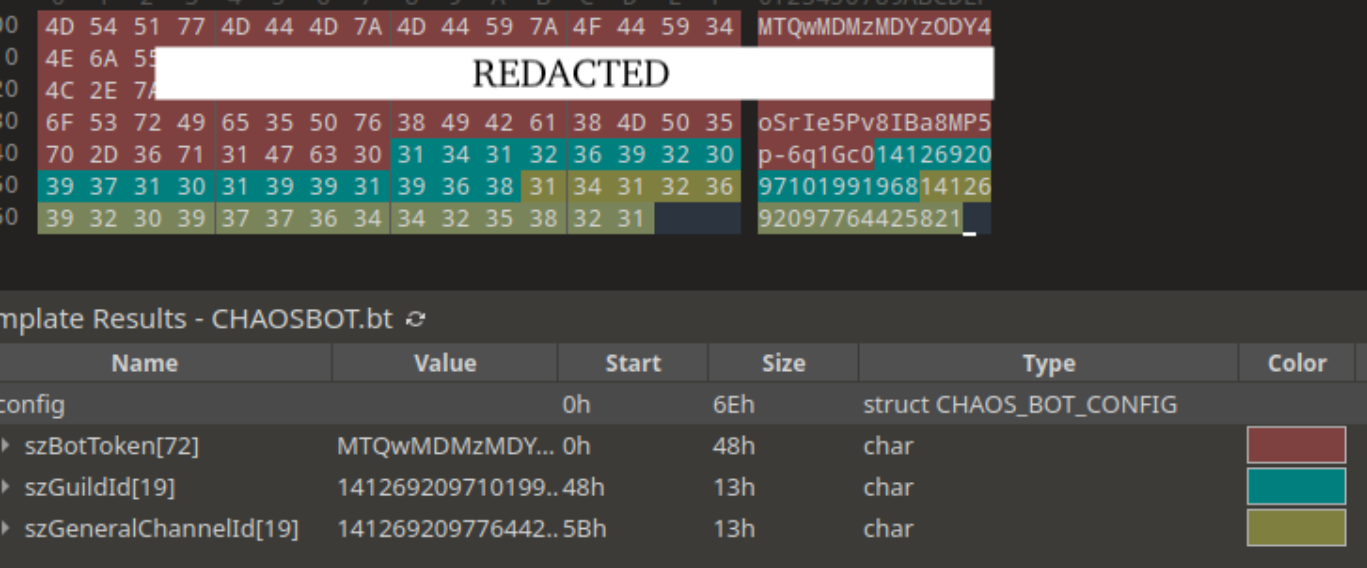
WordPress powers a huge share of the web, and plugins make it flexible — but plugins are also the most common source of site compromises. In 2025 attackers continue to target vulnerable plugins, using automation, supply-chain abuse, and legacy code mistakes to gain access. This guide inventories the Top 12 plugin vulnerabilities, explains how attackers exploit them, provides practical detection scripts and checks you can run today, and gives robust mitigation patterns: from vendor patches to virtual patching with a WAF.
Read More