New research reveals a disturbing truth: the very people responsible for cybersecurity are falling victim to phishing attacks at alarming rates—and a culture of fear is preventing many from reporting their mistakes.
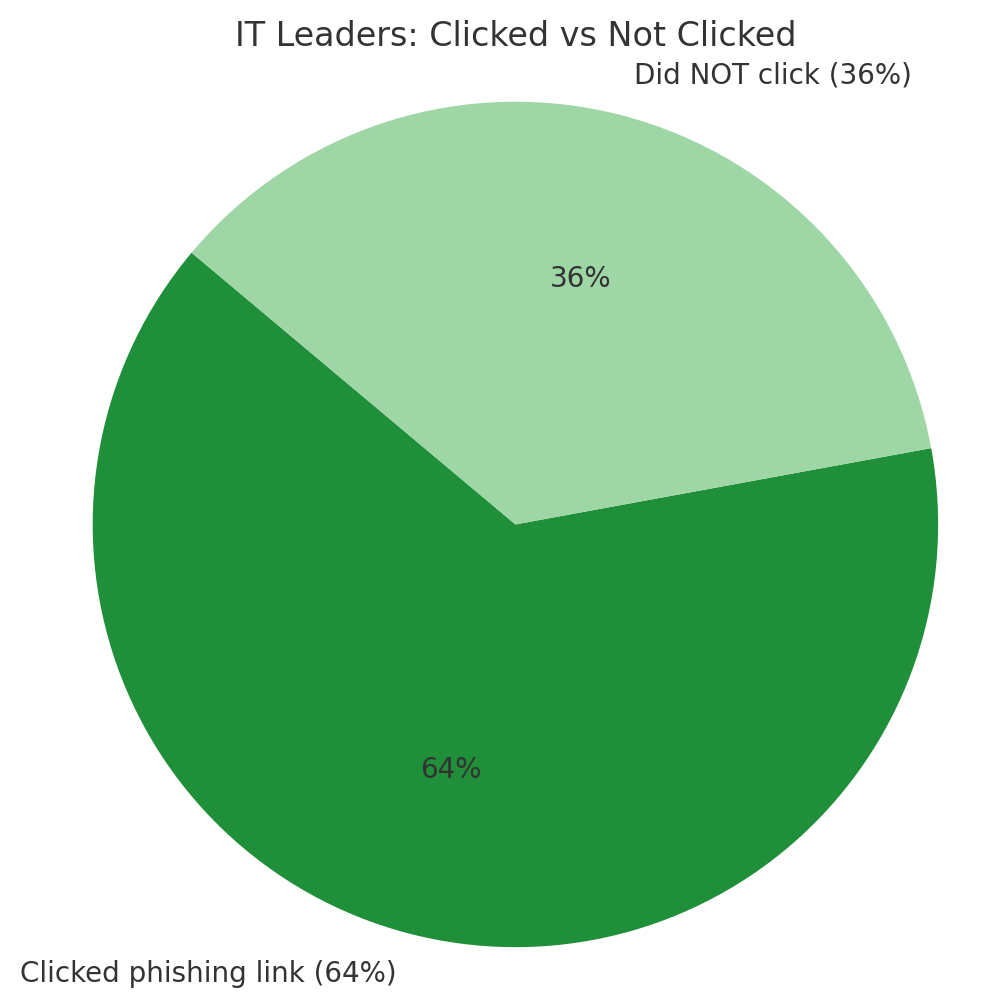
If you think your organization’s IT leadership is immune to phishing attacks, think again. A groundbreaking study from Arctic Wolf has uncovered a troubling reality that should concern every business leader: nearly two-thirds of senior IT executives have clicked on phishing links, and more than one in six never reported their mistake.
This isn’t just about individual errors—it’s a systemic problem that reveals dangerous vulnerabilities at the highest levels of organizational security. When those tasked with protecting the digital infrastructure become the weakest link, the consequences can be catastrophic.
The Alarming Statistics: IT Leaders Are Falling for Phishing
Arctic Wolf’s 2025 Human Risk Behavior Snapshot, which surveyed 1,700 IT leaders and employees, paints a concerning picture of cybersecurity vulnerability at the executive level:
IT Leadership Vulnerability by the Numbers
64% of senior IT executives have clicked on phishing links – Nearly two-thirds of those responsible for cybersecurity have fallen victim to the very attacks they’re supposed to prevent. This staggering figure challenges the assumption that technical expertise provides immunity to social engineering.
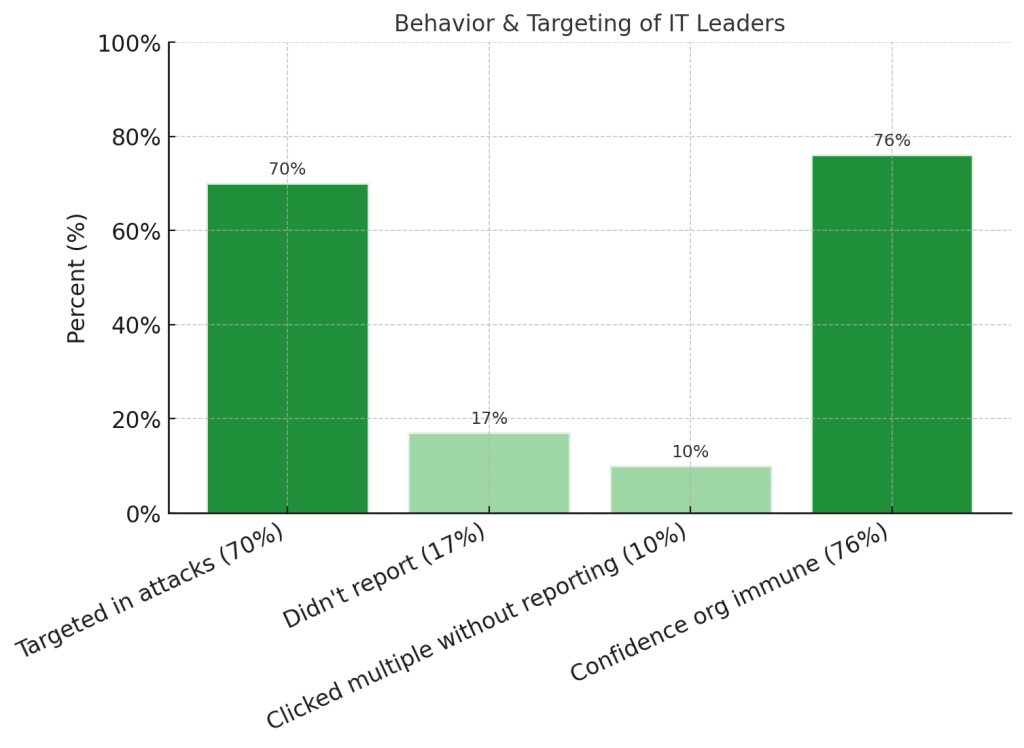
17% didn’t report clicking phishing links – One in six IT leaders who fell for phishing attacks kept it secret, creating a dangerous blind spot in organizational security. This silence prevents proper incident response and leaves potential breaches undetected.
10% have clicked multiple phishing links without reporting – Nearly one in ten IT leaders are repeat offenders who continue to hide their mistakes, compounding the risk to their organizations.
70% of IT leaders have been targeted in cyberattacks – The overwhelming majority of technical executives face active targeting, with sophisticated attackers recognizing that compromising leadership provides maximum impact.
The Confidence Paradox
Perhaps most alarming is the disconnect between reality and perception:
76% of IT leaders believe their organization wouldn’t fall for phishing – More than three-quarters express confidence that their organization is immune to phishing attacks, despite evidence showing that they themselves have fallen victim.
This dangerous overconfidence creates a false sense of security that leaves organizations vulnerable to attack. When leaders believe they’re safe while simultaneously falling for phishing scams, it signals a fundamental misunderstanding of the threat landscape.
Why IT Leaders Are Prime Targets
Understanding why IT executives click phishing links at such high rates requires examining both the sophistication of modern attacks and the unique vulnerabilities of leadership positions.
The Privilege Problem
IT leaders possess elevated privileges that make them extraordinarily valuable targets:
- Access to critical systems – Executives have administrative access to core infrastructure, databases, and security controls
- Financial authority – Many IT leaders can approve significant expenditures or wire transfers
- Strategic knowledge – They understand security architectures, making it easier for attackers to exploit specific weaknesses
- Trusted communications – Messages from IT leadership bypass skepticism, enabling lateral attacks
According to recent statistics, senior executives are 23% more likely to fall for AI-personalized phishing attacks compared to general employees. Attackers invest significant resources in researching and targeting high-value individuals, crafting messages that exploit their specific responsibilities and pressures.
The Pressure Cooker Effect
The modern IT leadership role creates conditions that increase phishing susceptibility:
Cognitive Overload IT leaders juggle countless responsibilities—strategic planning, vendor management, incident response, budget approvals, and staff oversight. Research shows that employees under tight deadlines are 3 times more likely to click phishing emails. IT executives operate under constant pressure, making them more likely to take shortcuts that bypass normal security scrutiny.
Email Volume Senior executives receive hundreds of emails daily. The sheer volume makes it impossible to scrutinize every message with the same level of attention. Attackers exploit this by timing phishing attempts to coincide with busy periods or known deadlines.
Authority Bias IT leaders regularly receive urgent requests from C-suite executives and board members. This creates a conditioning effect where responding quickly to leadership requests becomes automatic—exactly what phishing attacks exploit through Business Email Compromise (BEC) tactics.
Mobile Device Usage Executives frequently review emails on mobile devices while traveling or between meetings. Studies indicate mobile device users face 25-40% higher phishing success rates than desktop users due to smaller screens, abbreviated sender information, and reduced ability to hover over links to preview URLs.
The Sophistication of Modern Phishing
Today’s phishing attacks have evolved far beyond the obvious “Nigerian prince” scams:
AI-Powered Personalization Attackers leverage artificial intelligence to analyze social media profiles, LinkedIn activity, news articles, and public records to craft hyper-personalized messages. These attacks reference recent projects, ongoing initiatives, or personal interests to build credibility.
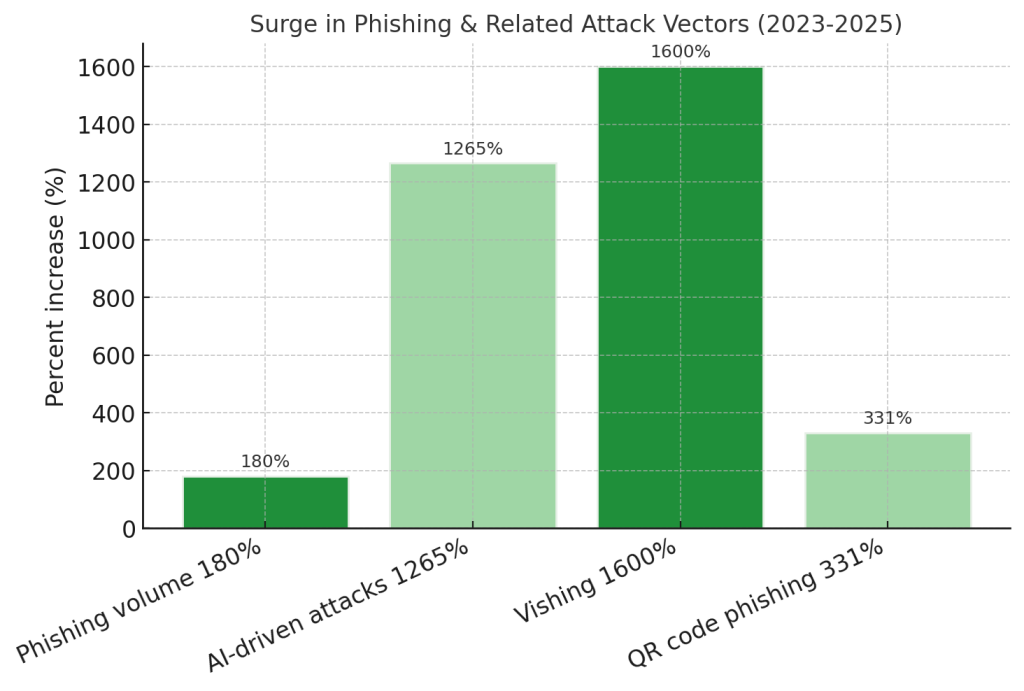
180% increase in phishing attack volume has been recorded in 2025 compared to 2023, with AI tools enabling attackers to scale personalized campaigns that previously required manual effort.
Deep Fake Technology Voice cloning and deepfake video are emerging as serious threats. Vishing (voice phishing) attacks spiked by over 1,600% in Q1 2025, with attackers using AI to replicate executives’ voices for fraudulent authorization calls.
Credential Harvesting Chains Modern attacks don’t just rely on single clicks. Attackers create multi-stage campaigns that progressively build trust before requesting sensitive actions. Initial contact might be benign, with subsequent messages referencing the previous exchange to establish legitimacy.
Around 80% of phishing campaigns aim to steal credentials, particularly targeting cloud services like Microsoft 365 and Google Workspace that IT leaders use extensively.
The Culture of Fear: Why IT Leaders Stay Silent
The fact that 17% of IT executives don’t report phishing clicks reveals a deeper organizational problem: a culture where admitting security mistakes carries professional consequences.
The Termination Threat
Arctic Wolf’s research suggests that fear of punishment or termination is driving the silence. Consider what’s at stake when an IT leader admits to clicking a phishing link:
- Damage to professional reputation and credibility
- Questioning of technical competence by peers and superiors
- Potential loss of authority over security decisions
- Performance review impacts and compensation consequences
- In severe cases, job termination or forced resignation
This creates a perverse incentive structure where covering up a potential security incident seems less risky than reporting it, despite the obvious organizational dangers.
The Trust Deficit
When IT leaders can’t admit mistakes without fear of severe consequences, organizations lose critical intelligence about:
- Attack vectors – Understanding how successful phishing works helps strengthen defenses
- Incident scope – Early reporting enables rapid response before attacks escalate
- Training effectiveness – Knowing what tricks even experts reveals where awareness training falls short
- Pattern recognition – Multiple reports might reveal coordinated campaigns targeting the organization
The “Expert Paradox”
IT leaders face unique pressure because they’re expected to be security experts. Admitting to falling for phishing feels like admitting incompetence in their core area of expertise. This creates a psychological barrier that lower-level employees don’t face—they can claim ignorance, but executives are supposed to “know better.”
Beyond IT Leadership: The Broader Phishing Landscape
While IT leaders’ vulnerability is shocking, they’re far from alone in facing sophisticated phishing attacks. Understanding the broader landscape provides context for this epidemic.
Phishing Attack Trends in 2025
Volume Explosion The frequency of phishing attacks has reached unprecedented levels:
- 4 billion phishing emails sent daily worldwide
- 84% increase in phishing attacks involving infostealers in 2024
- 45% of all ransomware attacks in Q1 2025 started with phishing
Financial Impact The cost of phishing continues to escalate:
- $4.88 million average cost per phishing breach in 2024, up 9.7% from 2023
- $2.77 billion in Business Email Compromise losses in 2024 alone
- $16.6 billion in total cybercrime losses with phishing accounting for a significant portion
Click-Through Rates Despite increased awareness, phishing remains devastatingly effective:
- 12-17.8% average click rate for general phishing campaigns
- 53.2% click rate for targeted spear phishing with phone follow-up
- 30% of phishing emails are opened by recipients
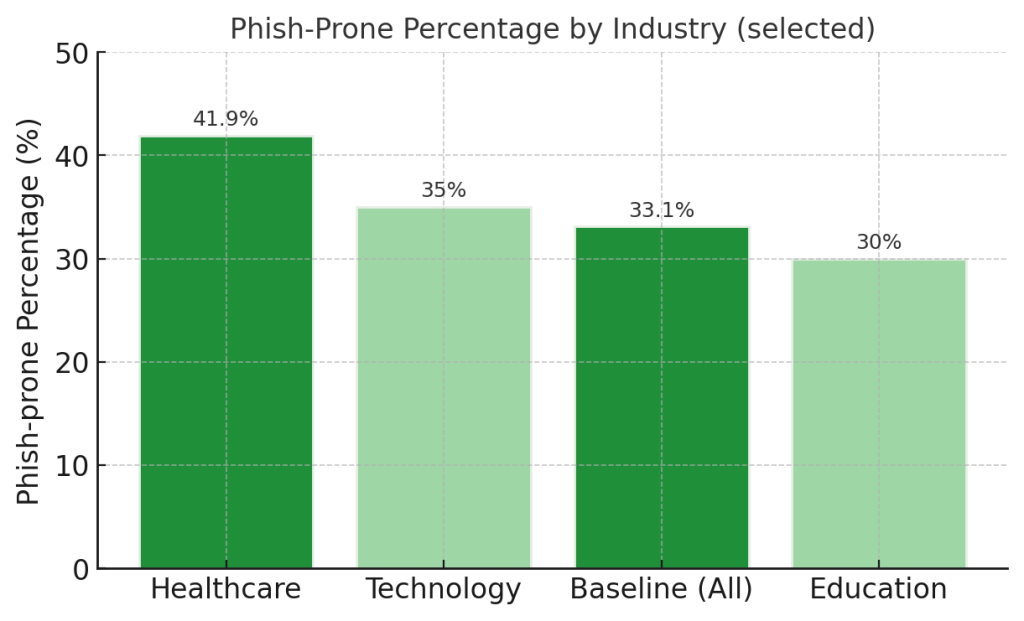
- 33.1% industry-wide baseline Phish-prone Percentage, meaning one-third of employees are susceptible
Industry-Specific Vulnerabilities
Different sectors face varying levels of phishing risk:
Healthcare: 41.9% Phish-prone Percentage – The highest click rate of any industry, making healthcare workers the most likely to fall for phishing attacks. The devastating Change Healthcare breach demonstrates the consequences.
Education: High click rates despite moderate targeting – Educational institutions see some of the highest phishing email click rates, though they’re not always the most targeted sector.
Financial Services: Most targeted sector – Despite better security awareness, financial institutions face the highest volume of phishing attempts due to direct access to money and valuable financial data.
Technology Companies: 35% report malware attacks – Tech firms face sophisticated attacks from nation-state actors and advanced persistent threat groups.
Evolving Attack Vectors
Phishing has expanded beyond email:
Quishing (QR Code Phishing): 331% year-over-year increase – Attackers exploit the perceived safety of QR codes to deliver malicious links, bypassing traditional email filters.
Vishing: 1,600% spike in Q1 2025 – Voice phishing now accounts for over 60% of phishing-related incidents handled by response teams.
Smishing (SMS Phishing) – Text-based attacks exploit the high trust users place in SMS notifications and the reduced security scrutiny on mobile devices.
Social Media Phishing – Attackers use direct messages on platforms like LinkedIn, Facebook, and Twitter to impersonate colleagues, HR departments, or support staff.
The AI Factor: Transforming Both Attack and Defense
Artificial intelligence is reshaping the phishing landscape in ways that directly impact IT leaders and their organizations.
AI Amplifies Phishing Threats
Automated Personalization at Scale AI tools enable attackers to research targets and craft personalized messages automatically. What previously required hours of manual work can now be accomplished in seconds, allowing attackers to send highly customized phishing at mass scale.
1,265% surge in AI-driven attacks has been observed as tools like ChatGPT become weaponized for creating convincing phishing content.
Language Perfection Traditional phishing emails were often identifiable by poor grammar and spelling. AI-generated content is grammatically perfect and contextually appropriate, eliminating this key detection signal.
Deepfake Technology Voice cloning and video deepfakes are becoming mainstream attack tools. IT leaders receiving what appears to be a video call from their CEO requesting urgent action face nearly impossible-to-detect deception.
The AI Data Leakage Problem
Arctic Wolf’s research uncovered another alarming trend: 60% of IT leaders have shared confidential information with AI systems like ChatGPT—a higher rate than the 41% of lower-level employees who did the same.
This creates multiple security risks:
Training Data Exposure Information entered into AI systems may be used for model training, potentially exposing sensitive business data to competitors or being inadvertently included in responses to other users.
Lack of Data Classification Many users don’t recognize when they’re sharing sensitive information, failing to distinguish between public knowledge and confidential data.
Shadow AI Usage 43% of employees weren’t sure if their organization had a generative AI policy, indicating a dangerous gap in governance and awareness training.
Organizations Worry But Lack Controls
The survey found significant concern about AI risks:
- 60% of organizations worry about AI tools leaking sensitive data
- 50% express concern about abuse of AI tools
However, policy implementation and communication lag behind concerns:
- Only 57% of lower-level workers say their organization has a generative AI policy
- 43% are unsure or believe no policy exists
This gap reveals inadequate communication and training around AI risks, leaving organizations vulnerable to data leakage and misuse.
Geographic Variations: Where Breaches Are Increasing
Arctic Wolf’s global data reveals interesting regional trends in security breaches:
Australia and New Zealand: Dramatic Surge
The Asia-Pacific region experienced the most significant deterioration:
- 78% of organizations reported breaches in 2025 (up from 56% in 2024)
- 22 percentage point increase year-over-year
- Potential factors include increased targeting of the region, rapid digital transformation, or improved detection and reporting
United States: Persistently High
The U.S. breach rate remained stable but worryingly high:
- Flat breach reporting rates between 2024 and 2025
- Suggests persistent vulnerability despite massive security investments
- Indicates attackers are successfully adapting to defensive improvements
Nordic Countries: Slight Improvement
Scandinavian nations saw marginal improvement:
- Modest decline in reported breaches
- May reflect strong security cultures, government support for cybersecurity, or effective public-private collaboration
Canada: Uptick in Incidents
Canadian organizations experienced increasing pressure:
- Slight increase in breach reporting
- Mirrors trends affecting close economic partner, the United States
Breaking the Silence: Creating a Culture of Reporting
To address the problem of unreported phishing clicks, organizations must fundamentally change how they handle security mistakes.
Psychological Safety is Security
No-Penalty Reporting Organizations should implement policies that guarantee no adverse consequences for promptly reporting security incidents, including phishing clicks. This requires executive commitment and cultural change, not just written policies.
Positive Reinforcement Rather than punishing reports, organizations should recognize and reward them. Employees who report potential phishing—even if they initially clicked—should be thanked for helping protect the organization.
“Near Miss” Framing Reframe phishing clicks as “near misses” that provide learning opportunities rather than failures. Aviation and healthcare industries have proven that this approach dramatically improves safety reporting.
Transparency From the Top
Leadership Vulnerability When executives openly discuss their own phishing encounters and near-misses, it normalizes reporting and reduces stigma. IT leaders should be encouraged to share their experiences in team meetings or company-wide communications.
Aggregate Reporting Regular sharing of anonymized phishing statistics helps employees understand that they’re not alone. Knowing that even senior executives click phishing links can reduce the shame that prevents reporting.
Structural Changes
Mandatory Reporting Periods Require all clicks on suspicious links to be reported within a specific timeframe (e.g., within 1 hour). Make this a neutral compliance requirement rather than an admission of wrongdoing.
Easy Reporting Mechanisms Implement one-click reporting buttons in email clients. The easier reporting becomes, the more likely people are to do it.
Incident Response Over Blame When phishing clicks are reported, focus entirely on incident response—password resets, system checks, threat hunting—rather than investigating who clicked and why.
Defense Strategies: Protecting Organizations From Phishing
Given the reality that even IT leaders fall for phishing, organizations need multi-layered defensive approaches.
Technical Controls
Email Security Enhancements
- Advanced email filtering with AI-powered threat detection
- DMARC, SPF, and DKIM authentication to prevent spoofing
- Suspicious link rewriting and sandbox analysis
- Banner warnings for external emails and suspicious content
Phishing-Resistant Multi-Factor Authentication Traditional SMS or authenticator app-based MFA can be bypassed through sophisticated phishing. Organizations should implement:
- FIDO2 hardware security keys
- Certificate-based authentication
- Biometric authentication tied to device hardware
These approaches prevent credential theft even when users enter passwords into phishing sites.
Zero Trust Architecture Assume breach and verify everything:
- Least-privilege access controls
- Continuous authentication and authorization
- Network segmentation to limit lateral movement
- Real-time monitoring for anomalous behavior
Human-Centered Security
Continuous Training Traditional annual security awareness training is insufficient. Organizations need:
- Quarterly or monthly micro-learning sessions (5-10 minutes)
- Just-in-time training triggered by suspicious behavior
- Role-specific training addressing unique risks faced by different positions
- Scenario-based simulations that test decision-making under pressure
Research shows organizations implementing strong security awareness programs see over 40% reduction in phishing risk within 90 days and up to 86% reduction within a year.
Realistic Phishing Simulations Regular testing with simulated phishing helps identify vulnerabilities:
- Use tactics that mirror current real-world attacks
- Avoid “gotcha” exercises that build resentment
- Follow simulations with immediate micro-training
- Track improvement over time, not just individual failures
- Include executive leadership in simulations
Red Flags Training Teach concrete indicators of phishing:
- Urgency and pressure tactics
- Requests for unusual actions outside normal procedures
- Slight misspellings in domain names or sender addresses
- Requests to bypass security procedures
- Generic greetings instead of personalized addressing
Process and Policy
Verification Procedures Establish protocols for verifying unusual requests:
- Callback verification for financial transactions or sensitive data requests
- Secondary approval for high-risk actions
- Out-of-band confirmation using a different communication channel
Incident Response Plans Detailed procedures for responding to suspected phishing:
- Clear escalation paths and responsible parties
- Timeline for password resets and access reviews
- Threat hunting procedures to identify compromise
- Communication templates for affected parties
AI Governance Given the findings about AI data leakage:
- Clear policies on what can and cannot be shared with AI tools
- Approved tools list with security reviews
- Data classification training to help employees recognize sensitive information
- Technical controls preventing copy-paste of sensitive data to AI interfaces
The Path Forward: Making Security Everyone’s Responsibility
The revelation that 64% of IT leaders have clicked phishing links should be a wake-up call for organizations everywhere. If those responsible for cybersecurity are vulnerable, everyone is.
Key Takeaways for Organizations
1. Abandon the Myth of Invulnerability No one is immune to phishing—not IT professionals, not executives, not security experts. Accepting this reality is the first step toward effective defense.
2. Build Reporting Into Security Culture The 17% of IT leaders who don’t report phishing clicks represent hidden incidents that could escalate into breaches. Organizations must create environments where reporting is expected, encouraged, and rewarded.
3. Layer Defenses Technical controls alone won’t stop phishing. Human training alone won’t stop phishing. Only comprehensive, layered approaches combining technology, training, and culture change provide adequate protection.
4. Address AI Risks Proactively With 60% of IT leaders sharing confidential information with AI tools, organizations need immediate action on AI governance, policies, and training.
5. Measure and Improve Regular assessment of phishing susceptibility through simulations, coupled with metrics on reporting rates and response times, enables continuous improvement.
Individual Responsibility
For IT leaders and all employees:
Slow Down Most phishing succeeds because of rushed decision-making. Taking 30 extra seconds to scrutinize a suspicious request can prevent disaster.
Verify Everything When a request seems unusual, even slightly, verify through a separate communication channel. Call the person, send a text, or walk to their office.
Report Immediately If you click something suspicious, report it immediately. Rapid reporting enables rapid response that can contain damage before it spreads.
Stay Educated Phishing tactics evolve constantly. Regular engagement with security training and awareness of current threats helps maintain vigilance.
The Bottom Line
Phishing has become the cybercriminals’ weapon of choice because it works—even against highly trained IT professionals. The statistics from Arctic Wolf’s research make this undeniable:
- Two-thirds of IT leaders have been compromised
- One in six hid their mistakes, creating dangerous blind spots
- Three-quarters maintain false confidence in their organization’s immunity
- AI is amplifying both attack sophistication and internal data leakage risks
The solution isn’t more blame or stricter punishment—that only drives mistakes underground where they can’t be addressed. The solution is creating security cultures where:
- Reporting is celebrated as responsible behavior
- Mistakes are treated as learning opportunities
- Defense is everyone’s responsibility, not just IT’s
- Technical controls work alongside human vigilance
The war against phishing cannot be won by IT departments alone, by technology alone, or by training alone. It requires organizational commitment to cultural change that values transparency over blame and collective security over individual perfection.
Your IT leaders are clicking phishing links. The question isn’t whether this will happen—it’s whether your organization has created an environment where they can report it, enabling you to respond before a click becomes a breach.
Is Your Organization Vulnerable to Phishing Attacks?
If two-thirds of IT leaders are clicking phishing links, how many of your employees are doing the same—and not reporting it? The statistics are clear: phishing is the #1 entry point for data breaches, ransomware, and financial fraud.
Don’t wait for a breach to discover your vulnerabilities.
Our Comprehensive Phishing Defense Services Include:
✓ Real-World Phishing Simulations – Test your team with current attack tactics, not outdated templates
✓ Customized Security Awareness Training – Role-specific education that addresses actual risks faced by your staff
✓ Phishing-Resistant Authentication – Implementation of FIDO2 and hardware security keys
✓ Email Security Hardening – Advanced filtering, authentication, and threat detection
✓ Culture Change Consulting – Build a reporting-positive environment that encourages transparency
✓ Incident Response Planning – Prepare for when phishing succeeds, not if
✓ Executive Security Briefings – Help leadership understand their unique vulnerabilities
Special Focus: IT Leadership Protection
Given the alarming vulnerability of IT executives, we offer specialized services:
- Executive-targeted simulation campaigns
- Leadership vulnerability assessments
- Confidential coaching for building secure habits
- C-suite security awareness programs
[Get Your Free Phishing Risk Assessment] | [Schedule Executive Security Consultation]
Protect your organization from the #1 cyber threat. Contact us today to learn how we can help build a phishing-resistant security culture.