
Critical Security Alert: Over 250 Magento Stores Compromised in 24 Hours Through Adobe Commerce Vulnerability
A coordinated cyberattack has successfully compromised more than 250 Adobe Commerce and Magento Open Source e-commerce stores within a 24-hour period, exploiting a recently disclosed critical vulnerability. E-commerce security firm Sansec has issued an urgent warning as threat actors actively leverage CVE-2025-54236, also known as “SessionReaper,” to hijack customer accounts and deploy malicious backdoors across vulnerable platforms.
Read More
Critical Security Incident: Xubuntu Website Hijacked to Deploy Crypto-Stealing Malware
On October 18, 2025, the official Xubuntu website experienced a significant security breach that transformed legitimate download links into malware distribution channels. Attackers replaced torrent files with a malicious Windows executable designed to steal cryptocurrency through clipboard hijacking. This incident represents a concerning trend in supply chain attacks targeting open-source software communities, particularly during a period when users are migrating from end-of-life Windows 10 systems.
Read More
The Rising Threat of ClickFix Attacks: Why Copy-Paste Malware Is Breaking Through Traditional Defenses
A new attack technique is quietly becoming one of the most prevalent cybersecurity threats of 2025. Known as ClickFix, FileFix, or fake CAPTCHA attacks, this social engineering method has seen explosive growth, with some studies reporting increases of up to 517% in just six months. Major organizations including Kettering Health, DaVita, and the City of St. Paul have all fallen victim to these increasingly sophisticated attacks.
Read More
Detecting and Removing PHP Webshells: Tools, Indicators & Real Case Studies
Compromised PHP sites often hide webshells – small scripts that give attackers remote command execution, file management, database access, and persistence. This guide walks you through how webshells stick around, IOCs to scan for, concrete commands/YARA patterns to detect them, and a step-by-step cleanup methodology you can follow (or hand to your incident responder).
Read More
The Small Business Guide to Affordable Managed Website Security
If you run a small business, your website is your storefront, sales rep, and support desk rolled into one. Keeping it safe matters—but should you DIY security or pay for a managed service? This guide compares both approaches, outlines clear pricing tiers, shows what’s included (monitoring, backups, WAF, patching), and runs the numbers on ROI so you can choose confidently.
Read More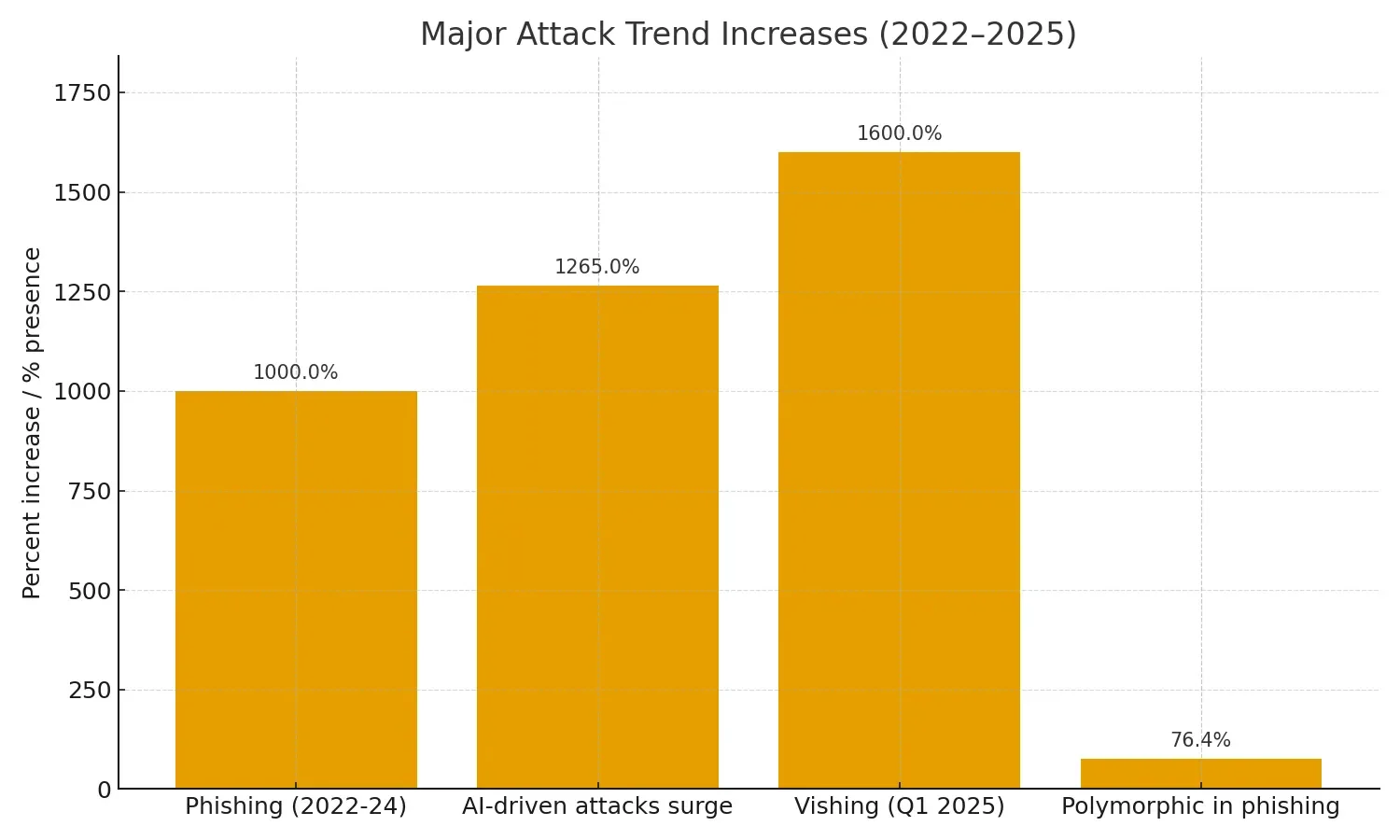
How AI is Transforming Both Cyber Attacks and Website Defense in 2025
The cybersecurity landscape of 2025 has become an arms race where artificial intelligence serves as both weapon and shield. As organizations scramble to defend their digital assets, they face an uncomfortable reality: the same AI technology powering their defense systems is being weaponized by cybercriminals to launch unprecedented attacks.
Read More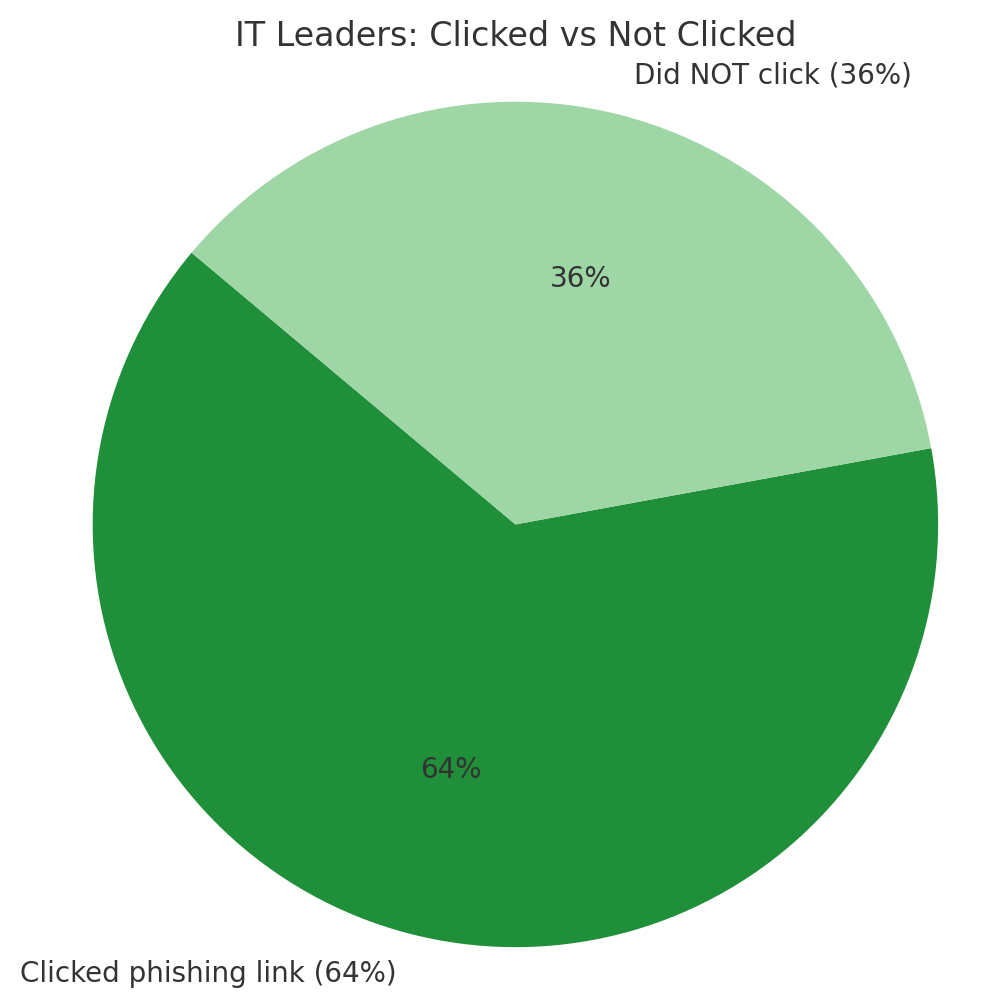
Shocking Reality: Two-Thirds of IT Leaders Click Phishing Links—And Many Never Report It
New research reveals a disturbing truth: the very people responsible for cybersecurity are falling victim to phishing attacks at alarming rates—and a culture of fear is preventing many from reporting their mistakes.
Read More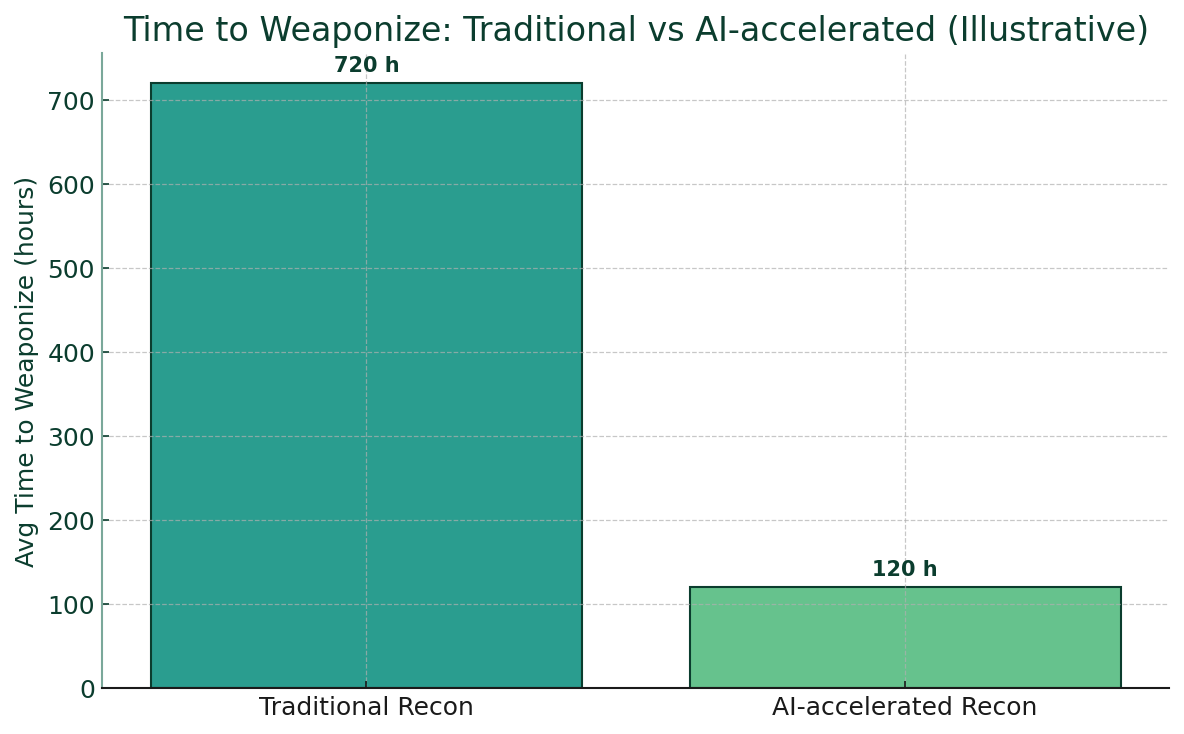
Cybercriminals Weaponize Blockchain Technology to Hide Malware Distribution Networks
A sophisticated threat group is exploiting blockchain smart contracts to create nearly undetectable malware distribution systems, compromising thousands of WordPress websites in the process.
Read More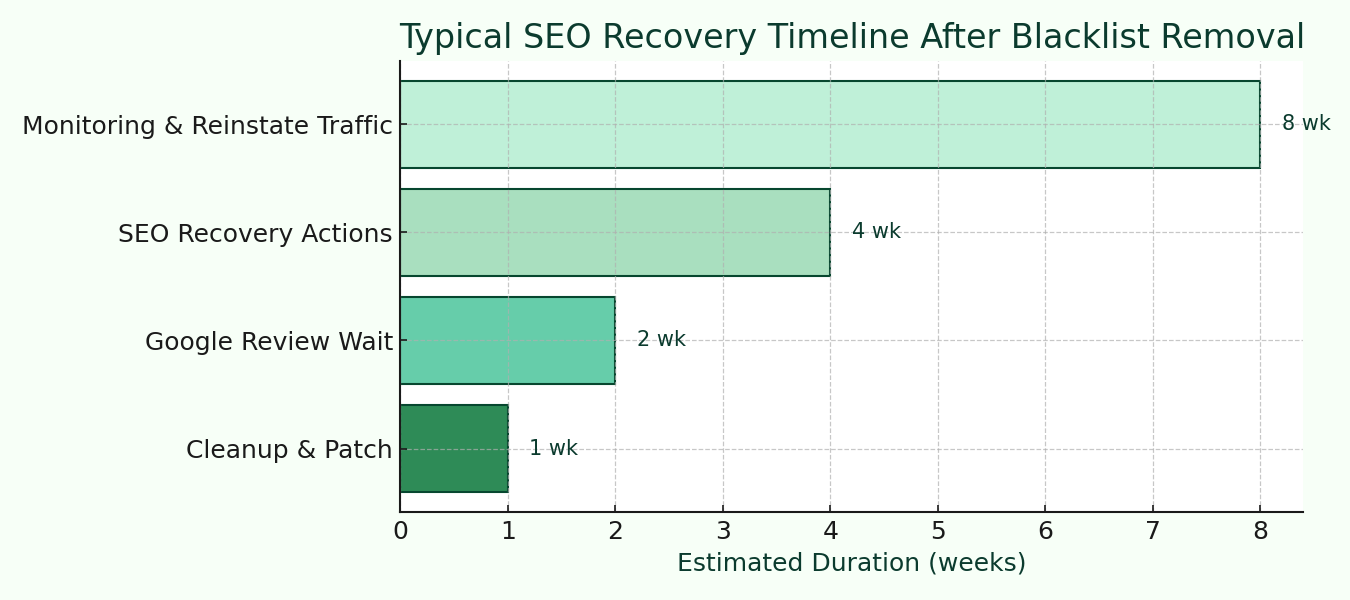
Why Google Blacklisted Your Site (and How to Get It Removed Fast)
Discovering that Google has blacklisted your website is every business owner’s nightmare. One moment your site is generating traffic and leads, the next it’s flagged with a terrifying red warning screen that scares away visitors and tanks your search rankings overnight.
Read More