A sophisticated new malware campaign is targeting WordPress sites with an ingenious obfuscation technique that’s proving difficult to detect—and it’s already hit over 30,000 sites in a single month.
Read More

A sophisticated new malware campaign is targeting WordPress sites with an ingenious obfuscation technique that’s proving difficult to detect—and it’s already hit over 30,000 sites in a single month.
Read More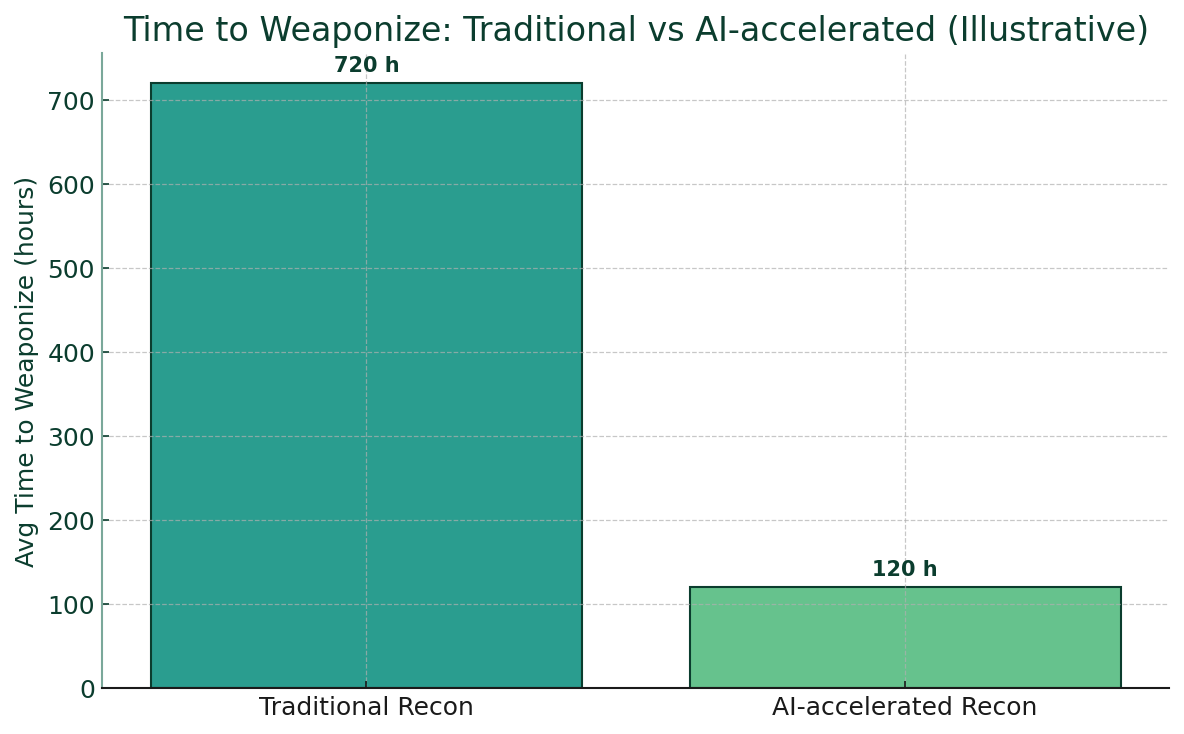
A sophisticated threat group is exploiting blockchain smart contracts to create nearly undetectable malware distribution systems, compromising thousands of WordPress websites in the process.
Read More
WordPress powers over 43% of all websites on the internet—that’s roughly 533 million sites. This massive popularity makes it the number one target for cybercriminals worldwide. If you’re running a WordPress site, you’re facing a harsh reality: your site faces approximately 30,000 hacking attempts every single day, with at least 13,000 of those specifically targeting WordPress installations.
Read More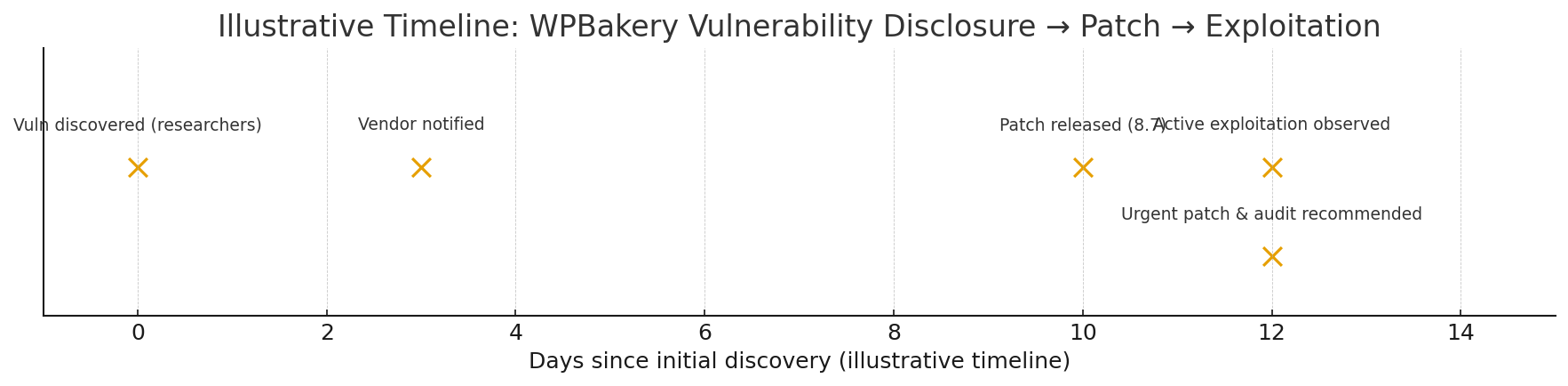
A stored cross-site scripting (XSS) flaw in WPBakery Page Builder’s Custom JS feature was disclosed; attackers with low-level authenticated access can persist JavaScript that executes when higher-privilege users view the page. Update WPBakery to the patched version immediately and follow the hardening steps below.
Read More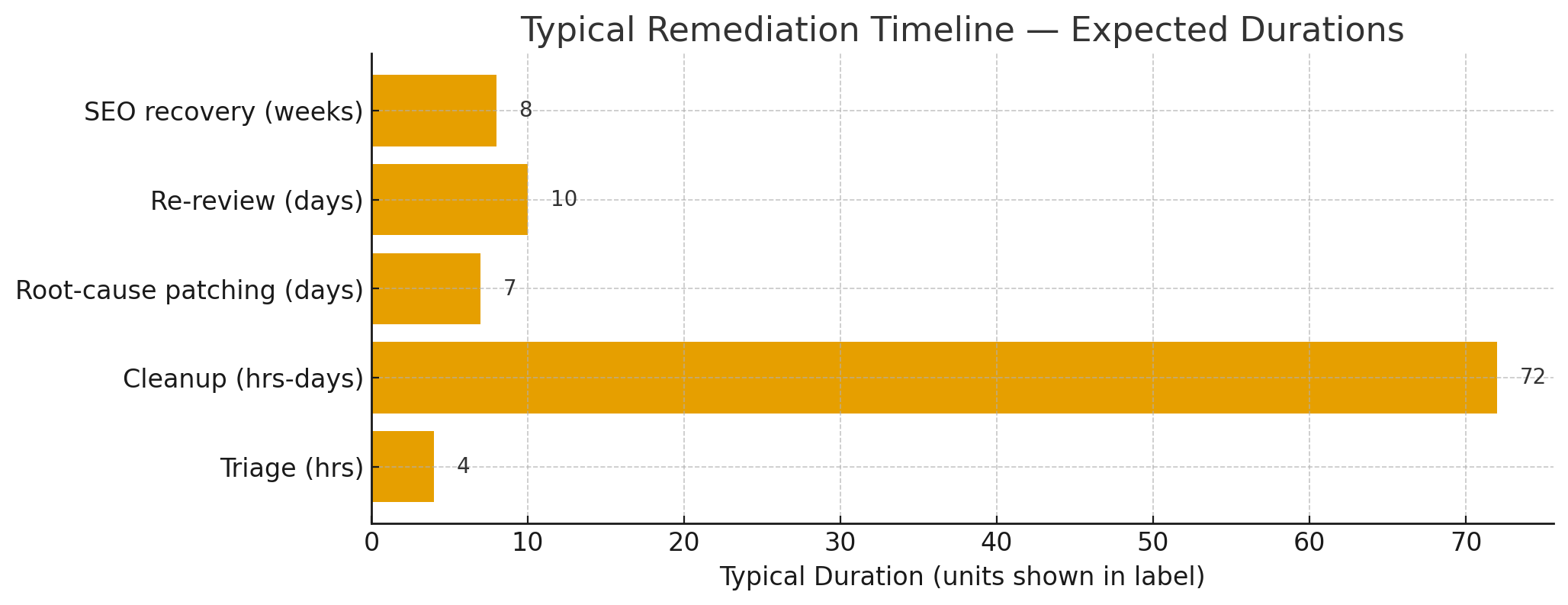
A critical authentication-bypass vulnerability in the Service Finder “Bookings” plugin/theme (affecting versions up to 6.0) allows unauthenticated attackers to take over accounts — including administrator accounts — on vulnerable WordPress sites. Multiple security researchers and vendors have confirmed active exploitation in the wild. If your site uses the Service Finder theme or bundled Bookings plugin, update to the fixed release immediately (or remove the plugin) and follow the emergency checklist below.
Read More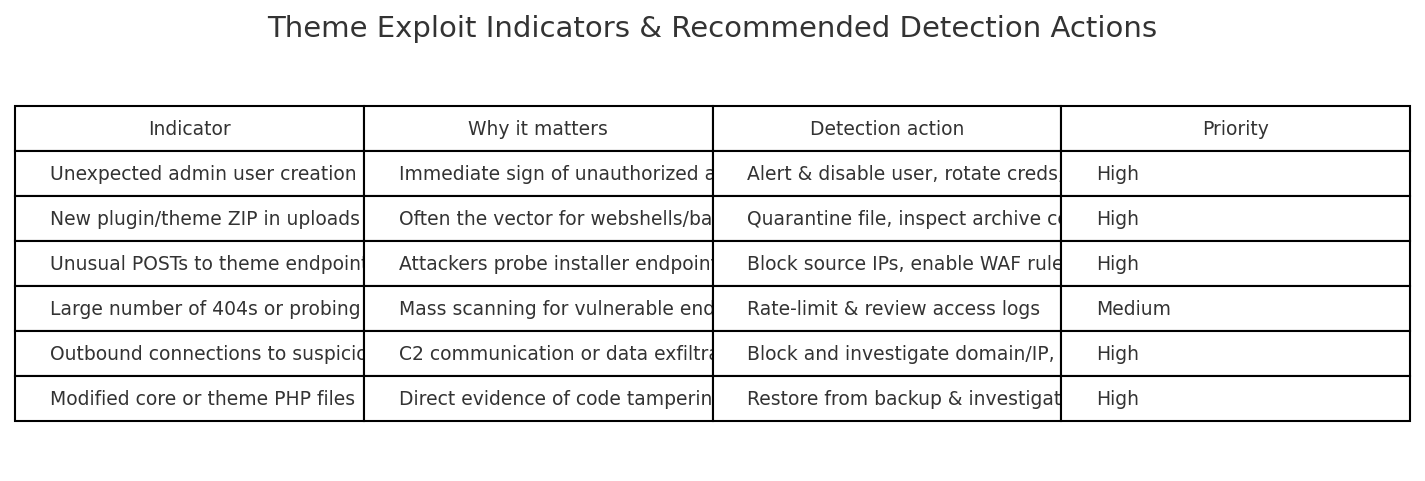
This article synthesizes current reporting and vendor analysis, explains how these attacks work, gives hard numbers and sources for the load-bearing facts, and provides a practical, prioritized mitigation playbook for ops, security, and web teams.
Read More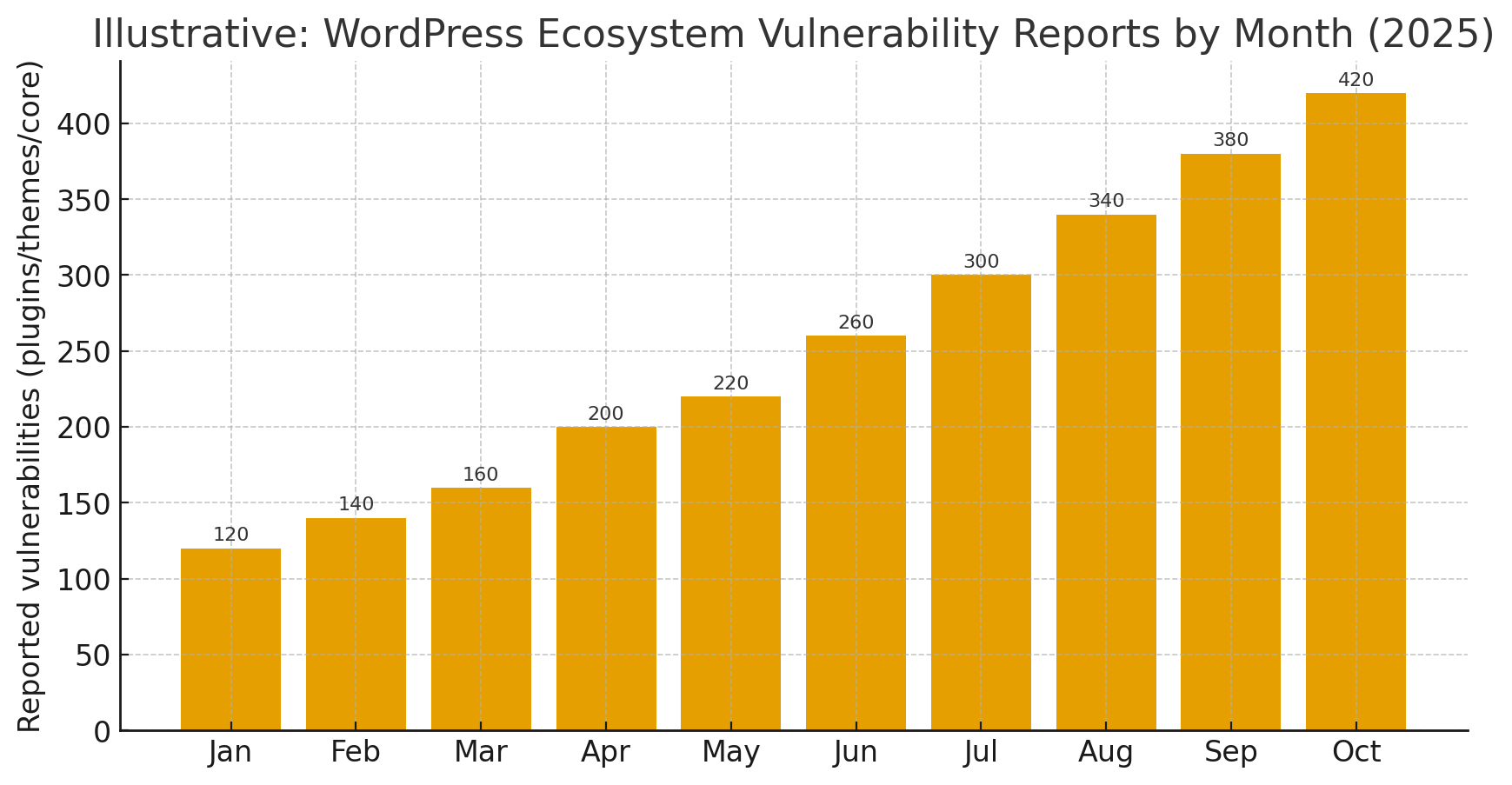
In 2025 the WordPress ecosystem continued to produce a large number of security disclosures, with third-party plugins and themes remaining the dominant source of high-impact vulnerabilities. Attackers quickly weaponized several unauthenticated remote code execution, arbitrary file upload and broken-access-control flaws, and exploit campaigns often began within days of disclosure. Industry mitigations such as virtual patching (WAF rules) and vendor “rapid mitigate” systems played a major role in reducing live exploitation while site owners applied official patches. If you manage WordPress sites, the priority remains the same: maintain an accurate inventory; patch high-risk components immediately; remove unused extensions; and combine short-term virtual patches with longer-term hardening and monitoring.

As more businesses, organizations, and individuals create websites to enhance their online presence, the importance of website security has never been more critical. Content Management Systems (CMS) are the backbone of most websites today, providing a user-friendly platform for managing and publishing content. However, with the rise of cybercrime and increasingly sophisticated attacks, it’s essential to choose a CMS that offers the highest level of security. In this article, we will examine the security features, vulnerabilities, and best practices of three of the most popular CMS platforms—WordPress, Drupal, and Joomla—based on the most recent data and security statistics.
Magento is still the most popular ecommerce platform. It’s known as the most trusted platform with a high functionality and customizability level. WordPress is considered the fastest growing CMS currently. Initially, it’s referred to blogs because its main functionality is aimed at easy blog keeping. By the way, its developers have succeeded in turning it into the perfectly well content management system.
Many have seen reports that another site was hacked. Perhaps someone personally came across this. How can a site be hacked, and what protection measures can be taken? We will talk about what needs to be done to protect your site and not become a victim of hackers.