This article synthesizes current reporting and vendor analysis, explains how these attacks work, gives hard numbers and sources for the load-bearing facts, and provides a practical, prioritized mitigation playbook for ops, security, and web teams.
Recent months have seen two worrying but related developments in the web threat landscape: high-impact vulnerabilities in popular WordPress themes that allow site takeover and a rise in stealth delivery techniques—most notably cache-smuggling variants of ClickFix/FileFix social-engineering attacks—that let attackers deliver malware in ways that avoid traditional detection. Together these trends raise the risk profile for any organization that relies on WordPress or embeds third-party components on public-facing properties.
What happened — summary of the incidents
Two types of activity are driving immediate concern:
1) Critical theme vulnerabilities being actively exploited. A critical flaw in a well-known WordPress theme (“Alone” / charity multipurpose theme) allowed unauthenticated attackers to upload archives that contained backdoors, enabling remote code execution and full site takeover in thousands of attempts observed by defenders. Security telemetry showed exploitation began prior to public disclosure and that defenders blocked more than 120,000 exploitation attempts related to this flaw. This vulnerability (high-severity, CVSS ~9.8) was patched by the vendor, but many sites remained vulnerable for weeks.
2) Cache-smuggling and ClickFix/FileFix-style delivery tactics. A newer wave of attacks has been observed where malicious actors craft social-engineering lures (often masquerading as compliance checks or benign utilities) that cause victims to retrieve files that look like images or other harmless content. Once on a host, these artifacts are unpacked or executed via staged commands (e.g., PowerShell), allowing a payload to run despite endpoint protections. Security vendors have described this “cache-smuggling” approach as effective because it bypasses ordinary download detection heuristics and leverages trusted content delivery paths for stealth.
Why these two trends are linked: theme vulnerabilities provide the initial foothold for site compromise and hosting of malicious lures or command-and-control assets; cache-smuggling improves delivery success and helps payloads evade detection once they reach targets.
How the attacks work (technical overview)
Below are concise, non-exhaustive outlines of the two attack chains defenders are seeing in the wild.
A. Theme-based site takeover (example pattern)
- Vulnerability discovery — an unauthenticated file-upload or plugin-install function lacks proper capability checks.
- Weaponization — attacker crafts a ZIP archive or plugin package containing a web shell or backdoor.
- Exploit — the attacker submits the package via the vulnerable endpoint (often via AJAX) and achieves code execution.
- Persistence & expansion — attacker writes web shells, creates stealth admin users, or installs scheduled tasks and rogue plugins.
- Abuse — compromised sites serve phishing pages, host C2 infrastructure, redirect visitors, or act as distribution points. Security firms recorded large numbers of automated attempts against the Alone theme and similar components.
B. Cache-smuggling + ClickFix/FileFix delivery (social-engineering + stealth)
- Lure — phishing or social-engineering messages encourage an action (e.g., “run this check” or “download this file to confirm”).
- Stealth download — the payload is delivered in a file type that appears benign (image/jpeg) and routed through CDNs or compromised websites to reduce usual detection triggers.
- Extraction & execution — a local script or command extracts a hidden payload from the benign wrapper and runs it (PowerShell on Windows, shell scripts on *nix).
- Post-compromise — attackers move laterally, install backdoors, or exfiltrate credentials. Researchers emphasize that cache-smuggling reduces the noise of obvious download events, which historically alerted detection systems.

Load-bearing facts and numbers (what the data says)
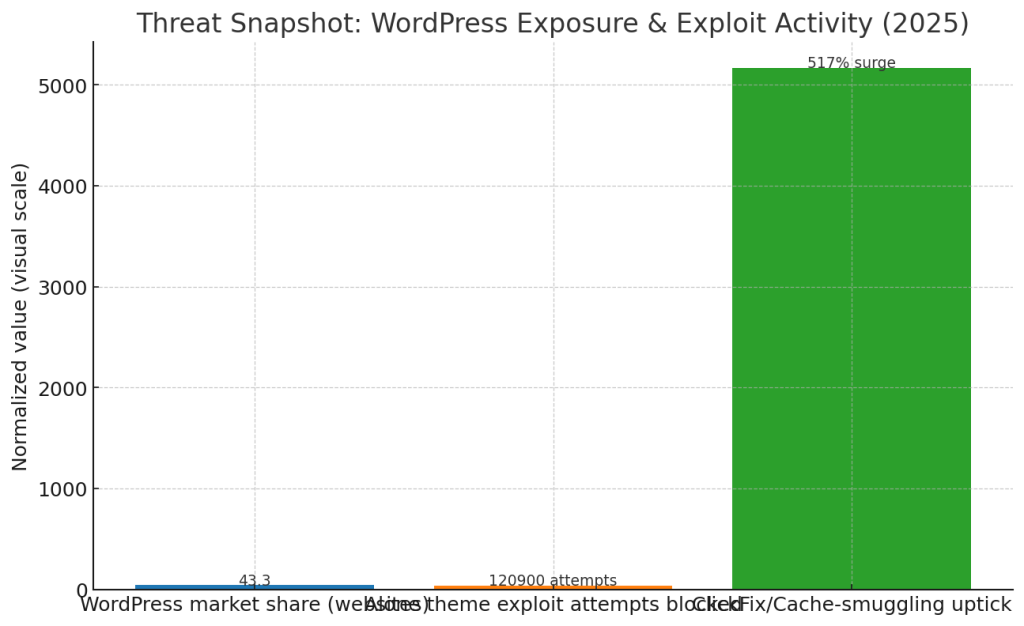
- WordPress prevalence: WordPress continues to power a large share of the web: roughly 43% of all websites run on WordPress, and WordPress dominates the CMS market (over 60% among sites that use a known CMS). That scale makes WordPress a high-reward target.
- Exploit telemetry: For the Alone theme flaw, security firm telemetry recorded more than 120,000 blocked exploit attempts during the active period, highlighting both the scale of scanning activity and the speed at which attackers weaponize disclosed bugs.
- Cache-smuggling/ClickFix trend: Variants of ClickFix/FileFix social-engineering grew sharply during 2025, with multiple security groups documenting surges (hundreds of percent increases in observed campaigns), and recent campaigns using cache-smuggling to evade detection were documented by multiple vendors. Expect these techniques to spread across campaigns.
Those figures show the combined effect of reach (WordPress market share), opportunistic scanning (automated attempts), and evolving delivery techniques.
Who’s most at risk
- Small-to-medium sites using commercial themes or many plugins — often updated infrequently and managed by small teams.
- Nonprofit and charity sites that use a common “multipurpose” theme with many demos and bundled components. Those themes often include import tools and plugin installers that expand the attack surface.
- Organizations with poor monitoring or no runtime protection — attacks that rely on cache smuggling and staged execution are specifically designed to slip past detection stacks without noisy download events.
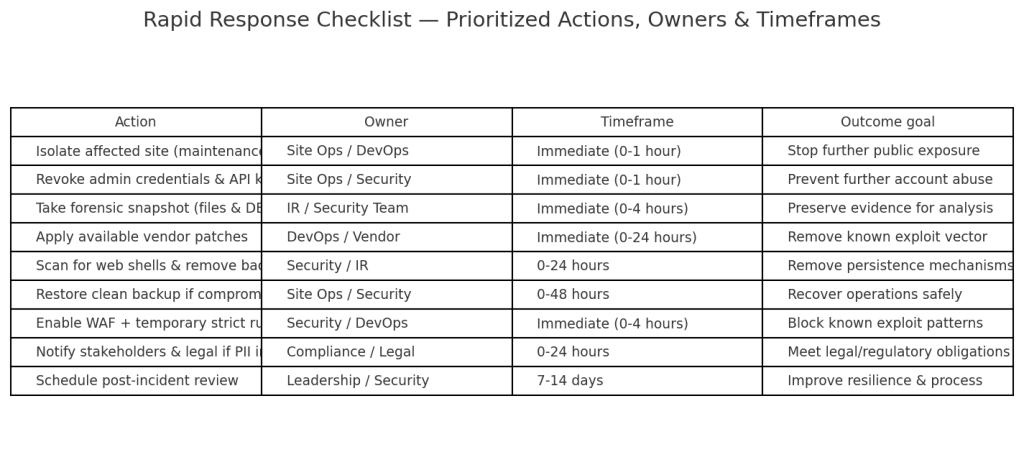
Practical mitigation — prioritized playbook
Here is a prioritized checklist you can implement now. The weightings reflect what will most rapidly reduce risk.
Immediate (hours–days)
- Patch everything (WordPress core, themes, plugins) — apply vendor updates and verify version numbers. For known critical theme advisories, update to the vendor-fixed release immediately.
- Remove unused themes/plugins — uninstall anything not actively used to shrink the attack surface.
- Lock down uploads — forbid execution in upload directories, implement server-side MIME checks, and block dangerous file extensions.
- Isolate admin interfaces — restrict wp-admin to allowlisted IPs or via VPN where possible.
Near term (days–weeks)
- Deploy WAF & runtime protection — use a web application firewall to block exploitation patterns and consider RASP for higher-risk sites.
- Enable file integrity monitoring (FIM) — detect unexpected file changes and new PHP files in content directories.
- Harden permissions and remove backdoors — scan for web shells, hidden admin users, and unauthorized plugins.
Operational (weeks–months)
- Monitor for social-engineering lures — train staff to resist ClickFix/FileFix messages and build playbooks for suspected incidents.
- Backups & restore drills — maintain immutable backups and test restores regularly.
- Threat-hunting & log retention — keep access and webserver logs for a meaningful window (90 days+) and run indicators for suspicious POSTs and new admin creations.
Detection & incident response tips
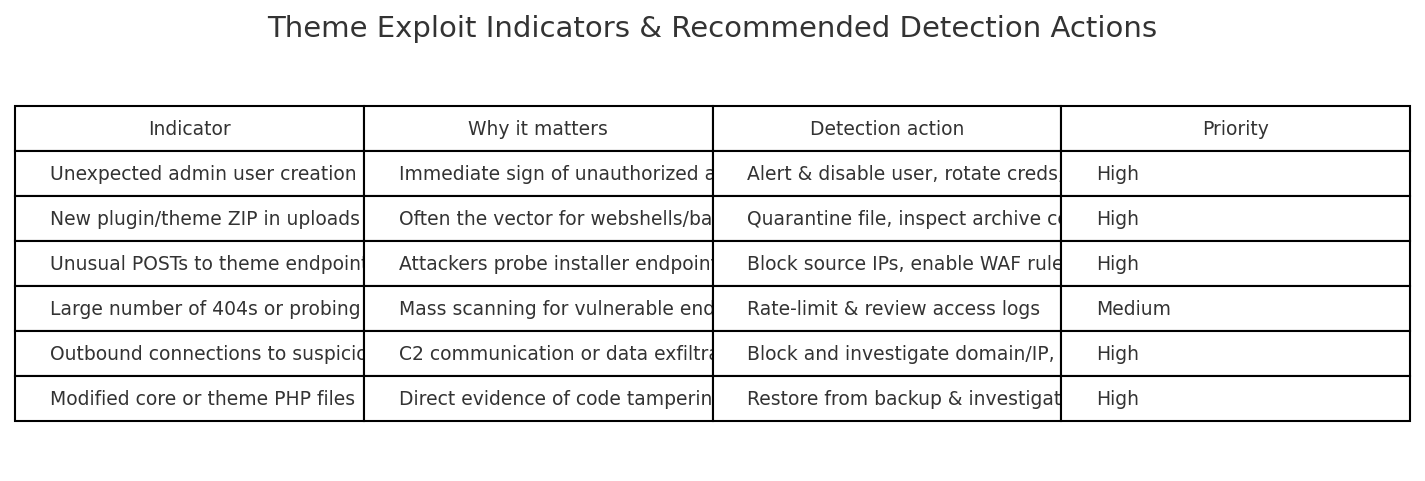
- Watch for anomalous admin creations and plugin installs. The easiest signal of a theme-based compromise is unexpected new admin users or plugin ZIPs appearing in uploads.
- Monitor outbound connections from webservers. Compromised sites often call home; unusual domains or IPs indicate C2.
- Run scheduled FIM scans and automate alerts. Trigger immediate containment actions (disable site, revoke creds) on detection of web shells.
- Use sandbox detonation for suspicious downloads. If an asset looks like an image but has suspicious metadata, detonate in an isolated environment. This counters cache-smuggling’s attempt to mask payloads within otherwise benign files.
Prognosis: what to expect next (3–12 months)
- More theme/plugin exploits, faster weaponization. Given WordPress’ reach and the ubiquity of third-party components, expect more critical theme/plugin bugs to be discovered and exploited quickly, often before many sites apply patches. Automated scanners will continue to probe widely within hours of disclosures.
- Stealth delivery techniques become standard. Cache-smuggling and similar evasion strategies will be refined and integrated into broader phishing and supply-chain campaigns. Detection tools must adapt to inspect content streams and not only file types.
- Rise of managed WordPress security and vertical defenders. Demand for managed hosting with proactive security (auto-patching, WAF, backups, RASP) will increase; security vendors offering targeted detection for social-engineering plus runtime protection will gain traction.
- Regulatory & procurement pressure. Organizations with public-facing sites in regulated sectors will face more pressure to demonstrate SLAs for patching and third-party component vetting; procurement processes will begin to include security checklists for themes/plugins.
Overall: attackers will iterate quickly, defenders must make fundamental posture changes (patching, hardening, RASP/WAF, and monitoring) to keep pace.
Quick executive summary (for leadership)
- WordPress theme vulnerabilities and novel delivery techniques are converging into a high-impact threat: site takeover + stealthy payload delivery.
- Immediate actions (patch, remove unused code, harden uploads, enable WAF) drastically reduce risk.
- Invest in runtime detection, backup resilience, and user training to counter ClickFix/FileFix-style social-engineering.
- Expect continued attack volume; treat WordPress ecosystems and third-party components as critical infrastructure.