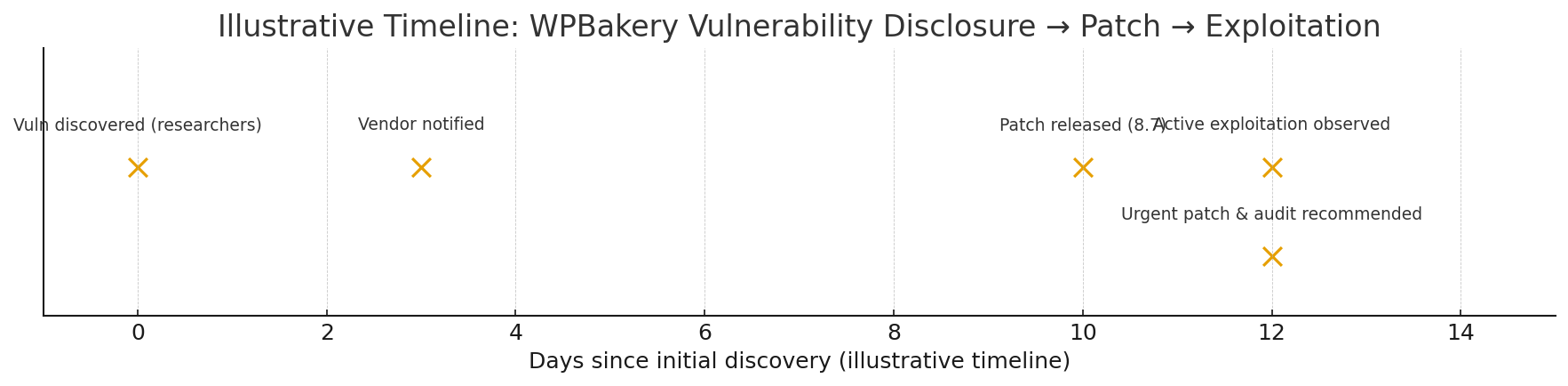
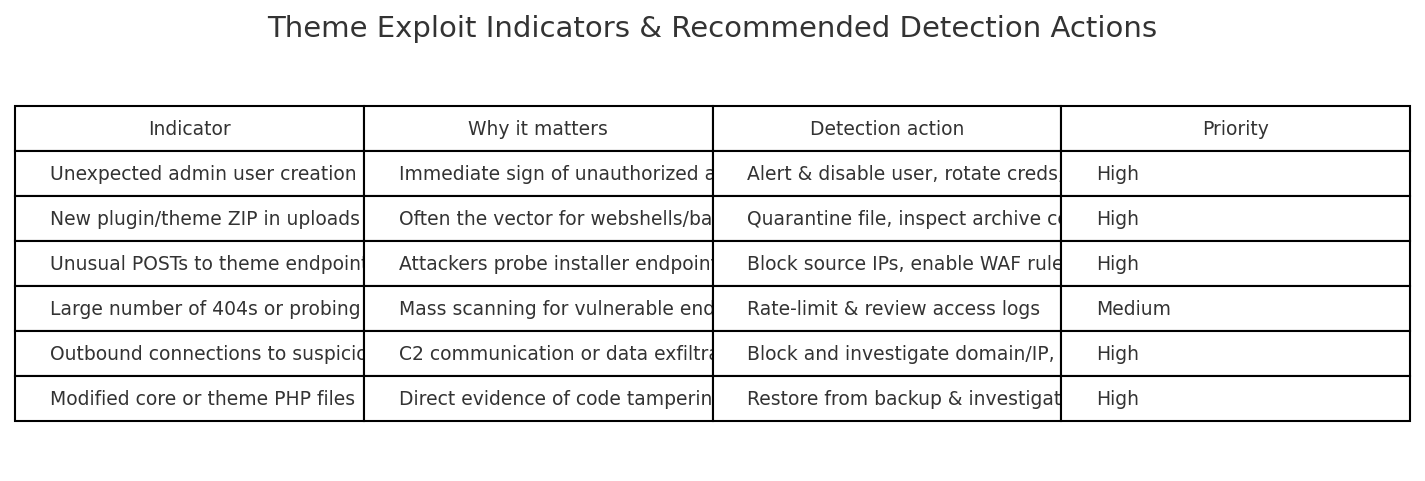
A stored cross-site scripting (XSS) flaw in WPBakery Page Builder’s Custom JS feature was disclosed; attackers with low-level authenticated access can persist JavaScript that executes when higher-privilege users view the page. Update WPBakery to the patched version immediately and follow the hardening steps below.
Read More