Every webmaster at one point or another has to face the fact of their website being hacked. If you haven’t had this kind of problem yet, then you’ve either been using a custom CMS or have just recently started working with sites. In this article, we will go point by point to easily explain what you need to do if your site has been hacked or if malicious code has been inserted into your site.
Relax, it’s not that bad
First of all, you shouldn’t panic or do anything rash. Webmasters frequently turn to immediately restore a backup copy of their site and thereby lose the content that they’ve posted over the preceding days. There’s nothing wrong with doing this, except for one “but”: the site is restored, but the backdoor through which the site was hacked isn’t closed. This means that it is only a matter of time until your site will be hacked again and you’ll have to face the same problem all over again.
There is no need to panic and make rash decisions, you just need to get out of the situation with minimal losses and act so as to ensure that your site will be an impregnable fortress to hackers in the future.
Contact your hosting provider
First and foremost, find out from your hosting provider whether your site could have been hacked because of a server vulnerability. If you use regular hosting and not a dedicated server, then it is by all means possible that the hacking was the fault of your hosting neighbor. In other words, the hacker gained access to one of the client sites on the same server as yours, and thereby gained administrative rights to the whole server. When a hacker gets administrative rights, they can install a virus on any website on the whole server.
Find out from your hosting provider whether the server has software that lets you scan your site for malicious code. Many hosting providers buy antivirus protection for their servers from us so that their clients can check their sites for viruses for free. But in most cases things are still a little different: most of hosting providers either do not use antivirus software at all, or use free versions which are very ineffective.
Tell your hosting provider that you are aware of the virus and are already working on getting rid of it. This is necessary because many hosts, upon seeing a virus on a client site, simply block and disconnect the site from their network. As a result, you might lose clients and search engine positions while your site is unavailable.
Ask your hosting provider if their administrators can help you delete the virus from your site. It is possible that your hosting seller offers such a service which you just don’t know about.
Restore an earlier version of your site
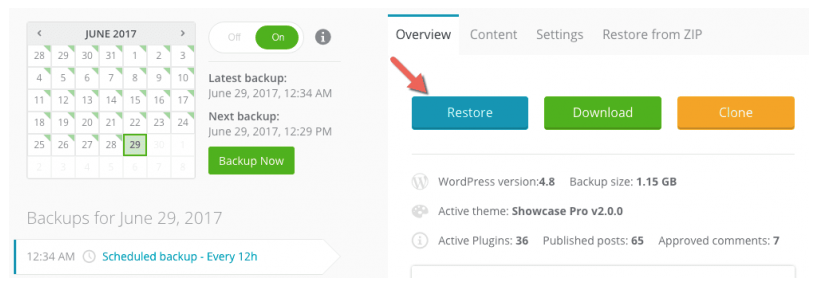
If you have backed up your site at least once a week, then it should be no problem for you to simply restore a copy of the site from before it had malware injected. This is the easiest way to eliminate a virus and then install additional site protection.
Check your work computer for viruses
According to our statistics, 20% of site hacks occur due to negligence towards the security of one’s work PC or employees’ computers. If you use Windows at your workplace, be sure to install a firewall (WAF – Web Application Firewall) and antivirus. Check your computer and employees’ computers for viruses, and then consider transferring your employees working on the site to Linux or Unix OS.
Change passwords
The most cunning hackers know that as soon as you detect a hack and unauthorized access to your site, the first thing you’ll do is change all your passwords. So they create additional users within the site administration, and sometimes inside the cPanel. Make sure that you do not have new administrators and FTP accounts, and if you do find them, simply delete them.
Templates, modules, and plugins
Go to the administrative section of your CMS and view the installed modules. Delete all the ones you don’t need. Attention!: Don’t simply deactivate them, but delete them from the hosting so that these modules’ files aren’t on your server. Check to see if the plugins you need are updated to the latest versions. If you haven’t updated them in a while, be sure to check with the developer what the latest version is and update them. A lot of Magento Extension Development companies warn you if your website has extensions that are not up to date.
Do the same with your templates. If you only use one version of a template on the site, then delete all the unneeded ones and update the ones you need to their latest version.
Google Webmaster (Search Console)
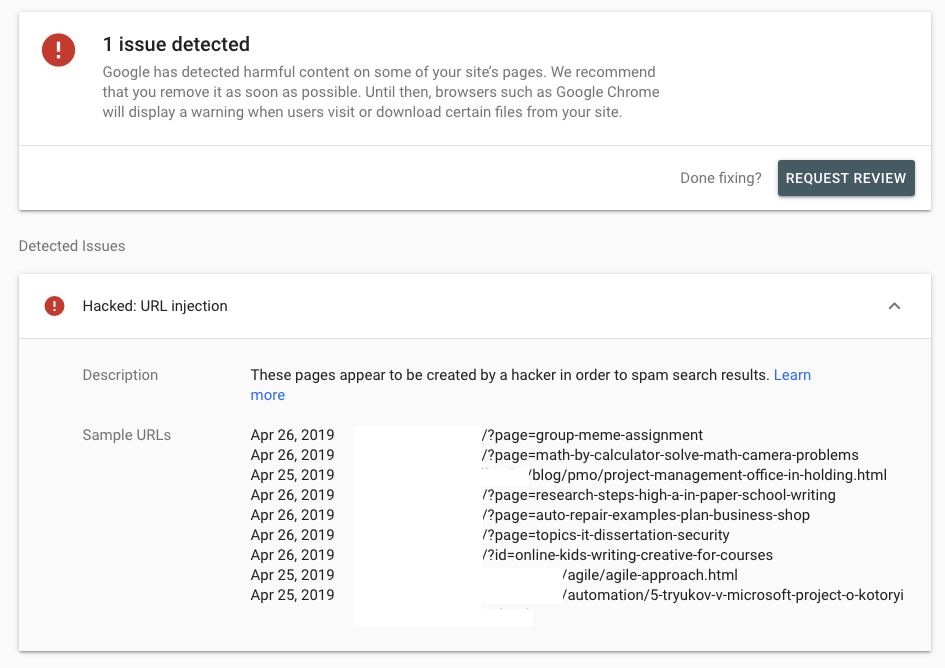
If you still haven’t installed Google Search Console, then be sure to do so. Check if there aren’t any notifications for you. Both Google and MSN generally send notifications when their algorithms detect a virus on sites. If you have notifications, be sure to contact both after you delete the viruses. Then, submit a request to review your site.
Indexed Pages
Open Google and type in the search bar site:site_name.com. View all the pages in the MSN and Google indexes. If you find any unknown pages, send a request to have them removed through Google or MSN Webmaster.
To quickly block spam pages, you can use the file robots.txt which can be found in the root folder of your site and is available at the address of your_site.com/robots.txt. Open the file in any of your favorite text editors and add the following lines for all robots:
Disallow: /spam.php
Disallow: /hacked/malware.html
Disallow: /malware_folder/
Naturally, instead of the above pages, you should specify the pages you found in the search results.
Here is an example of Japanese spam which is installed on hacked user sites:
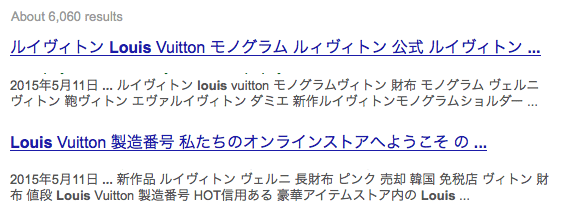
Find and eliminate viruses on the site
It should be added that simply deleting a malicious code is not enough. You need to find out how your site was hacked and where the vulnerability is on your site, so as to protect yourself from future hacks. Let us draw your attention to the fact that if you have more than one site on a hosting, you need to check all of them for viruses and vulnerabilities. If an attacker gained access to one of your sites, it is likely that a malicious code can also be found hidden in any of the others.
Conclusion
It doesn’t matter which CMS you use or what traffic your site has, you should always devote time to the security of your resources. Ensuring site security is just as complicated and difficult work as is building or promoting a site in search systems. It takes time and energy, but modern reality is such that if you don’t dedicate enough time to securing your server, you will most likely lose time searching for and deleting viruses and restoring sites following a hack.
Check Your Website For Malware
Scan Your Website Absolutely Free, No Registration Required